A security report details the finding of malicious code in the official APKPure app, one of the most popular app stores for Android devices outside the Play Store. This platform offers users “identical versions” of popular games and tools that would otherwise only be available on Google’s official store.
The malware resides in version 3.7.18 of APKPure, as noted by Kaspersky experts who prepared the report in collaboration with Dr. Web.

Experts note that this malware appears to be a variant of Triada, a Trojan detected in early 2016 characterized by sending spam to infected devices for additional malware delivery: “When you start the infected APK, it will automatically decrypt the payload for release, then the malware will collect additional information about the device to send it to the C&C server of the threat actors.”
When the Trojan is loaded, malware operators may display invasive advertisements and perform arbitrary clicks to generate subscriptions to services not authorized by the user and even download other malware variants. Then, depending on the telephone operator, some of the following conditions may be triggered:
- Ad appearance every time your device is unlocked
- Sudden and continuous start of websites with ads
- Arbitrary clicks on ads to subscribe to paid services
- Installation of other payloads or potentially malicious software without the user’s consent
Experts note that the consequences of the attack vary depending on the version of the operating system on the infected device, although in general affected users experience malvertising issues.
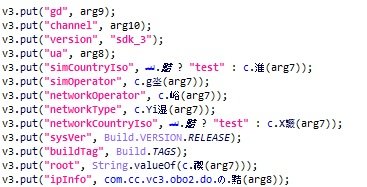
The operators of this app store do not have exact figures about the times this APK has been downloaded, although experts claim to have blocked the malware on at least 9 thousand 300 Android devices with the official Kaspersky antimalware solution installed. The report was presented to APKPure developers, who rushed to release version 3.17.19, free of malicious code.
APKPure users are invited to install the secure version of the app to prevent future security incidents.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











