Patrik Wardle, a renowned information security researcher, reported the finding of one of the first malware variants specifically designed to compromise the latest generation Apple devices using the M1 chip, one of the company’s most sophisticated developments.
The expert claims that malicious hackers are adapting existing malware variants to launch ambitious attack campaigns against Mac devices by abusing the features of their own processors. In this particular case, Wardle refers to the finding of suspicious behavior in GoSearch22, an extension for Safari browsers for Intel x86 computers that has been adapted to run on M1 chips.
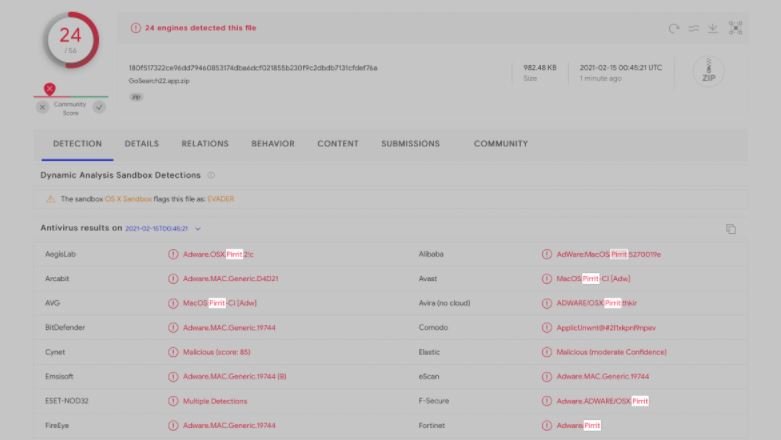
“This binary was detected in the wild, distributed via a malicious tool. By looking at the detection results we were able to conclude that GoSearch22.app is an instance of Pirrit adware,” Wardle says.
The malicious extension was signed with an Apple Developer ID to make it difficult to detect its malicious behavior; the signature “hongsheng_yan” has already been removed. Wardle adds that Pirrit is a variant of adware known by the same name and detected just a couple of months ago. Pirrit has advanced data collection capabilities for browsing and sending malicious advertisements, including banners and pop-ups.
Through these advertisements threat actors could also redirect unsuspecting users to malicious websites used to distribute malignant payloads.
Wardle concluded that GoSearch22 could be considered the first malware variant specifically designed for M1 compatibility for the reasons listed below:
- This malicious code demonstrates a continuous evolution in terms of its ability to respond directly to hardware and software changes. There are a lot of benefits in native distribution of native arm64 binaries, which is highly appealing to hackers
- Static scanning tools or antivirus engines may have problems with arm64 binaries. In a later experiment, Wardle separated the x86_64 and arm64 binaries from the GoSearch22 universal binary (using macOS’ built-in lipo utility)
Wardle noted that static scanning tools or antivirus engines face difficulties scanning ARM64 binaries, which is demonstrated by the fact that the detection rate of these malware is lower compared to Intel x86_64: “New M1 systems offer great advantages, and natively compiled arm64 code runs incredibly fast. We want to point out that malware authors have joined the ranks of developers by rebuilding their code for arm64 in order to get native binary support for Apple’s latest hardware,” concludes the expert.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











