Microsoft security teams have warned their users about a campaign related to Adrozek, a browser hijacking and credential theft malware capable of compromising up to 30,000 users a day. Malware operators inject ads into results pages in search engines and have the ability to hijack Microsoft Edge, Chrome, Yandex and Firefox sessions.
According to experts, this malware uses malicious scripts to inject advertisements after modifying the settings and components of the target browser. The Microsoft 365 Defender research team recommends that users uninstall and reinstall their browsers to prevent this attack.
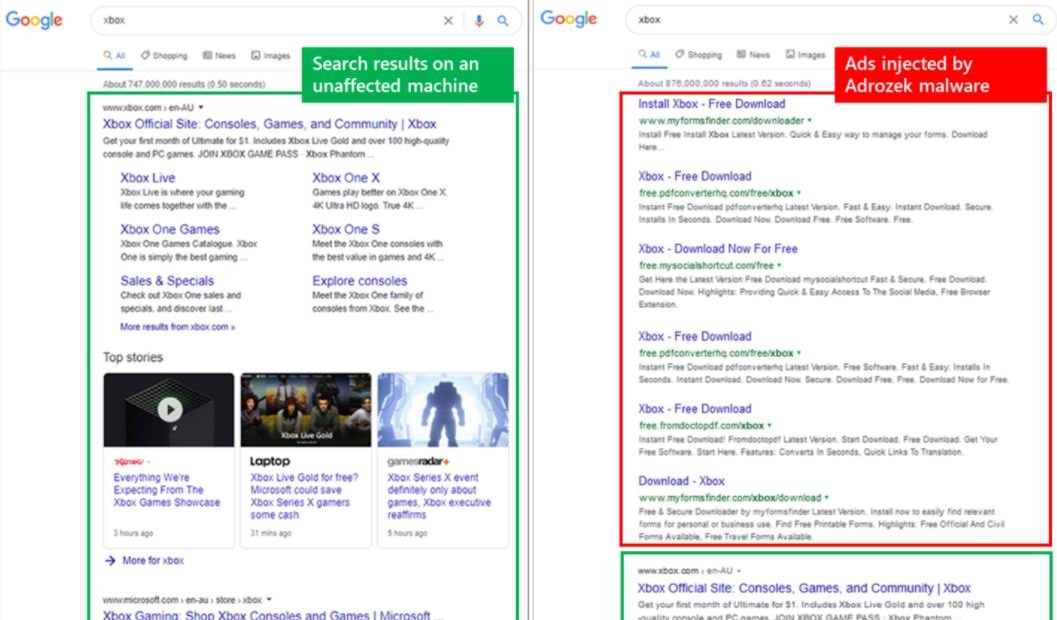
“If Adrozek is not detected, the malware is able to add browser extensions, modify a specific DLL and change the affected browser settings to insert additional malicious advertisements,” the specialists mentioned.
Although Microsoft specialists have found no evidence that Adrozek is being used to send malware to vulnerable devices, they do recognize these attacks they could begin at any time: “Hackers could infect their devices with additional malicious payloads or cede control of this malware to other groups of threat actors.”
So far this campaign has used 159 domains to host around 17,000 unique URLs through which more than 15,000 malware samples have been delivered, triggering hundreds of thousands of potentially affected devices.
Experts believe Adrozek’s infrastructure continues to expand, adding new domains to continue infecting vulnerable devices. According to Microsoft, “the infrastructure of this hacking group is dynamic. While some domains remain active for just a few hours, others can prevail for up to 120 days.”
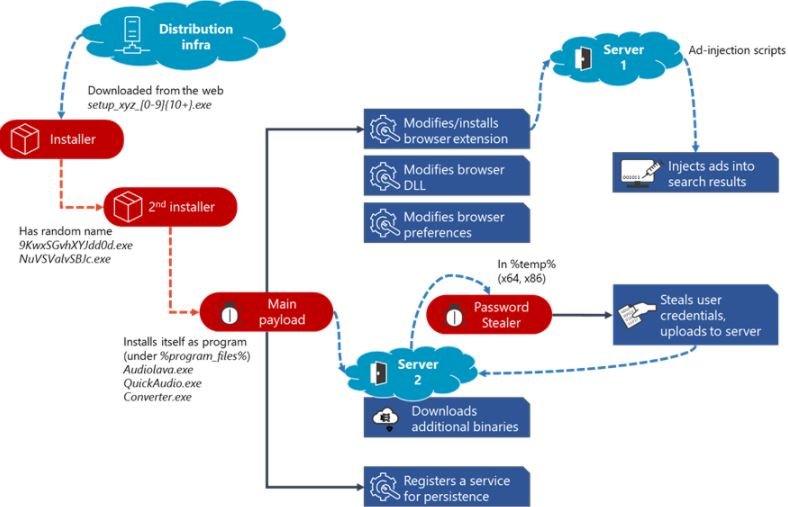
Malware operators infected their victims through unauthorized downloads as soon as they entered any of the malicious domains. Because it is a variant of polymorphic malware, Adrozek is able to avoid detection and make it easier for its operators to implement large volumes of new samples.
When installed on the target device, Adrozek will begin adding the malicious scripts to complete the injection of advertisements in various extensions aimed at each of the browsers it hijacks. The malware will disable security controls in Microsoft Edge and other Chromium-based web browsers, disabling secure browsing and enabling hijacked extensions in incognito mode.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











