A group of hackers claims to have compromised the systems of Electronic Arts (EA), one of the most important video game development companies, which allowed them to steal around 750 GB of confidential information including source code of some games and their debugging tools.
In a message shared with some members of the cybersecurity community, the company confirmed the incident, ruling out that it is a ransomware infection: “The attackers accessed a limited amount of related code and tools; we rule out this impacting the user experience.”
Moreover, an investigator contacted an alleged threat actor, who is now selling EA data, including what he claims is the complete source code of the latest edition of FIFA, plus points used as currency in the game. It is important to mention that these points can sometimes be used as a method of money laundering.
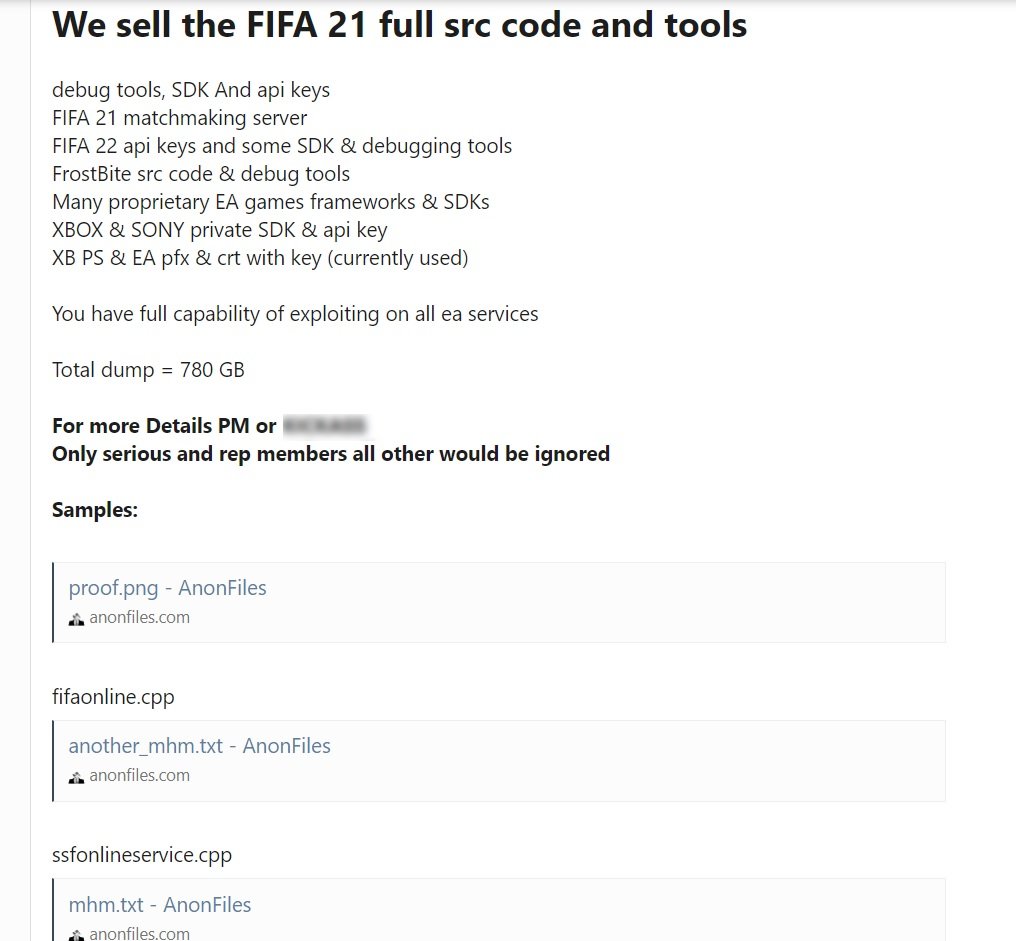
The attackers claim to have access to all of EA’s services, and say that a customer willing to pay $28 million USD for the stolen data will also get full exploitability on all EA services.
Threat actors claim to have the source code and debugging tools for the following video games:
- FrostBite
- FIFA 21 and FIFA 22
- Xbox and SONY private SDK and API key
- XB PS and EA pPFX
The hackers shared some screenshots showing directory listings and source code to prove the legitimacy of this leak.
Despite the seriousness of the incident, the company assures that users will not be affected in any way: “Player data was not accessed and we have no reason to believe that there is any risk to player privacy. After the incident we implemented security enhancements and did not expect subsequent attacks. We are actively working with law enforcement agencies and external cybersecurity specialists to ensure this does not happen again.”
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











