A group of specialists has revealed the discovery of a new variant of surveillance and spying malware for iOS and Android devices. Identified as Goontact, the new spyware has the ability to collect all sorts of details about infected devices, including phone ID, contact list, SMS messages, photos and location data.
Goontact was first detected by researchers at mobile security firm Lookout, who mention that spyware is distributed through third-party websites that advertise messaging apps specially designed to hire escort services.
At the moment the activity of this spyware seems to be limited to countries such as South Korea, Japan and Chinese-speaking territories throughout Asia, the researchers mention.
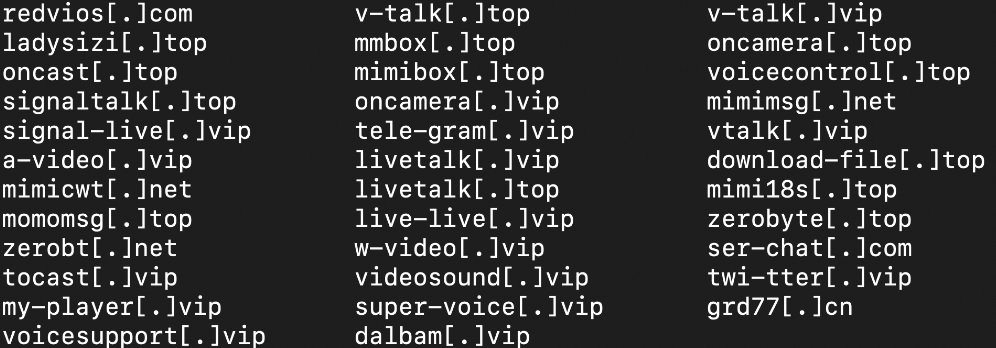
The list of apps that contain Goontact is too long, so it’s not convenient to include it in this note. However, the following is a list of all websites that advertise any of the malicious apps:
This malware variant has not yet been detected in malicious apps available on the App Store or Play Store, although experts do not rule out cybercriminals trying to infiltrate official platforms with this spyware.
After being installed on the target device, Goontact begins to collect information to be sent to the hackers’ servers. Because of the language used in the management panels of the analyzed servers, experts believe this could be an operation deployed by Chinese cybercriminal groups.
Lookout specialist Apurva Kumar mentions that this operation is very similar to a sextorsion campaign detected a couple of years ago: “Our investigation is still ongoing, but we believe that the data collected in this campaign could be used to extort victims; hackers have a lot of confidential information.”
Experts notified Google and Apple of their finding so companies can implement the necessary measures before it’s too late: “Multiple apps will stop working as a result of a revocation of business certificates potentially associated with this campaign,” Kumar added.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










