Talal Haj Bakry and Tommy Mysk, cybersecurity researchers, have published reports on some security risks that could occur in previews of links sent across all kinds of online platforms.
According to experts, these flaws could affect users of Facebook, Instagram, WhatsApp, Discord, Twitter, LinkedIn, Slack and Zoom, generating IP address leaking, exposure of links sent in chats with end-to-end encryption, unnecessary download of data in the background, among other unusual behaviors.
These applications use a very specific approach to handling this data, which involves sending the binding in question to an external server on which the preview is generated. This server sends the preview to the sender and receiver, so it requires a copy of the information contained in the link to generate the preview.
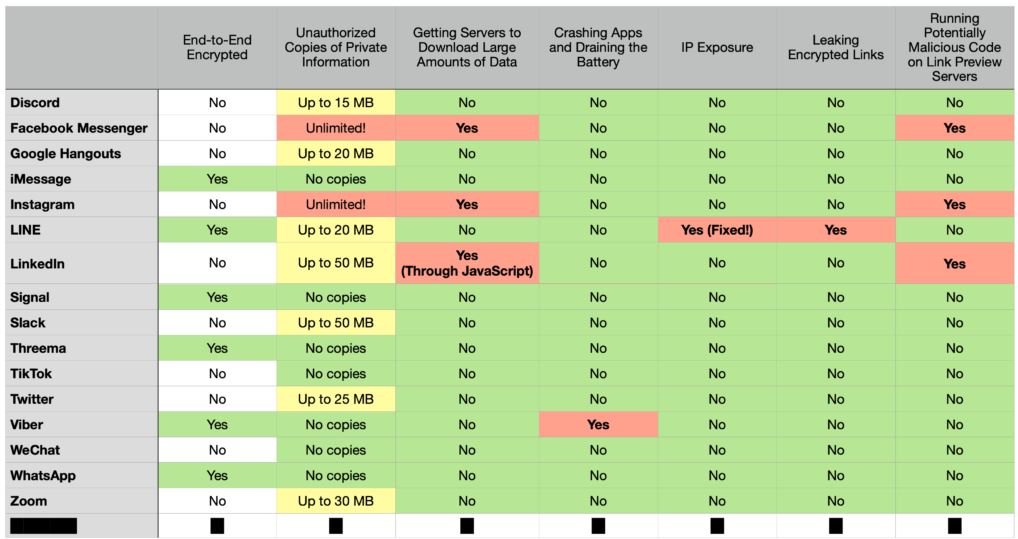
Researchers argue that this approach could be detrimental to user privacy, as the information contained in the link may contain sensitive data only for the recipient of the message, whether invoices, medical records, among other data.
Some applications have limitations on the amount of data collected and stored. However, popular apps like Instagram and Facebook Messenger have no limitations, so it is possible to download links up to 2 GB on various Facebook servers.
Several platforms like Slack have already taken action, setting a download limit of 50 MB, while LinkedIn has limited it to 30 MB. Still, the researchers point out those threat actors could get information from these links if they manage to compromise the platforms.
An approach that could prevent this behavior requires a summary and image to be downloaded from the website to which the link redirects. When the application on the receiving end receives the message, it will display the preview as sent by the sender without having to open the link at all. In this way, the receiver would be protected against risks if the link is malicious. This approach assumes that whoever sends the link must trust it, because it will be the sender’s application that will have to open the link.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










