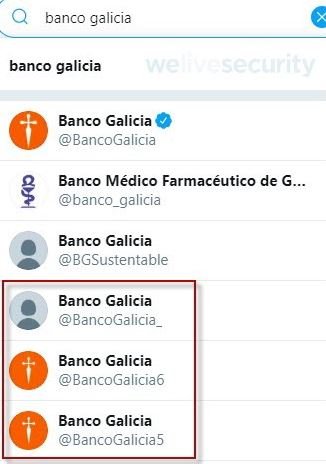
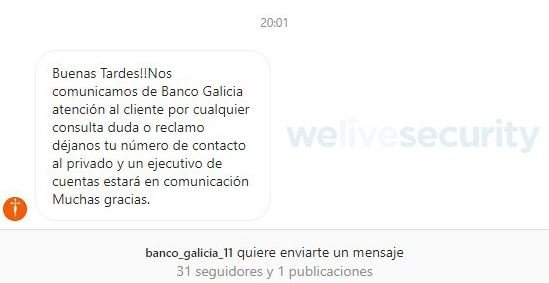
Experts from the security firm ESET revealed the detection of a new phishing campaign in which threat actors try to trick users by posing as social media accounts of renowned banks. Security expert Luis Lubeck recounts how he received a private message via Instagram from an account apparently operated by Banco de Galicia, Argentina’s financial institution.
The message provides personalized financial advice to the target user, although the real goal of the operators of these accounts is to obtain sensitive information from the victims, so users must remain alert to this attack variant.
As can be seen, messages are sent by accounts that use the official name and images of legitimate financial institutions, although there are clear signs of malicious behavior such as the low number of followers, the absence of account verification or the few posts made by the fake account.

Threat actors send generic messages that seek to attract the attention of users, who might be more likely to fall into the trap if they face real difficulties with their bank account. If the user responds to these messages, threat actors will begin to make excuses for the user to disclose confidential details, Lubeck mentions.
Threat actors have not only used the image of the Bank of Galicia, but have usurped the image of many other financial institutions, representing an increase of about 30% of security incidents in Argentina. The Bank of Galicia even announced the temporary closure of some of its social media accounts to prevent further incidents.
This is not a practice limited to Instagram, but similar campaigns have been detected active on other platforms such as Facebook or Twitter.
Users should consider implementing appropriate security measures, as well as never remembering to provide personal information from messages that arrive surprisingly via social media or SMS. Users can also notify banks about active scams.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.