Apple developers announced the release of a set of updates to fix a zero-day iOS flaw that impacts both iPhone and iPad devices and Apple Watch. According to the report, this flaw has already been exploited in real scenarios, so the installation of the patches is urgent.
Tracked as CVE-2021-1879, this flaw was reported by Clement Lecigne and Billy Leonard of Google Threat Analysis Group.
The flaw lies in the Webkit browser engine and would allow threat actors to launch cross site scripting (XSS) attacks after tricking affected users into opening malicious websites on their devices.
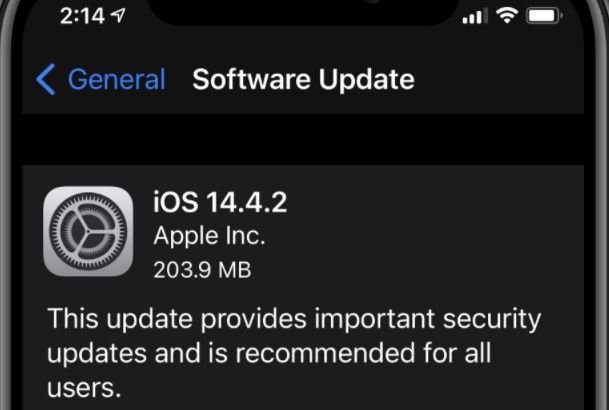
These flaws were fixed by making an improvement in object lifetime management in iOS 14.4.2, iOS 12.5.2, and watchOS 7.3.3. According to Apple’s message, this security measure provides important security updates, so it is recommended that all users upgrade to the latest version of iOS available for their devices.
In addition to fixing this flaw, Apple released security patches for two other recently exploited zero-day flaws in some versions of iOS. These flaws were reported by Project Zero, Google’s team specializing in vulnerability analysis.
Last January the company also released a patch to fix a race condition vulnerability in the iOS kernel and two Webkit flaws; these vulnerabilities were identified as CVE-2021-1782, CVE-2021-1870 and CVE-2021-1871.
Finally, it should be remembered that Apple fixed three other iOS zero-day vulnerabilities: a remote code execution error (CVE-2020-27930), a kernel memory leak (CVE-2020-27950) and a kernel privilege escalation flaw (CVE-2020-27932), so it’s important that iOS device users stay on top of the latest updates.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











