U.S. authorities agreed the emergency pass of a new law after the country’s main pipeline was compromised by a ransomware attack that severely disrupted operations. Colonial Pipeline carries more than 2.5 million barrels per day, equivalent to 45% of the fuel supply for West Coast aircraft.
The approved legislation relaxes the guidelines for road fuel transport, so drivers will now be able to work extra hours when transporting petroleum products. On the other hand, while fuel prices have remained stable, experts fear this could change if colonial Pipeline outages continue.
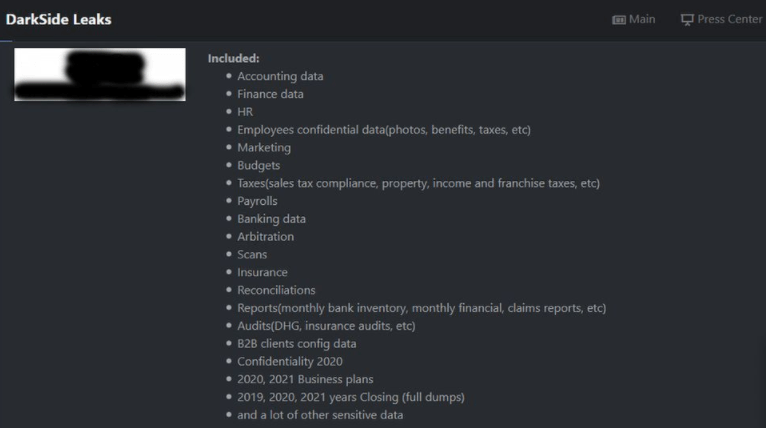
On the attack, sources mention that it was deployed by DarkSide ransomware operators, who sent a file with information about encrypted computers and servers. The hackers listed the stolen data types and sent the affected systems a URL showing that the compromised information is ready to be posted on illegal hacking forums in case the affected organization does not make the payment within the set timeframe.
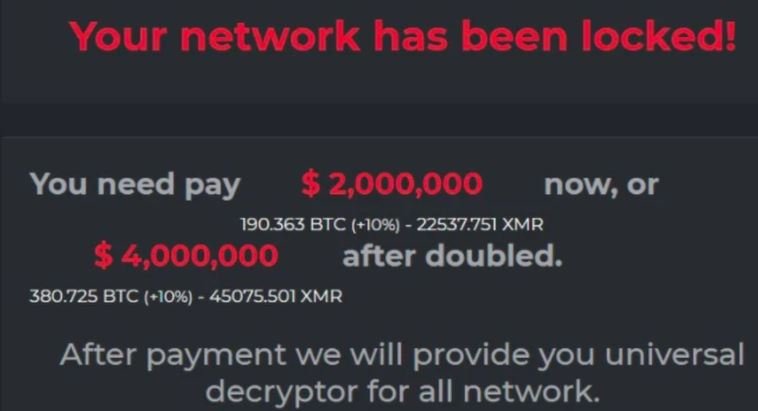
Hackers also offered to send evidence that the data was actually compromised and that it is ready to filter or even permanently delete it. At the moment it is ignored whether the directors of the pipeline will try to negotiate with the hackers or whether the incident will be addressed with the organization’s backups.
Cybersecurity specialists mention that DarkSide is a ransomware as a service (RaaS) platform, which means that hackers engage in the development of malware and partner with external criminal groups tasked with deploying the attacks. The gains obtained by this practice are divided between malware creators and attackers.
DarkSide developers even have a dark web platform that lists all public and private organizations that have been compromised in previous attacks, as well as including a list of organizations that, by policy, have decided never to attack.
Researchers mention that the attack on the pipeline was made possible by many of the engineers working at Colonial who have been working from home because of the pandemic. James Chappell of digital security firm Shadows mentions that ransomware operators might have purchased a set of login credentials for remote desktop systems such as TeamViewer and Microsoft Remote Desktop.
Chapell concluded by mentioning that, most likely, DarkSide is developed by Russian-speaking hackers operating from countries such as Ukraine, Russia, Belarus, Georgia or Azerbaijan. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











