Cybersecurity experts report a new supply chain attack method in which perpetrators managed to compromise the update process of NoxPlayer, a popular Android emulator for Windows and Mac systems developed by BigNox. According to its own numbers, NoxPlayer has more than 150 thousand users in a hundred countries. This tool is used mainly by video game users for mobile devices eager to bring these developments to the screens of their PCs.
The report, prepared by the IT security firm ESET mentions that the malicious hackers managed to inject the malware into a small number of users, mainly in Asian territory. The experts detected at least five infected users in Syria, Taiwan, Hong Kong and Sri Lanka.
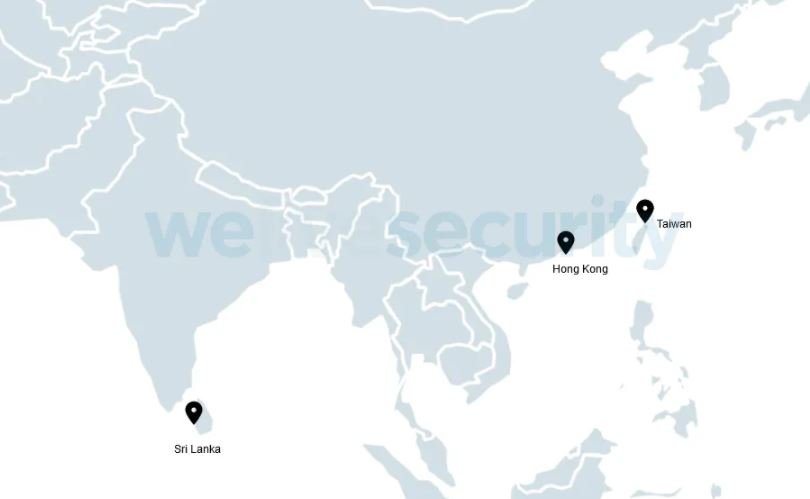
The researchers dubbed this campaign “Operation NightScout.” Researchers report having detected this attack mechanism, which employs at least three different variants of malware distributed through malicious installations and targeting previously selected victims; Because there appears to be no financial benefit for hackers, experts believe it could be a spy campaign.
The attackers reportedly compromised one of the company’s official APIs (api.bignox.com) and file hosting servers (res06.bignox.com). When the attackers generated persistence, the hackers manipulated the NoxPlayer update download URL on the API server in order to deliver the infected updates.
ESET also included some technical details about the attack so that general emulator users can identify if their installation has been compromised and can even remove the malicious installation by their own methods. Although ESET does not attribute this campaign to a specific hacking group, the report mentions some similarities between the malware variants detected and some samples collected by the Myanmar authorities after a cyberattack that compromised their government websites.
This has been an especially prolific period of time for supply chain attacks. However, experts mention that the attack method used in Operation NightScout is especially striking because this is an unusual vector for the deployment of cyber espionage operations against users of digital platforms. Android has issued no statement on this incident.
For further reports on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses fell free to visit the International Institute of Cyber Security (IICS) websites, as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











