Cybersecurity specialists report that the source code of Windows XP, the operating system released by Microsoft nearly 20 years ago, was filtered online along with Windows Server 2003 code. The leak was released on the popular website 4chan, where the information was published in torrent form, the first time this has happened with the source code of the operating system.
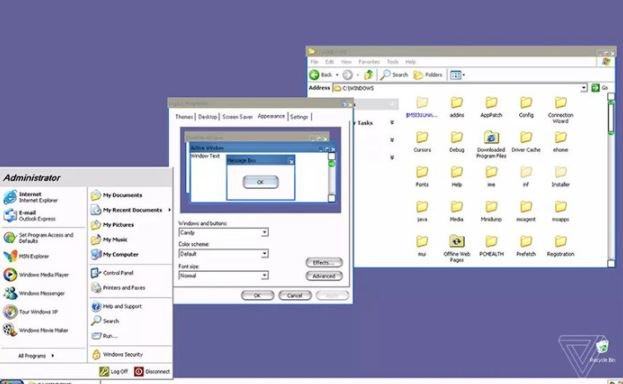
Despite being released a long time ago, Windows XP operates on more than 1% of desktops and laptops around the world, making this a significant incident.
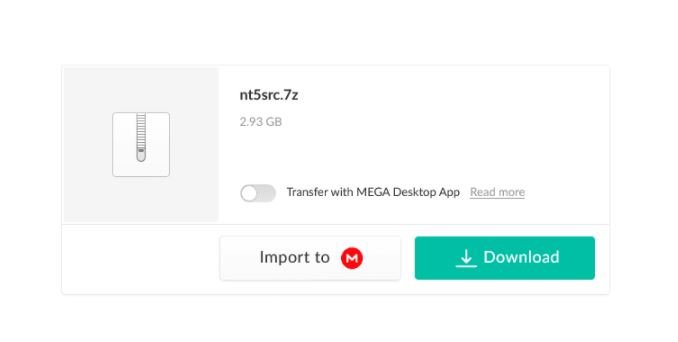
Reports mention that the torrent file set (with a size of 43GB) also includes the Windows Server 2003 source code, as well as information related to other older operating systems, including those mentioned below:
- Windows 2000
- Windows CE 3
- Windows CE 4
- Windows CE 5
- Windows Embedded 7
- Windows Embedded CE
- Windows NT 3.5
- Windows NT 4
- MS-DOS 3.30
- MS-DOS 6.0
Some users also claim that the leak also includes samples of the Windows 10 system source code, released in 2017, in addition to the source code for the first version of the Xbox console. The company has not commented on the incident, although multiple members of the cybersecurity community have already verified the legitimacy of the leak.
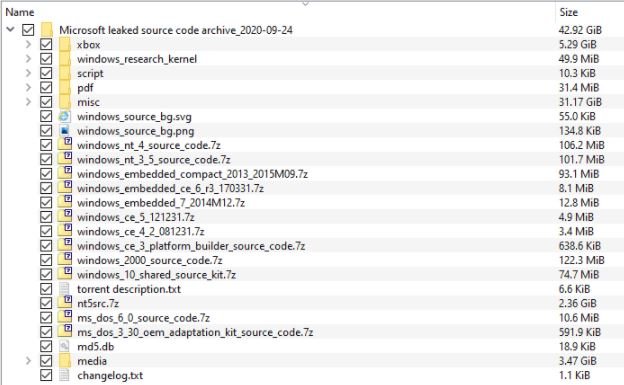
About the person responsible for the leak, this was done by a self called user billgates3, who claims to have compiled the source code during the most recent months because “everyone deserves to have access to this information”. This user also mentioned that many operating system source files have been shared among the hacking community for years.
Torrents also include a media folder related to various conspiracy theories about Bill Gates. The most possible explanation is that this information has been obtained from some government organization, as Microsoft often shares its source code with some governments around the world through a special program.
Microsoft stopped releasing support for Windows XP in 2014, so this incident does not make systems running the outdated version of the operating system a target, because there are probably already many unmediated vulnerabilities.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











