The attack on the SolarWinds supply chain through the SolarWinds Orion tool has proven to be one of the most devastating hacking incidents of recent years, impacting thousands of public and private organizations worldwide. One of the main features of this attack is the distribution of binaries through legitimate updates, which allowed the theft of credentials, privilege escalation attacks and eventually theft of sensitive information.
Microsoft is one of the institutions that have invested the most resources in investigating this complex attack, which has enabled the detection of source code, engagement indicators, and behavior patterns associated with the hacking group responsible for the Solorigate malware operation.
As a way to provide better defenses methods against such incidents, Microsoft decided to open source the CodeQL code, a queries set used during Solorigate’s investigation, so that other organizations can conduct similar analyses. Using these queries, researchers will be able to detect any source code that shares similarities with Solorigate, either in its basic elements or functionalities.
Using these queries to detect indicators of compromise is not a foolproof method (threat actors could restrict Solorigate’s analyzed functions); however, using this method as part of a comprehensive framework would best address this new cyber risk variant.
What exactly is CodeQL?
This is a semantic code analysis engine that is part of GitHub and works primarily in two stages; first, as part of compiling source code into binaries, CodeQL creates a database to capture the build code model, parsing the source code and creating its own build model.
Subsequently, this database is used to query in the same way as any other database, as the CodeQL language was specially designed by Microsoft to facilitate the selection of some complex code conditions. Its developers ensure that CodeQL is a useful resource as its two-stage approach unlocks multiple scenarios, including the ability to use static analysis for reactive code analysis over a complete network.
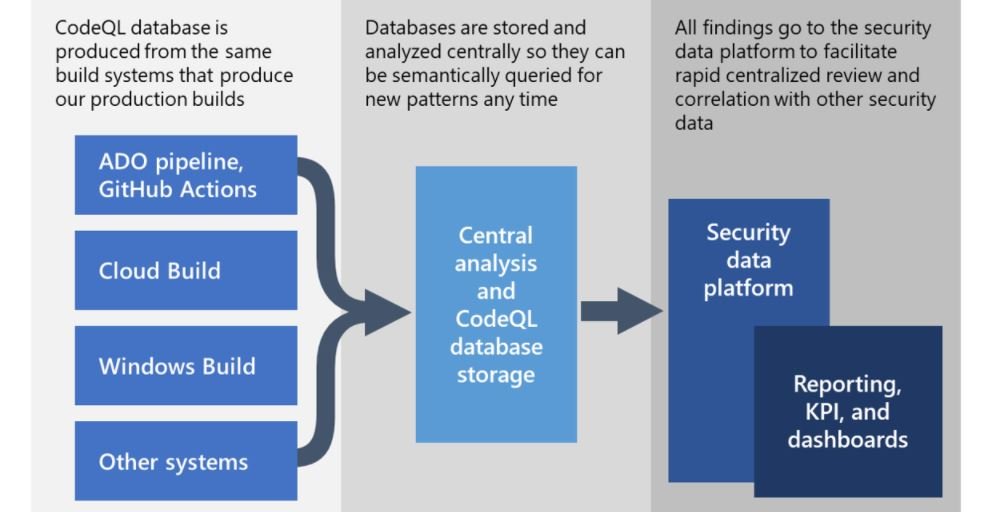
Using CodeQL databases will allow researchers to perform semantic searches on a multitude of different codes to find code conditions linkable to a specific malicious build. CodeQL will help analyze thousands of repositories for discovery repositories for some variant of failures potentially related to Solorigate.
These queries evaluate code-level compromise flags, which are also available in the GitHub repository for CodeQL. This platform hosts all the information required to detect a potential Solorigate attack, as well as guidance for other queries.
Code-level threat detection
In this research, Microsoft employed two main tactics for detecting indicators of compromise: the first approach is based on finding a particular syntax at the code level, while the latter is focused on the detection of general semantic patterns for techniques present in code-level indicators of compromise.
In addition, writing and executing syntactic queries is a relatively fast process and offers multiple advantages over finding searchable regular expressions. Semantic patterns look for general techniques, such as hashing process names, time delays before contacting C2 servers, among others. These are durable for substantial variations, but are more complicated to create and more compute-intensive when analyzing many code bases at once.
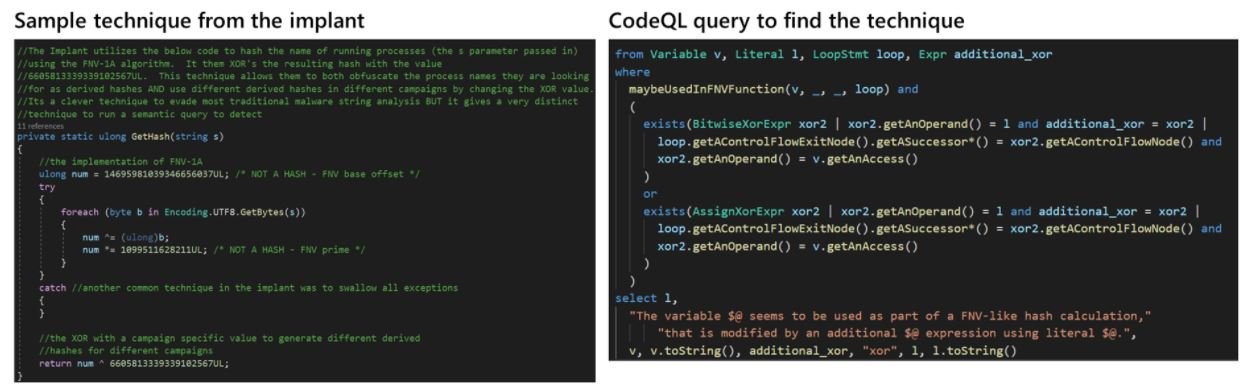
The combination of these two approaches allows detecting potentially malicious scenarios, although researchers should not forget that a threat actor could modify both syntax and its attack techniques, so CodeQL should only be considered an auxiliary tool in the context of a full security approach.
Although in its description this set of queries focuses on Solorigate code-level engagement indicators, CodeQL developers mention that the tool provides multiple options for backdoor querying and functionality and other evasion techniques. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











