A group of researchers has reported tracking detection of some of the most important groups dedicated to information theft, which operate through pay-per-click (PPC) ads in Google search results. According to Morphisec experts, malicious ads appear on the first page of Google results and force the download of malicious packages from platforms such as AnyDesk, Dropbox and Telegram.
The researchers analyzed three attack chains that lead to malicious tools like Redline, Taurus and a new compromise mini-Redline infostealer. Two of the operators of these attacks abuse certificates and similar command and control centers (C2), while the third uses Redline.
For its part, Google claims to employ proprietary technology and malware detection tools to perform periodic scans for any indication of malicious activity, in addition to prohibiting practices such as calling third parties from an ad or the appearance of unc certified advertisers. Despite enabling these practices, hackers still find multiple methods to sneak malicious ads into the most popular internet search results. The Morphisec report mentions that the most popular of these techniques is an advanced obfuscation method.
These attacks begin with the appearance of some paid ads on Google that lead users to a website from which an ISO image greater than 100 MB is downloaded, thus evading the first security control in Google. The first group of hackers employs an obfuscation process to hide the .NET executables with popular tools like DeepSea. This stage leads to an obfuscated .NET DLL loader that eventually leads to a Redline .NET executable.
The second group of hackers employs the Taurus and Redline tool, which has a common functionality for stealing browser data and which wraps four layers of obfuscation around its configuration and communication patterns. Upon the latest malicious grouping, its executables recreate and run a legitimate AutoIt compiler with a malicious AutoIt script and a malicious encrypted Taurus executable that will be emptied into the AutoIt process.
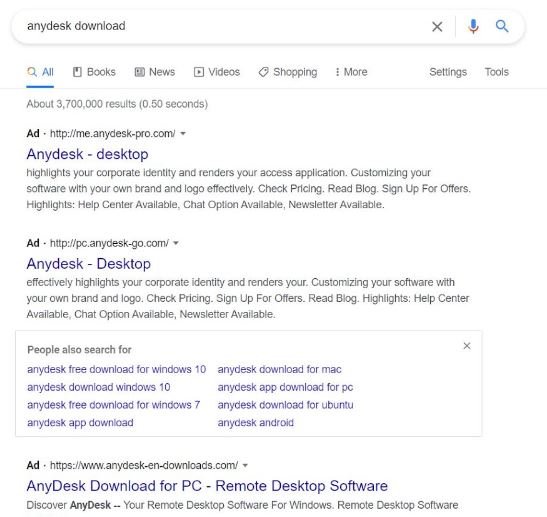
The researchers also found that a simple search on any desktop computer leads to the appearance of PPC ads on Google. These ads lead to malicious information thieves; while the first two ads lead to information thief Redline, the third leads to Taurus.
Joseph Neumann, a cybersecurity specialist at Coalfire, mentions that this is an unsophisticated but very dangerous attack variant: “It’s pretty simple to take a legitimate program and package it with malicious payloads, pay an ad hosting provider, and publishes the content,” he says. Even if these attacks were more complex, their execution is too obvious for Google to fail to detect. However, the company has not been able to disrupt these malicious campaigns due to misfocusing.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











