A report by researchers at Heimdal Security points to the detection of a phishing campaign targeting Office 365 users and administrators that could put the security of an entire business environment at risk. As some users may recall, phishing is an attack variant in which an unauthorized user tries to gain access to a system by posing as a legitimate user or company, mainly employing the image of a well-known company.
In this campaign, the threat actors employ a very convincing and legitimate-looking message, in addition to employing websites similar to those of Office 365 and SharePoint, seeking that victims enter their credentials of access to these malicious platforms.
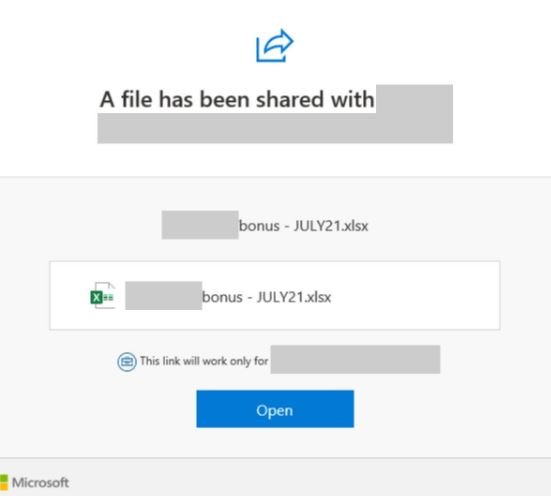
Hackers use the Microsoft SharePoint name to trick victims into clicking on a link attached to the email. The malicious content is disguised as a request for “shared files”, supposedly related to the internal work in the affected organization.
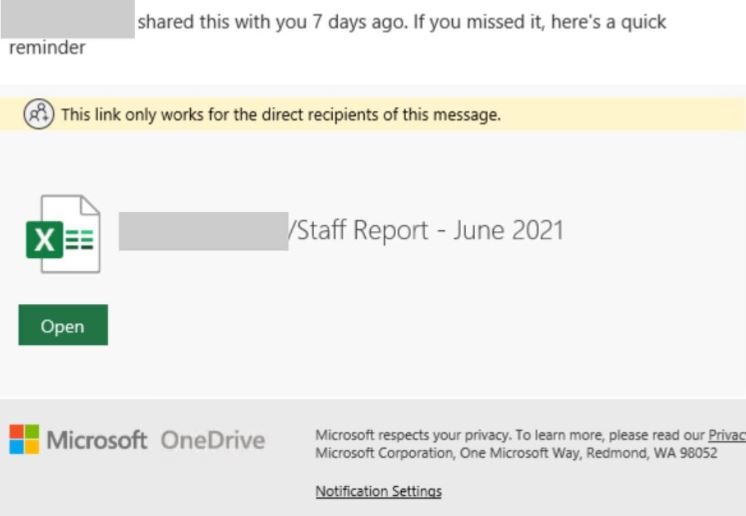
As can be seen in the screenshots, threat actors use Microsoft logos at all times to give these messages a legitimate appearance.
After closely looking at the source URL, experts detected that it was based on a Google storage platform that redirects victims to the AppSpot domain of Google App Engine.
Heimdal’s report mentions: “The emails contain two URLs with malformed HTTP headers. The primary phishing URL is a Google storage resource that points to an AppSpot domain where the user will be prompted to sign in before being redirected to another domain that pretends to be the official Office 365 website.”
Moreover, the second URL is attached in the claims configuration and is designed to redirect the target user to a compromised SharePoint website. It is worth mentioning that the two malicious URLs require the user to enter their login credentials to complete the attack, as this way cybercriminals will be able to evade the most popular email security filters used nowadays.
For security reasons, Office 365 users are encouraged to ignore any email sent by unknown users or that includes unsolicited attachments and links. Also, before entering your access codes always remember to check the validity of the URL in question.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











