A recent research states that certified PDF files are not protected enough, so they are vulnerable to various types of cyberattack. These files are often used to securely sign agreements between two parties, as certification protects document integrity.
The research, by a specialized team at Ruhr University, notes that certified PDF documents employ two specific signatures for authentication, in addition to a certification firm. Certification firms are the most flexible and are made to handle complicated agreements between multiple parties, as well as en allow for some limited changes to the document.
The vulnerabilities reside in these certified signatures, as experts discovered that this mechanism is exposed to two new attacks identified as “Evil Annotation” and “Sneaky Signature”, which allow the overlapping of malicious content over the legitimate signature.
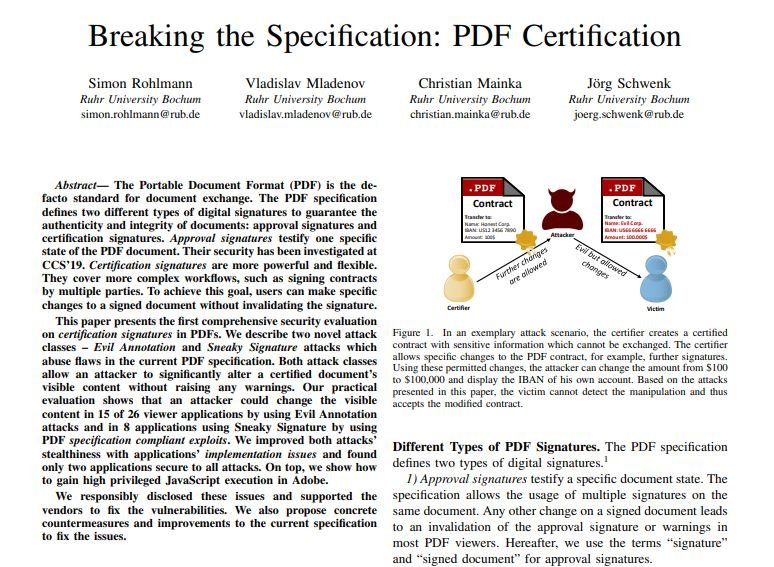
While the first attack variant allows hackers to display malicious content in document annotations and send it with the digital signature intact, the Sneaky Signature attack adds malicious content above the legitimate content.
Researchers analyzed 26 of the most popular PDF visualizing tools, finding alarming results: “Only two of these tools are safe from these attacks, while multiple versions of applications like Adobe, Foxit and LibreOffice are affected by at least one of these malicious techniques,” experts say.
These findings were presented to all affected suppliers, in conjunction with a series of supplementary reports on each security flaw found.
In order to mitigate the risk of exploitation, researchers recommend that administrators disable FreeText, Stamp and Redact, three particular annotations that can be abused by threat actors. This is not to say that the risk will be completely eliminated, so developers need to address these security risks.
The report also mentions that signature fields must be configured in locations defined in the PDF document before completing the certification process: “Subsequent addition of signature fields must be penalized with an invalid certification status. Otherwise, it can always be used to add text or images included in the signature at any position,” concludes the report.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











