A Cofense Intelligence report details the finding of a phishing campaign that uses the issue of COVID-19 disease to infect victims with a new version of the Hentai OniChan ransomware. Formerly known as King Engine, this variant filters victim data and charges a much larger ransom than other detected variants.
The infection campaigns that used this ransomware deployed it using phishing emails similar to those seen in enterprise email engagement attacks. In addition, threat actors continue to use data leakage to pressure victims of these attacks.
The malicious message, like the one shown below, was found in protected environments in sectors such as health. To overcome barriers to protection, threat actors argue that these messages contain information about COVID-19 tests from some patients. Coronavirus cases continue to accumulate in Europe, Asia and the Americas, so victims are likely to fall into this trap. Attackers use very common tactics to reach end users and deliver the Hentai OniChan ransomware, belonging to the Chimera malware family.
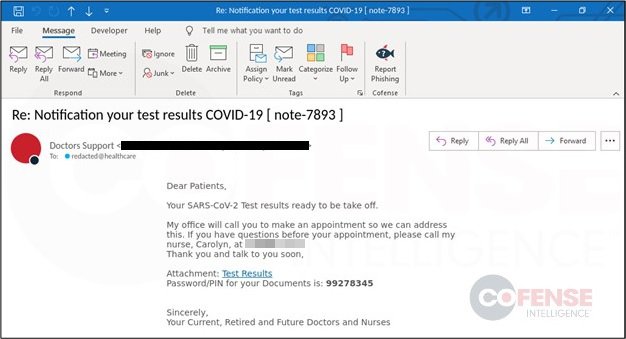
Experts mention that this campaign would have been detected last September, detecting environments committed to Proofpoint, Symantec, TrendMicro, Cisco, and more solutions.
The downloaded files contain components to run the ransomware that encrypts the victims’ files in addition to including an application to decrypt the information after paying the ransom. In their ransom note, threat actors explain how to decrypt the information and make the ransom payment in Bitcoin.
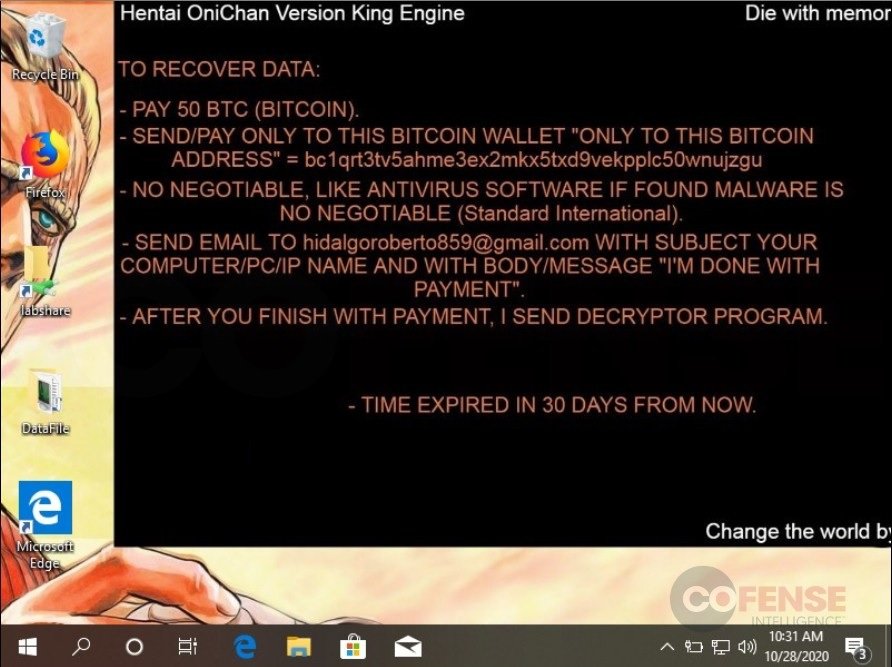
More and more ransomware operations are also using data theft as a strategy to get a payment. In its early stages, Hentai OniChan used a version of the Berserker malware that was unable to extract sensitive data; soon after, with the use of the King Engine variant, the operators of these attacks began stealing information and threatening to make it public.
As for this version, Hentai OniChan encrypts the files committed to the .docm extension and demands a ransom of 50 Bitcoin ($650k USD), while the previous version only charged 10 Bitcoin ($130k USD).

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











