Security teams at popular consumer credit agency Experian announced the correction of a weakness on an associated website that would have allowed any unauthorized user to conduct credit searches related to millions of U.S. citizens. Although the flaw has already been resolved, the researcher who made the first report mentions that this same scenario could be replicated on many other websites working with Experian.
Bill Demirkapi, an independent security researcher and student at Rochester Institute of Technology, said he discovered this leak while looking for loan services for college students.
The student mentions that he found a website offering to verify his eligibility for a loan by simply entering his name, address, and date of birth: “By verifying the code on this website, I could see that an Experian API was invoked,” Demirkapi said. For obvious reasons, this is not a process that should be available to any lending website: “Experian must require non-public information for such queries, as attackers could use this condition as a vulnerability,” the expert adds.
Demirkapi discovered that the Experian API could be accessed directly without any authentication, and that entering only zeros in the “date of birth” field allowed obtaining the credit score of almost any user, even creating a command-line tool to perform an automated search.
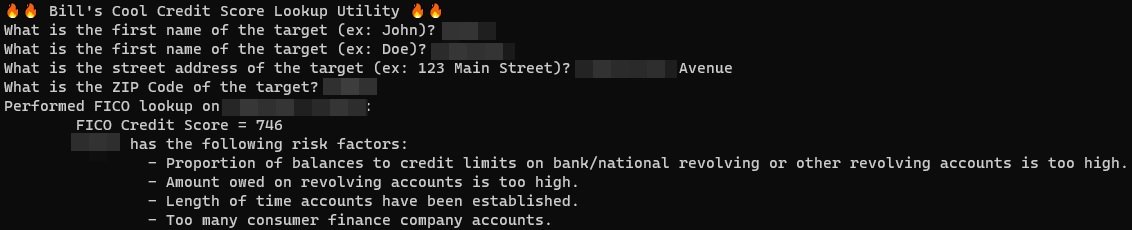
A group of researchers tested this tool and was able to demonstrate that it is really functional, helping to find credit scores and risk factors for the analyzed users
Demirkapi refused to share with Experian the name of the lender or the website where the API was exposed, arguing that there could be many more sites exposing this information: “If we let them know the name of this website, Experian could simply block specific requests, which doesn’t really solve anything.”
Still, shortly after receiving Demirkapi’s report, Experian’s security teams discovered the source of the leak: “We have confirmed that only one instance is impacted by this incident, and that it has already been corrected.”
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











