Like other festivities, Valentine’s Day is an ideal opportunity for threat actors to deploy ambitious cyberattacks. This time, experts report that a hacking group is sending emails with information about alleged orders to flower and lingerie stores; actually these messages include links or attachments for downloading the BazaLoader malware.
This malware variant was identified in April 2020 and since then at least six variants have been detected, indicating that developers devote considerable resources for its maintenance.
The report, prepared by security firm Proofpoint, mentions that since the beginning of 2021 various phishing campaigns were detected using PDF documents infected with BazaLoader: “Hackers turn to multiple topics to attract the attention of users, including the sale of office supplies, medications and food supplements, although the closest topic is the Valentine’s Day celebration.”
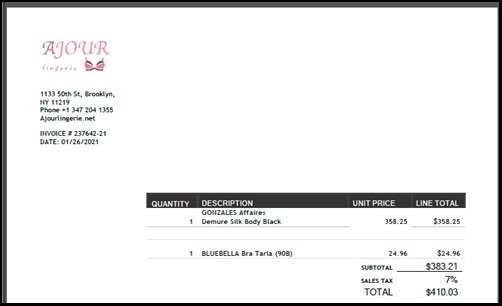
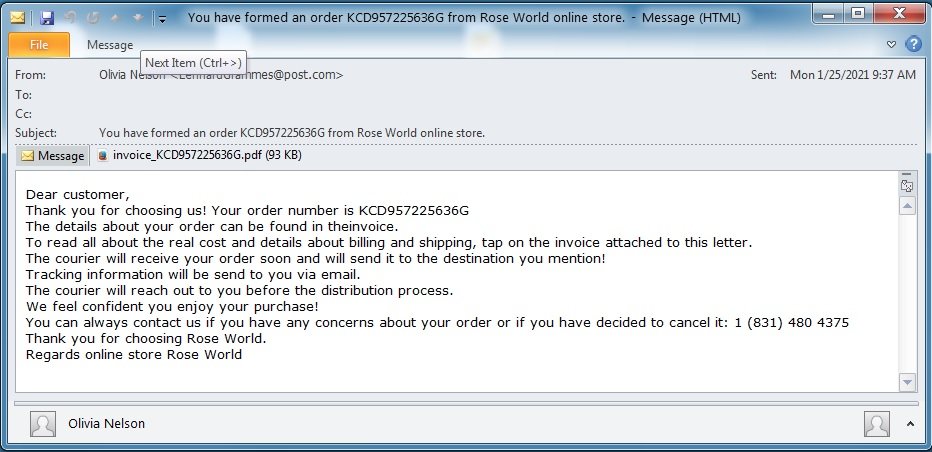
In a case analyzed by this firm, the victim received an email purportedly from a lingerie store called Ajour Lingerie, based in New York mentioning that their order had been completed, so verification of an invoice, attached in PDF format, was required. While the attachment does not contain malware, its inclusion is a critical element in completing the attack.
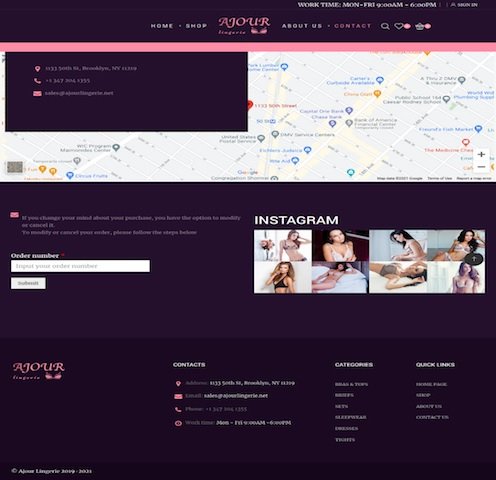
This PDF contains a link to a fraudulent website (ajourlingerie<.>net) pretending to be the official site of Ajour Lingerie (ajour.com). The fraudulent website is an identical copy of the legitimate lingerie company platform, so it is not strange to think that a user can be deceived. The fraudulent platform includes a “contact” section that, if visited by victims, opens a window to enter the details of the false invoice, which in turn will download a spreadsheet. If users activate the macros in this file, they will start downloading BazaLoader. This method of attack is replicated using the image and fraudulent sites of companies dedicated to sending flowers.
Researchers are still trying to determine what malware variant is downloaded by BazaLoader, although they have already detected a great similarity between this malware and others like TrickBot.
This is a sign of how easily hackers can deploy a malicious campaign by abusing holidays. Last year a group of researchers reported that multiple iPhone users received fraudulent messages that tried to convince them to download a dating app loaded with malware for information theft, among many other malicious features.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.