Mobile security risks seem to increase as we rely more on our smartphones for routine tasks such as communicating and organizing our work. A recent report published in Forbes by mobile security experts Luis Marquez and Ernesto Canales describes a risk scenario that could lead to the blocking of any of the more than 2 billion active accounts of WhatsApp, the world’s most popular messaging service.
The report begins by pointing out the little innovation that exists around this platform, whose infrastructure pales compared to that of its competitors (Telegram, Signal, among other services). In general, WhatsApp lacks measures considered standard for the security of these platforms, including backup encryption and secure access to multiple devices.
Experts then refer to session hijacking, one of the main security risks for WhatsApp users and their controversial use of authentication codes, six digits sent via SMS when users want to activate a new app installation. In case of intercepting one of these codes, threat actors could access all the information stored in the compromised WhatsApp account, leaving the affected user without access to their own chats.
It is important to note that such an attack requires human error, as the target user must share this code with the attackers for session hijacking to occur. However, the fact that the platform does not use multi-factor authentication by default certainly makes things easier for malicious hackers.
The vulnerability described by specialists is related to two separate WhatsApp processes affected by a serious security weakness, which would allow an attacker to deactivate the affected user’s account and prevent its reactivation. As mentioned earlier, when you install the app on a new device the service sends a code via SMS for account verification and then requests an authentication number.
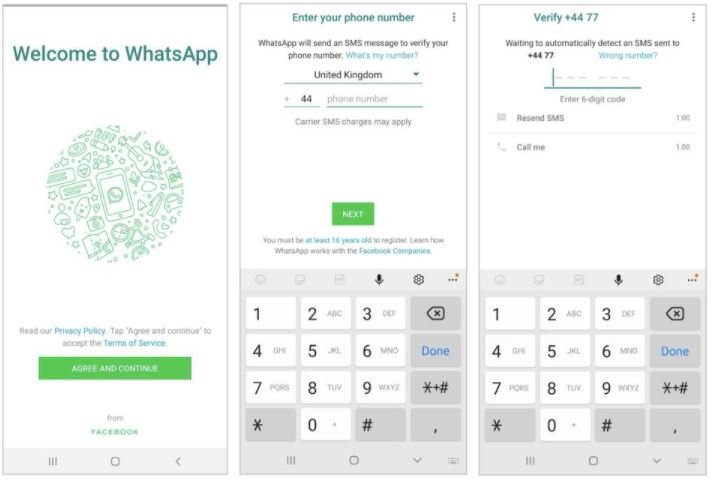
Here we find the first weakness, since any user could install the app on a new device and enter the phone number of the target user to request a verification code.
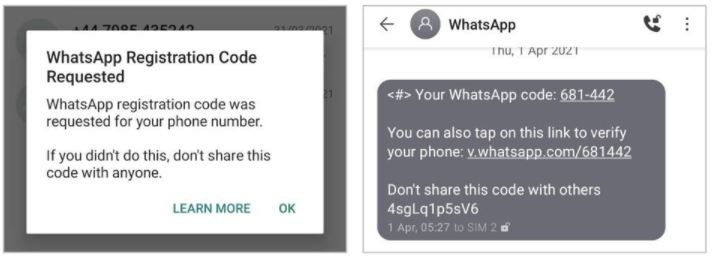
The WhatsApp verification process limits the number of codes that can be sent, so after some incorrect attempts by attackers, WhatsApp will have the user choose whether to receive a new SMS or a call after 12 hours.
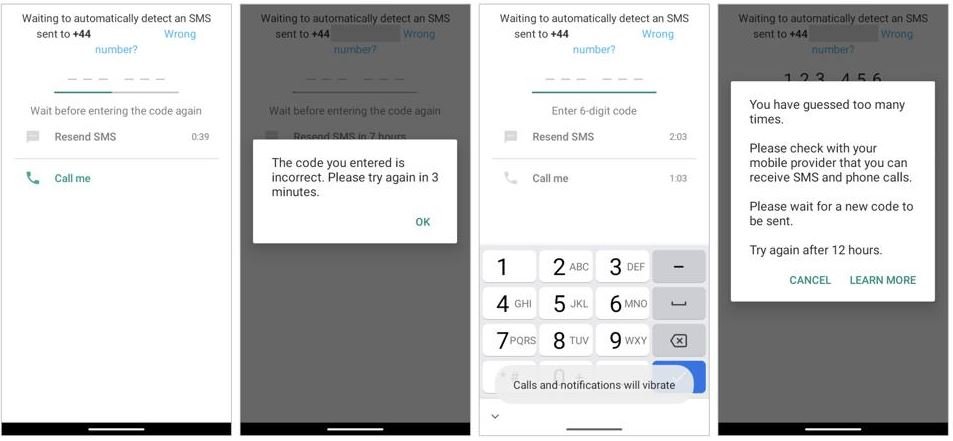
In the meantime, the legitimate user’s app will continue to function normally, without receiving any notification about malicious activity related to their phone number. Now all attackers have to do is waiting for the platform’s 12-hour deadline to be met.
The second weakness will then appear, as threat actors will be able to register a new email address and send a message to support@whatsapp.com requesting the deactivation of the target account. WhatsApp only asks for the phone number via an automatic response, so it is relatively easy for threat actors to deactivate a WhatsApp account.
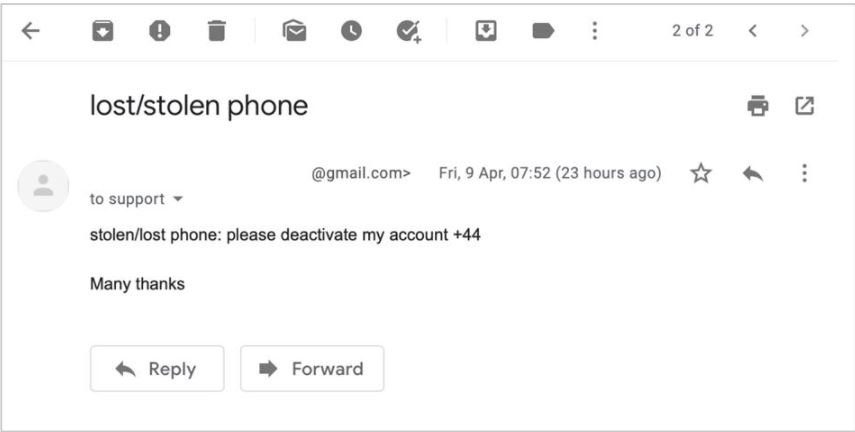
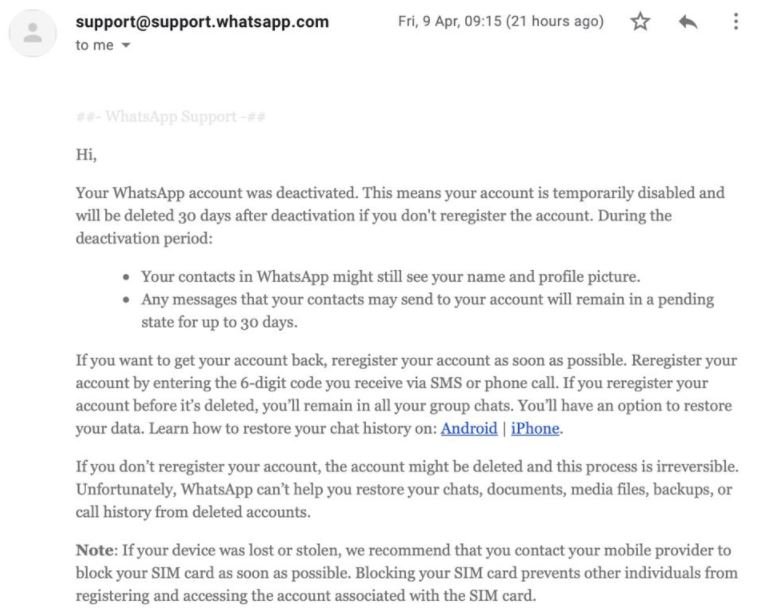
In less than an hour the platform deactivates the account associated with the phone number sent by email, notifying the user that the phone number is no longer registered for WhatsApp on their phone.
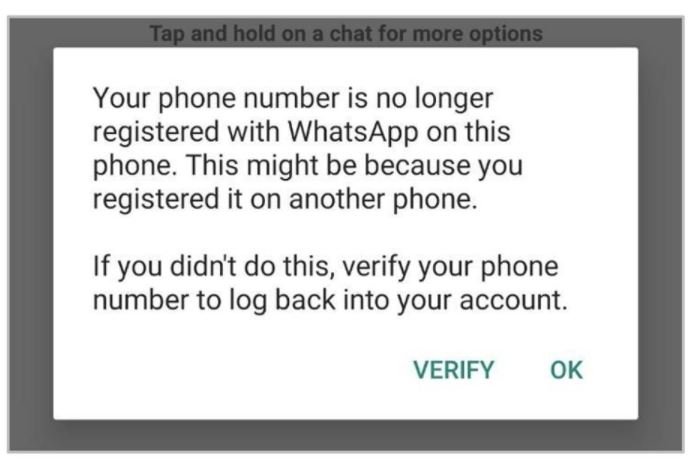
This seems to be an automated process and works regardless of whether the user has multi-factor authentication enabled. Under normal conditions this should not be an issue for users, as it is enough to request the sending of a security code to reactivate their account; however, the intervention of threat actors prevents users from recovering their account due to the 12-hour period triggered by the repeated number of failed attempts on the platform.
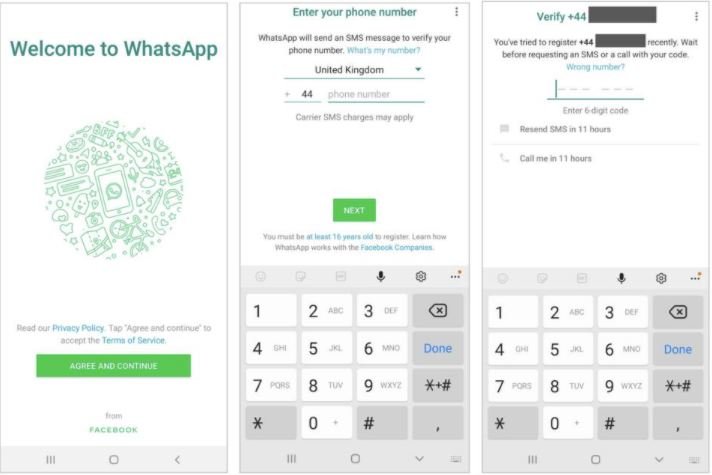
At this point, the target user and attackers will face the same restrictions, and will not be able to request new codes via SMS for 12 hours.
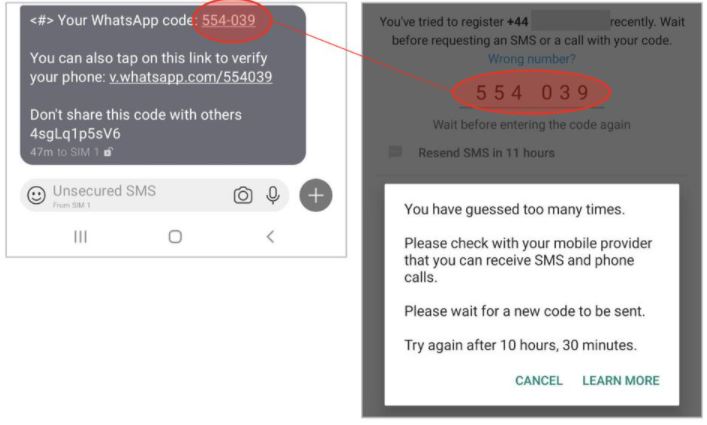
Once the 12-hour deadline has been met, threat actors will only have to wait a second 12-hour period, while the user will unsuccessfully try to regain access to their account. During the third 12-hour period, attackers will get the app to stall, as there is no way to receive new security codes and the 12-hour count will now mark a “-1 second” lapse.
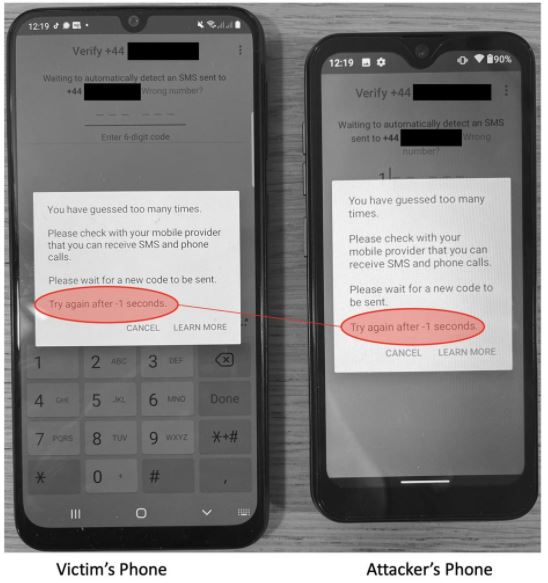
“At this point it will be too late to try to recover the account in an automated manner,” the researchers say. If so, the user only has to try to recover their account with the help of some employee of the platform.
This attack variant depends entirely on the security conditions in the application, plus its abuse does not require technical knowledge. For attackers’ purposes, experts point out that there are multiple reasons why a threat actor would want to prevent a user from accessing their WhatsApp account, so the platform should prevent such attacks from happening with such ease.
Experts also mention that this finding has revealed another critical condition on the platform, as there is no way to prevent hackers from discovering whether the target user has an actic WhatsApp account: “Users need the platform to take a greater approach to user privacy, as it is very easy to affect users with the least effort.”
In addition, a company spokesperson noted that the circumstances identified in this investigation would constitute a violation of its terms of service, so it requests interested parties to request further reports via email.
This message left many doubts to the experts, as the platform did not confirm whether it is preparing any methods for correcting weaknesses that allow account blocking. Perhaps this invites more users to follow the example of Mark Zuckerberg, who uses the encrypted messaging app Signal despite owning WhatsApp.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











