Specialists in a form of security report finding 33 vulnerabilities in four open source TCP/IP libraries widely used in the firmware of more than 150 vendors. Researchers believe that millions of devices used in industrial, domestic and commercial environments could be exposed to this set of failures, dubbed Amnesia:33.
All kinds of smart devices could be affected, including smartphones, video game consoles, HVAC systems, printers, routers, switches, as well as all kinds of industrial control devices.
The broad impact of these flaws lies in the fact that they affect four widely used open source libraries: uIP, FNET, picoTCP, and Nut/Net. For more than 20 years, device manufacturers have added one of these four libraries to their device firmware, allowing their products to support TCP/IP, the most widely used network communication protocols today.
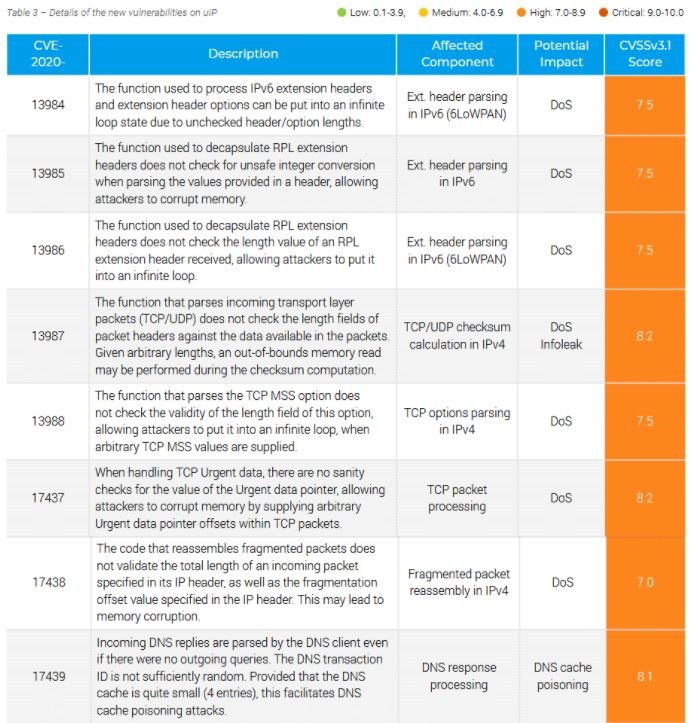
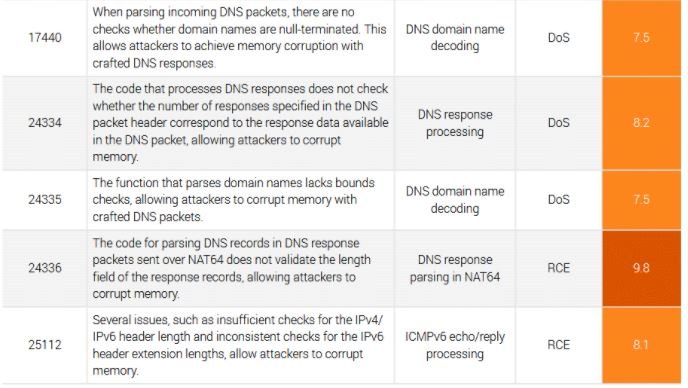
Experts believe that, if exploited, these failures would allow threat actors to deploy multiple variants of attacks, including:
- Remote Code Execution (RCE)
- Denial of Service (DoS)
- Leak of confidential information
- DNS cache poisoning attacks
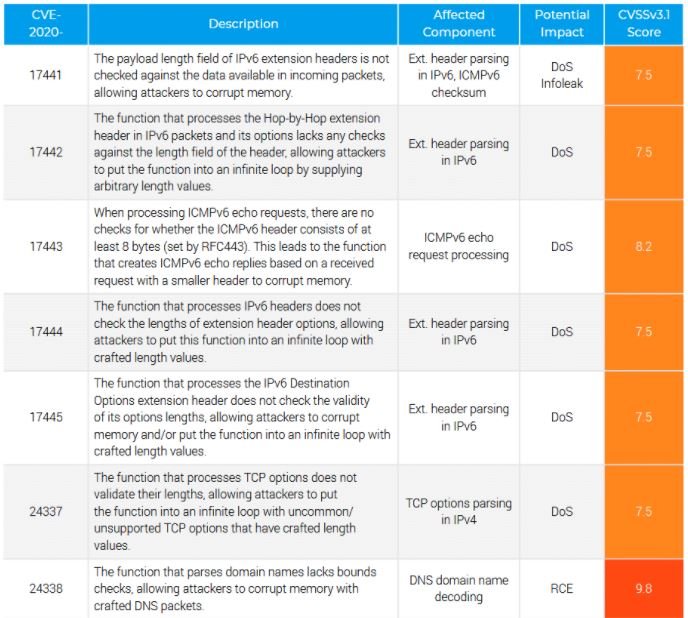
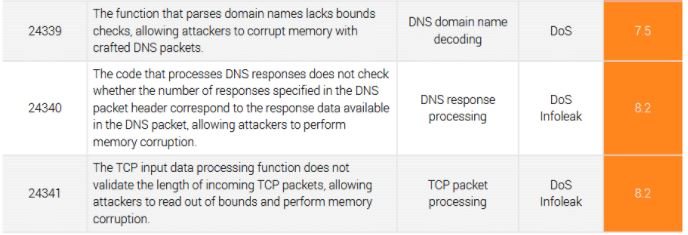
It should be noted that attacks vary depending on the target device and the type of network deployment. For example, by their nature, routers can be exploited remotely, as they are usually connected to a company’s external interface. Other devices, such as sensors and industrial equipment, depend on local access for abuse.
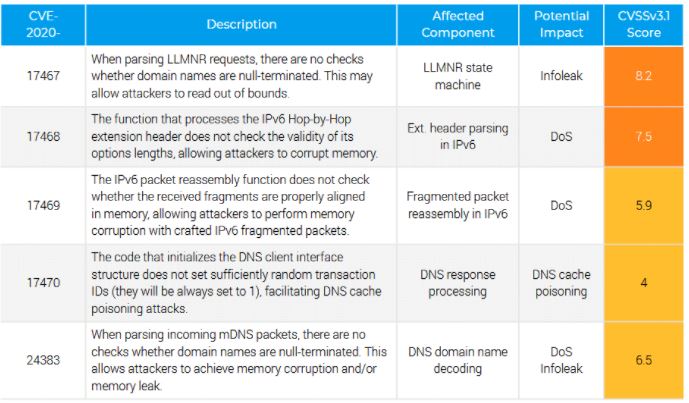
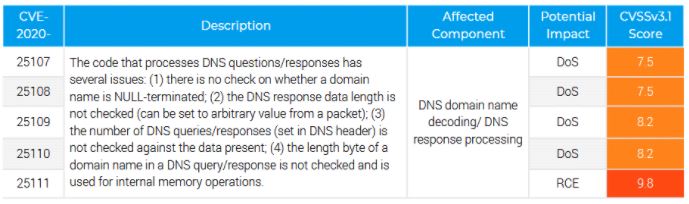
This finding was reported by the experts of the firm Forescout, who mention that this report is part of an investigation called Project Memory, in which the security mechanisms have been analyzed in 7 other TCP/IP stacks: “We found no faults in the lwIP, uC/TCP-IP and CycloneTCP stacks; although this does not necessarily mean that there are no failures in these batteries, we note that the batteries have consistent limits and generally do not depend on syntactic analysis,” the experts mention.
To fix the failures, affected device vendors must take the updated TCP/IP stacks and integrate them as firmware updates for their products. Although this is a relatively simple process in some products, many of the affected devices do not even have the ability to receive firmware updates, making it virtually impossible for manufacturers to fix the flaws.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











