An Iran-based hacking group has spent about a year and a half operating a hacking campaign in which they pose as aerobics instructors in order to spy on and infect defense employees and contractors and aerospace agencies with malware trying to steal sensitive information.
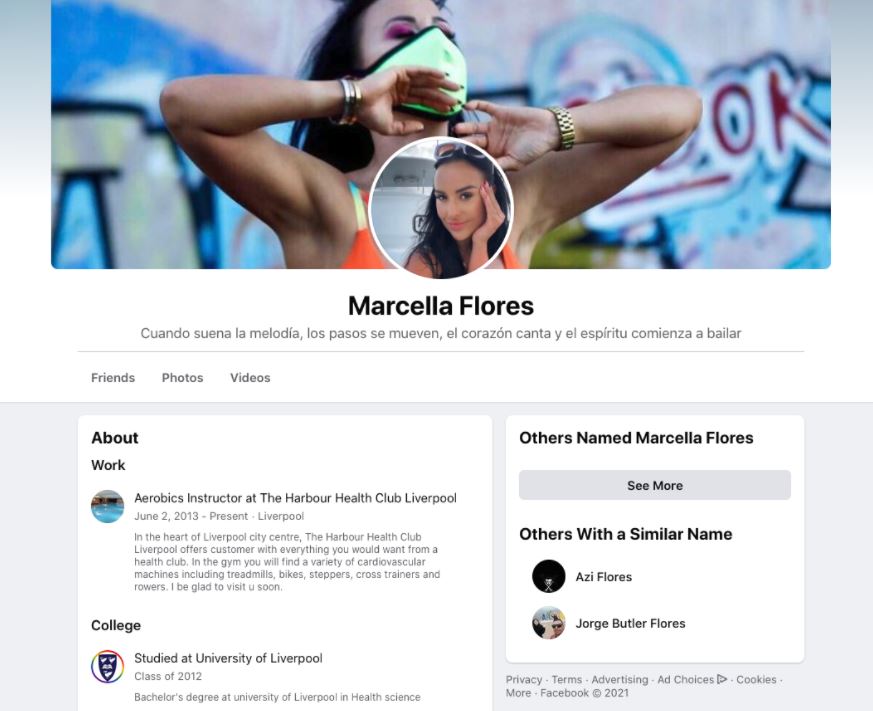
According to Proofpoint specialists, the operators of this campaign created a fake profile allegedly controlled by aerobics instructor “Marcella Flores”, using platforms such as Facebook, Instagram and email servers to deceive affected users. Attackers use these fake profiles to trick users and distribute malware with relative ease.
Experts have attributed this campaign to the hacking group identified as TA456 or Tortoiseshell, a hacking group sponsored by the government of Iran and very close to the Islamic Revolutionary Guard Corps (IRGC).
In the social media profiles created by the threat actors, Marcella Flores is announced as an expert aerobics instructor who resides in the English city of Liverpool and has a long list of supposed friends, professional contacts and clients. Hackers use Marcella Flores’ profiles to search for people of interest on these platforms, offering their supposed services as a personal trainer, requesting to respond to a feeding survey and even flirting with affected users.
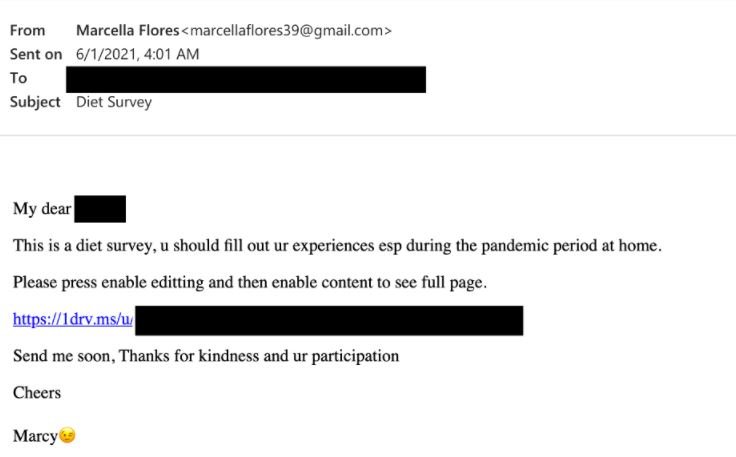
After gaining the trust of affected users, attackers use a personal Gmail account to send an OneDrive link where personal documents are allegedly hosted; actually, this platform hosts a file uploaded with a new version of the Lideric malware, also known as Lempo. This malware generates persistence in Windows systems and then begins to search for and steal sensitive information such as usernames and login credentials, which are sent to a server controlled by hackers.
The compromised information would allow threat actors to gain remote access to VPN and remote management platforms, which could enable the deployment of ambitious cyber espionage campaigns and sophisticated phishing attacks. After receiving a report about it, Facebook removed Marcella Flores’ profiles on its various platforms, in addition to publishing a security alert related to this hacking campaign.
This is a clear demonstration of the sophistication with which threat actors can operate, creating a comprehensive infrastructure for the deployment of ambitious social engineering and phishing campaigns. Users should try to avoid making contact with an unknown account on social media, especially if they are employees or managers at government contracting companies.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











