Browsing the Tor network is easier than many might think, although sometimes it is better to restrict access to this kind of resource. In working environments, for example, it will always be desirable for there to be measures against the use of private networks or for them to provide anonymity services.
On this occasion, cybersecurity experts from the International Institute of Cyber Security (IICS) will show you how to block access to the Tor network, as well as some methods that help bypass these measures.
As usual, we remind you that this article was prepared for informational purposes only, so IICS is not responsible for the misuse that may be given to the information contained herein.
How does Tor blocking work?
Cybersecurity specialists mention that there are 4 main methods to restrict access to Tor.
Directory restriction: This is the simplest method. There are a total of nine public directories of input nodes to Tor; when you close access to these directories, users will not be able to connect to the anonymous network.
List of relay nodes: According to cybersecurity experts, network administrators can download a list of around 7 thousand relay nodes (responsible for redirecting traffic) to block them by their IP address.
Fingerprints: This is a very unreliable method; it consists of tracking the fingerprints that are characteristic of certain packages. Based on these logs it is possible to configure traffic filtering to limit access to Tor. This method is widely used in cyberwarfare campaigns.
Software blocking: The last method is to block the access and execution of the resources needed to connect to the Tor network, cutting off any possible attempt to use the anonymous network.
Cybersecurity experts mention that the combination of these four methods can show excellent results, although of course the developers of Tor did not stand idly by watching as security agencies and companies blocked access to this network.
How to bypass access restrictions to Tor?
Using Tor bridges
The use of bridges is the main method of circumventing these restrictions. Everything starts from the premise that any user can get a complete list of relay nodes that exist in order to block them, this led to the need to create bridges whose address list is not publicly known.
To connect to Tor over a bridge, we must go to the site https://bridges.Torproject.org, select the type of transport and indicate if the network supports IPv6. Then we will have to solve a CAPTCHA, obtain the address of the bridge and then specify it in the configuration of the Tor browser. Security experts mention that it is also possible to request the bridge address from The Tor Project (Torproject.org) website during the setup of a connection.
If you are blocked, you can send an email with no subject to bridges@Torproject.org by typing a line in the body of the get transport obfs4 message (send this message only from Gmail or Riseup). In response, an automated program will send you the bridge address to evade the access restriction.
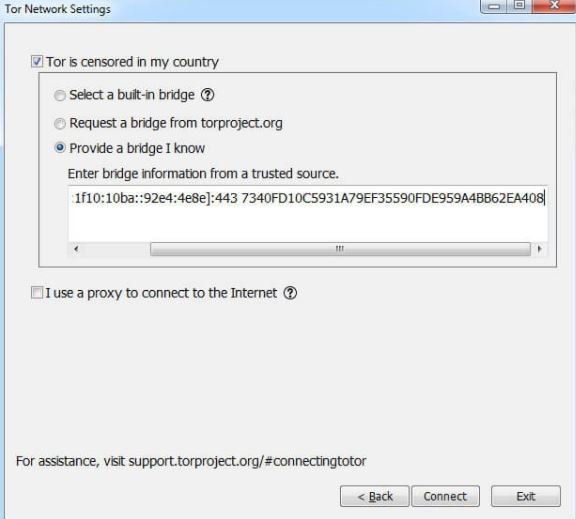
Cybersecurity experts mention that these Tor bridges use the SOCKS Proxy interface and are similar in architecture to the Shadowsocks project, used to evade the so-called Great Firewall of China. Tor bridges act as obfuscators that mask traffic on the Tor network, making it look like normal HTTP or a random byte stream, making the filtering process difficult.
The popularity of this method quickly caught the attention of many government agencies, which learned to block these connections using deep traffic analysis tactics and tools. Upon detecting a “suspicious” node, the government host tries to connect to it through the Tor protocol. If a host supports this protocol and responds that it is a bridge, it is immediately blocked and its IP address is blacklisted.
It is a fact that, with the necessary resources, the government can block the available bridges in a given region, also blocking any subsequent attempts, so the bridge method has limited functionality.
Meek
Tor has another pluggable transport called Meek, which can be activated if the bridges are blocked. It also works similar to that of a proxy, but cloud servers from Amazon, Google, CloudFront, Content Delivery Network (CDN), or Microsoft Azure are used as an intermediate link for the transmission of traffic.
The expectation is that in governments and organizations that monitor the Tor network will never completely block CDN, Amazon, Azure or other similar services, since these clouds use a lot of internet resources and any restrictions would impact their performance. In some cases, however, more restrictive governments could tear down half the national segment of the network in search of a single potentially risky messenger that has not been blocked.
Connecting to Meek is very simple: when you start the Tor browser, you need to click the Configure button, select the censor checkbox, and then, by placing the switch in the Select an integrated bridge position and select the Meek transport from the drop-down list
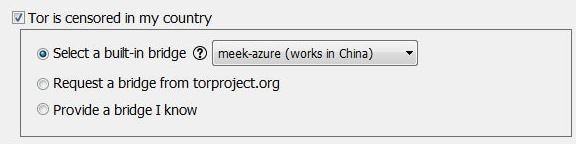
According to cybersecurity experts, Meek uses a technique called “domain fronting”. To connect to the target host, Meek client generates special HTTPS requests and sends them to an unlocked “external” service, such as CDN. This “external” name appears in the DNS request and data used by the SNI protocol.
The actual host name to which the client needs to connect is hidden in the HTTP host header. An intermediate cloud service determines this name and forwards the request to the Meek server running on one of the Tor bridges. In turn, Meek decrypts the request body and forwards it to the Tor network to finally reach the end user. In addition to the default configuration with Azure, users can set their own Meek transport parameters, although less experienced users might require help configuring it correctly.
Snowflake
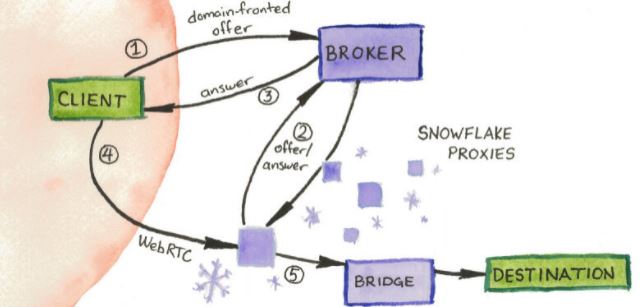
For users less familiar with the concepts stated above, those responsible for The Tor Project created a JavaScript browser extension called Snowflake. Simply install this plugin to start running a Tor bridge that will run directly from the web browser.
This has proven to be an efficient method as no organization in the world could block the use of all web browsers. Other techniques such as deep data analysis wouldn’t work either, as Snowflake is based on webrtc technology, which employ dozens of legitimate software tools such as Google Hangouts and video conferencing platforms; for obvious reasons it is impossible to block webrtc.
Tor’s developers try to give constant maintenance and receive feedback from the users of this project, cybersecurity experts mention. Other online anti-censorship efforts such as Open ObservaTory for Network Interference also support the proper functioning of Snowflake.
Conclusions
Tor is a critical tool to prevent censorship and strengthen users’ online privacy. It is obvious that many of the most nefarious criminal groups take advantage of this to go unnoticed, so it is unlikely that the governments of the world will leave behind their interest in monitoring the activities on this network, so we are in a scenario similar to that of an arms race for privacy and anonymity online.
In this context, all that’s left for legitimate users to make proper use of this network, taking advantage of the tools at their disposal to access Tor securely. To learn more about cybersecurity risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











