This time, experts in malware analysis from the International Institute of Cyber Security (IICS) will show you an easy procedure to create fake websites in order to extract information from any user from operating systems like Android, iOS and Windows.
It is important to mention that the information contained in this tutorial is for educational and informational purposes only, so IICS is not responsible for any misuse that may be given to this information.
According to malware analysis experts, we will need the following elements:
- Winrar Archiver
- JPG
- HxD Hex Editor HxD – Free hexadecimal editor and disk editor | mh-nexus
To get started, install HxD and drop its icon into the folder with the virus
Then take the virus and arch it, no problems with the settings, just compress this item in Zip format
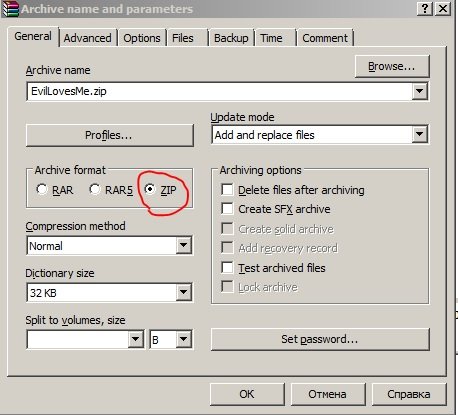
As a result, the tool will throw a file with a virus in .exe
According to malware analysis experts, a window will open where we see all the code, then we go to the Search tab> Search or press Ctrl + F
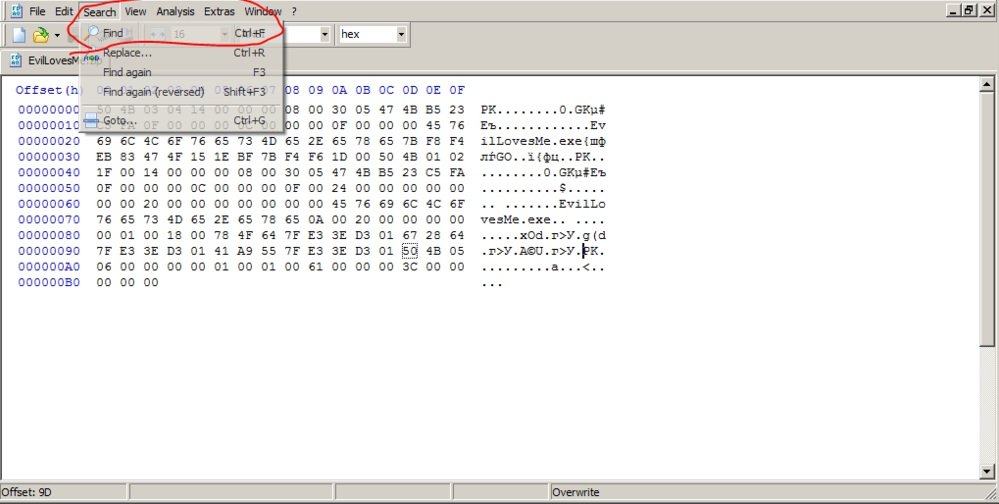
Now, type in the search box “Full name of virus.exe”
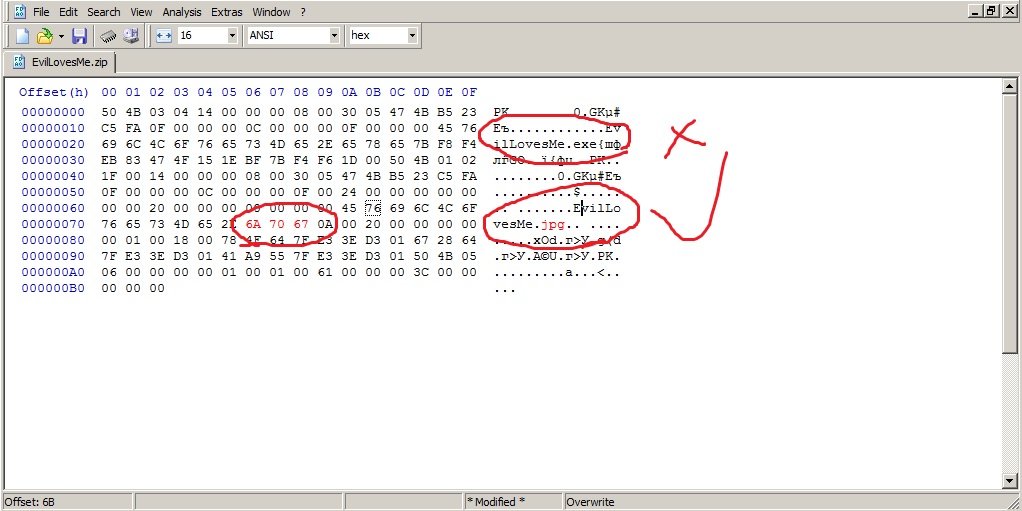
When searching, you’ll find two records, one at the bottom and the other at the top of the code. Try not to get confused, as we will need the lowest value; then we’ll change the .exe to the .jpg.
Now we save all this, open our file and see this image.
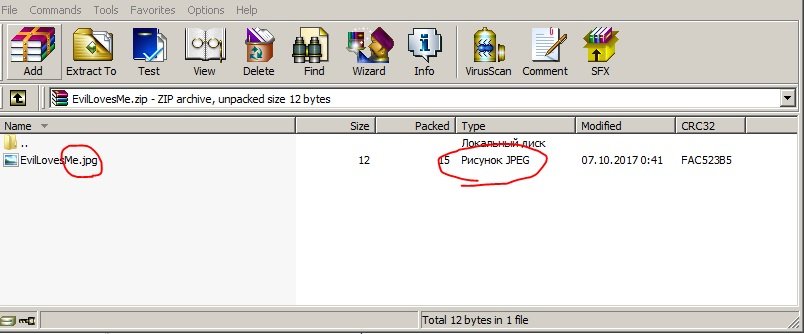
As you can see, .jpg, next to the Type tab, says it’s a JPEG image
And that’s it. You can also redo and launch this ZIP file in the .txt format and launch this file as part of a phishing or malvertising campaign. This attack is highly effective as users would never be suspicious of a simple text file.
Don’t forget that your malicious creation, whether it’s a cryptojacker or a backdoor, must be encrypted so as not to be detected by antivirus solutions, although that will be a theme for another occasion. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











