Cybersecurity experts reported the detection of at least four flaws in Dell SupportAsist’s BIOSConnect feature, the exploitation of which would allow threat actors to deploy remote code to affected devices. It should be noted that this software is preinstalled by default on most Dell computers running Windows systems, and BIOSConnect allows remote firmware update and some operating system recovery features.
This set of flaws received a score of 8.3/10 on the Common Vulnerability Scoring System (CVSS) scale, and its exploitation would allow privileged remote hackers on the target system to impersonate an official Dell service in order to take control of the operating system boot process and thus break any security controls enabled. So far no active exploitation attempts or a functional attack have been detected for the abuse of these flaws.
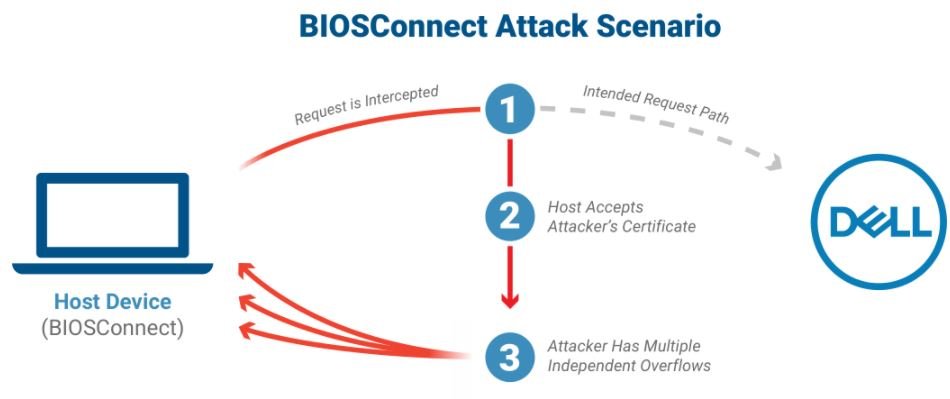
The report was presented by security firm Eclypsium, whose researchers say the problem lies in at least 129 Dell devices, including desktops, laptops and electronic tablets used by nearly 130 million users worldwide.
The flaws were described as an insecure TLS connection from BIOS to Dell (CVE-2021-21571) and three overflow errors (identified as CVE-2021-21572, CVE-2021-21573, and CVE-2021-21574). All vulnerabilities are independent and their exploitation would allow multiple risk scenarios, including the execution of arbitrary code in BIOS.
For security reasons, Eclypsium experts recommend users update the BIOS/UEFI of affected systems, as well as employ an alternative method to BIOSConnect for the installation of updates released by Dell. A detailed report on these findings is available on the company’s official platforms.
While CVE-2021-21573 and CVE-2021-21574 do not require users to take additional actions, the remaining flaws necessarily require the installation of updates for Dell ClientBIOS to mitigate the risk of exploitation.
Finally, it is recommended that users who are unable to update their systems soon can disable BIOSConnect from the BIOS setup page or by using Dell Command | Configure, the remote system administration tool.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











