Cybersecurity experts report the detection of Sarbloh, a new variant of ransomware that encrypts infected systems and sends messages to support protests by thousands of farmers in India.
In 2020, the Indian government enacted those known as “Agriculture Laws”, with the intention of modernizing the country’s agricultural processes. However, producers believe that these new laws will harm their livelihoods and make it difficult to generate income, as any restrictions on the purchase and sale of agricultural products have been removed.
This bleak panorama has led thousands of Indian farmers to demonstrate in the territories surrounding New Delhi since November 2020.
Reports, prepared by firms such as Malwarebytes and Cyble detail the emergence of this encryption malware, distributed via malicious Microsoft Office documents that include support messages for protesting farmers. Researchers still don’t know if these files are sent via phishing emails or if they are hosted on a compromised website, although they are distinguished by asking users to enable the content to access the entire document.
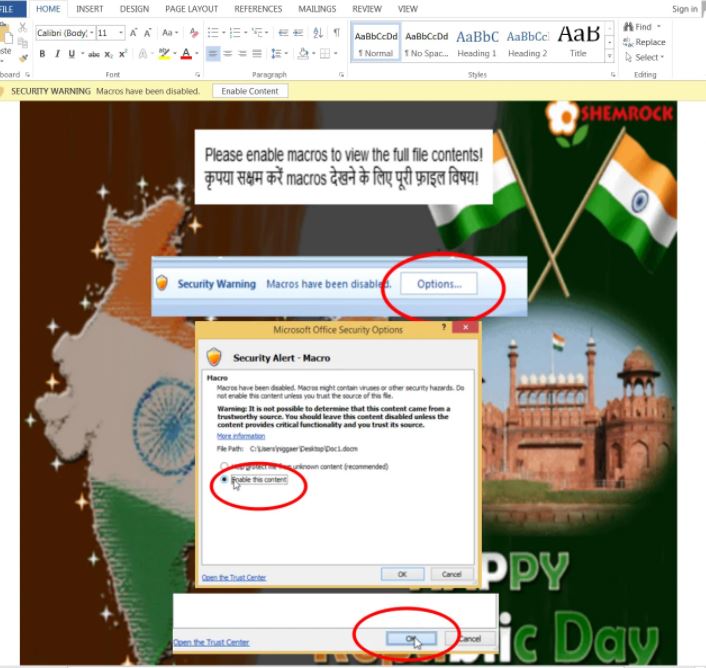
When users enable content, macros will download a file identified as putty.exe using bitsadmin.exe in the documents folder and then run. Once executed, the ransomware will encrypt the system and add the .sarbloh extension to each infected file.
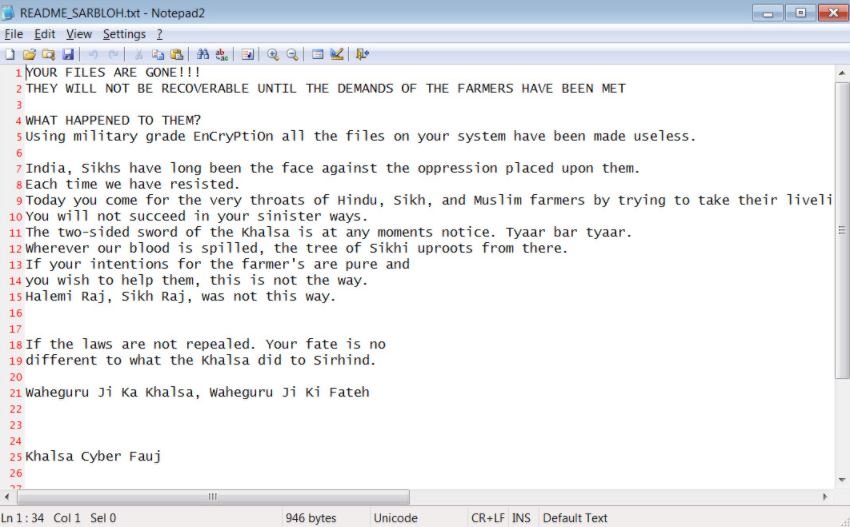
Upon completion of this process affected users will find the ransom note corresponding to the attack (README_SARBLOH.txt), which also includes a support message for Indian farmers. In addition to claiming that they are employing military-grade encryption, the ransom note includes a postulate on the Agriculture Act: “The people of India have long been the face of oppression. Today the powerful come down the throats of Hindu, Sikh and Muslim farmers trying to take away their livelihoods. They will not succeed in their sinister paths,” the document adds.
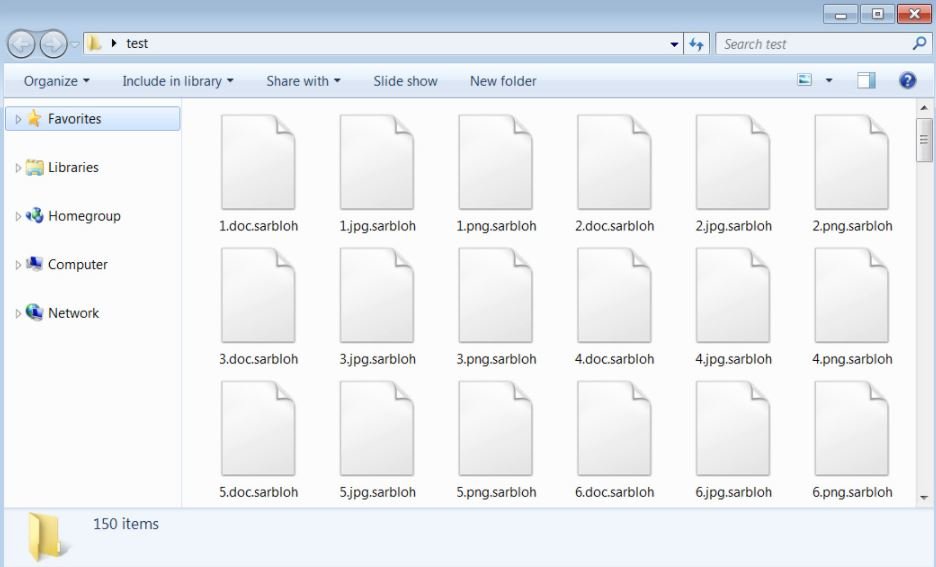
The ransomware appears to be named after the ‘Sarbloh Granth’, a book of scriptures related to one of the many religions practiced in India.
Michael Gillespie, ransomware specialist and creator of the specialized platform No More Ransom, Sarbloh is based on an open source ransomware known as KhalsaCrypt, for which at the moment there are no decryption tools, so victims of this infection will have to resort to their backup systems or, in a critical case, to pay the ransom.
The good news is that Gillespie ensures that unlike other encryption variants, Sarbloh operators do not delete shadow volume snapshots, providing an opportunity to restore systems to normal.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











