Using a database of 380 million personal records, a hacker group has attempted to gain access to thousands of Spotify accounts. Hacking is the main problem that users of this music platform go through, as reports constantly appear about unauthorized login attempts, password changes or unusual recommendations.
The most common method for hacking a Spotify account (and other online platforms) is the credential stuffing attack, which involves using huge combinations of usernames and passwords to try to login to certain accounts. The security firm VPNMentor published a report on an exposed database with more than 300 million combinations used in an attack on Spotify.
According to experts, each record in this database contains a username (usually in the form of an email address), a password and its usefulness to successfully log into a Spotify account, as shown in the following screenshot:
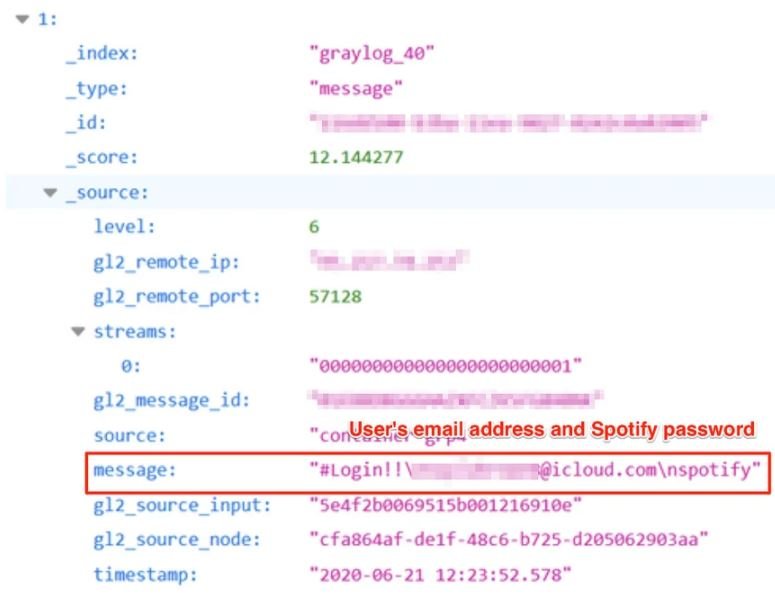
Experts are still unaware of how this information was collected, although it is most likely the result of previous data breach incidents. In a first estimate of the incident, experts estimated that between 300 and 350 thousand accounts; experts reported the incident to Spotify, which has already spoken out.
“In response to this report, we have implemented a continuous reset of all affected users’ passwords; as a result the database’s information will become completely useless”, Spotify’s release states. The incident occurred a few months ago, so Spotify has been confirmed to mention that the reset was performed last July.
Spotify does not have the multi-factor authentication feature, which could increase user security. The platform needs to implement some mechanism to strengthen its security.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











