A recent report from Check Point Research (CPR) points to the detection of a new malware variant designed to infect Windows and macOS devices. This malware was identified as XLoader and is for sale for a considerably low price given its advanced capabilities.
This is actually a variant of the Formbook malware, which was previously sold on dark web forums on a subscription of $29 USD a week. About five years ago this malware was removed from the black market by its developer, known as ng-Coder, who remained inactive until the appearance of XLoader.
Researchers have been analyzing this malware since its appearance in early 2021, which allowed them to discover that XLoader contains the same code base as Formbook albeit with some notable changes, including the ability to infect macOS systems.
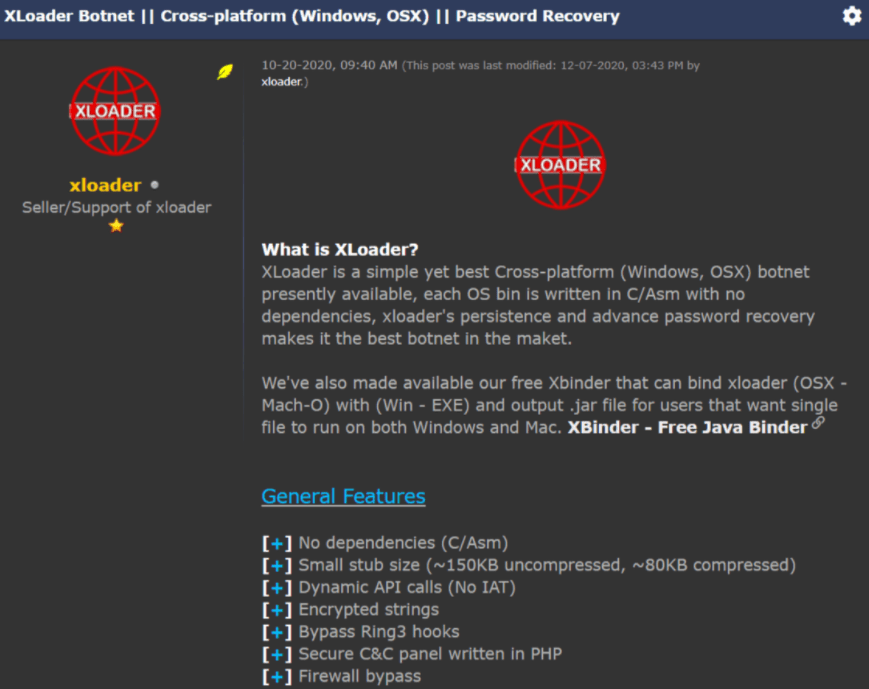
Like many other malware variants, XLoader attacks begin with a phishing campaign that aims to send a malicious attachment, usually Microsoft Word documents loaded with the malware. Once installed on the target system, this malware is able to monitor keystrokes, take screenshots and extract sensitive data.
The malware also has an extensive C&C configuration, using almost 90,000 domains for its network communications. Experts mention that, of these 90,000 domains, approximately 88, belong to legitimate websites to which malware sends malicious traffic to disorient researchers: “There is a problem when trying to determine which are the C&C providers controlled by hackers,” the report mentions.
XLoader is available on dark web forums for prices between $59 USD and $129 USD. The price varies depending on the subscription time and the type of target system.
The Check Point report concludes by mentioning that XLoader-related incidents have been identified in at least 70 countries, all linked to a centralized C&C server. The main focus of activity of this malware is the United States, with more than half of the cases detected in this territory. Experts also claim to have found a link between ng-Coder and xloader, a very active user in the forums where this tool is sold, although reports mention that this is just a seller of the malware.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











