A group of threat actors maintains an active attack targeting GitHub Actions systems with the intention of extracting cryptocurrency in a hacking variant known as cryptojacking. As you may remember, GitHub Actions is a CI/CD solution that makes it easier to automate particular resource flows, as well as allow for periodic task configuration.
Apparently, this attack is based on injecting malicious code from GitHub Actions into forked repositories in a legitimate repository, as well as creating pull requests for maintainers to integrate malicious code with the repository’s original code. The report also mentions that the malicious code loads cryptocurrency mining software identified as npm.exe from GitLab, being executed with the cryptocurrency wallet address of the threat actors.
ATTACK PROCESS
It all starts by forking a legitimate repository with GitHub Actions enabled. Threat actors then inject malicious code into the forked version to file a pull request with which those responsible for maintaining the original repository will need to merge the code again.
Through his Twitter account, researcher Justin Perdok mentioned that there are at least 95 repositories that are under attack.
One surprising thing about this attack is that threat actors do not require the right project maintainer to approve the pull request, as just sending it is enough to continue arbitrary actions, especially in the context of GitHub projects with certain configurations.
The moment the removal request is created the GitHub infrastructure will execute the malicious code, starting to run the cryptojacking software.
As mentioned above, the mining software is identified as npm.exe although Perdok mentions that the software is mislabeled, giving the impression that it has some relationship with the official NodeJS installers.
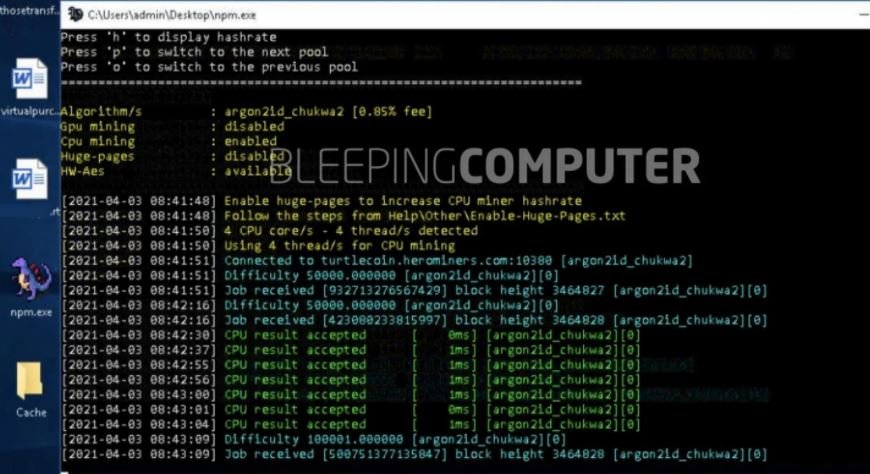
In tests conducted by cybersecurity specialists, executables connect to the turtlecoin.herominers.com cryptocurrency group, starting their cryptocurrency mining activities.
Through a spokesperson, GitHub mentions that its security teams are aware of this campaign, so an internal investigation has been initiated. It should be noted that this is not the first time that hacking groups have abused implementations such as GitHub Actions, as a while ago researcher Yann Esposito described an attack variant directly abusing pull requests.
In 2020 GitHub security teams also received reports of an attack method based on hosting a botnet on their systems, abusing pull requests in a similar way to that made by this cryptojacking campaign.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











