Cybersecurity specialists from vpnMentor have detected the leaking of a surveillance platform developed to track and monitor millions of coronavirus-carrying patients in Uttar Pradesh, India. It appears that multiple vulnerabilities within the platform left the information completely exposed to any security incident, especially in the context of the pandemic.
Threat actors reportedly compromised the exposed database by exploiting multiple vulnerabilities, including a flaw in an unsafe GitHub repository that contained usernames and passwords for administrator accounts on the platform. Although the researchers decided not to check if the exposed accounts are active, research was conducted to determine their authenticity by other methods. Noam Rotem, an expert at vpnMentor, has concluded that there is a data breach related to this incident.
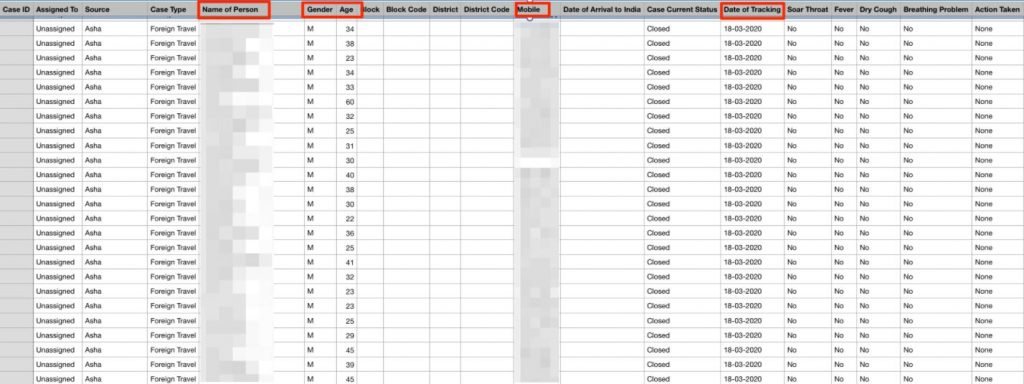
To be specific, this incident exposed a web index that lists all data related to coronavirus testing applied in Uttar Pradesh and elsewhere in India, amounting to more than 8 million records; this index was available to any user without authentication. The report was submitted in a timely and form to the Indian authorities.
As mentioned above, Uthar Pradesh is a state in northern India with a population of more than 200 million people; at the time vpnMentor reported the incident to the authorities, this area had more than 136,000 confirmed cases of COVID-19. Researchers believe that the database presented was developed by the Department of Health and Family Welfare in order to follow up on confirmed cases; experts believe the state’s IT teams would have made multiple mistakes in deploying the database, resulting in three critical vulnerabilities:
- An unsecure git repository was found revealing multiple technical details, including admin passwords
- The platform admin panel was accessible to anyone using the password mentioned above
- A separate index of CSV files containing daily COVID-19 patient reports, accessible without password or any other login credentials
As if that weren’t enough, the passwords listed had minimal protections, so they were easy to decrypt using dictionary attacks within the reach of any malicious hacker, not to mention that their extension did not go far beyond 4 digits, so a threat actor would not have had much trouble compromising an account.
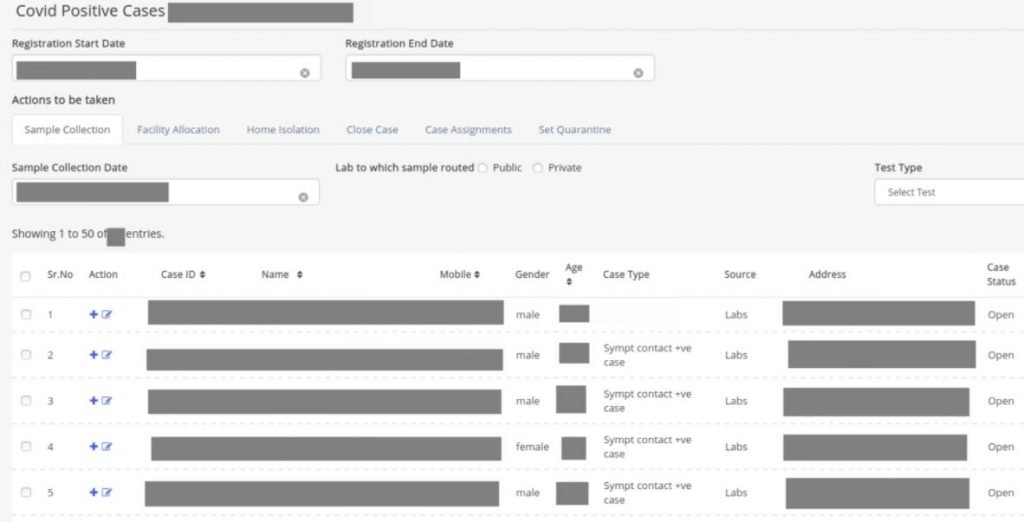
Security measures were so weak that any threat actor with access to the URL of this information platform could have easily accessed the admin panel, exposing all stored data and getting the opportunity to monitor patients and modify multiple data such as:
- User’s diagnoses
- Tests results
- Quarantine measures, among others
Among the personal identifiable data exposed during this incident are details such as:
- Full names
- Birthdates
- Addresses
- Phone numbers
Uttar Pradesh people’s health data was also compromised, including:
- Case identification keys
- Diagnosis information
- Symptoms
- Medical records
- How the patient contracted COVID-19
- Place of isolation or quarantine
The platform also includes an information section on members of the public health system positive for coronavirus throughout India.
As in other data breach incidents, affected users could be exposed to phishing attacks, bank fraud, identity fraud, or phone or email spam campaigns thanks to the large amount of personal information exposed. However, local authorities fear that this data could be used in a cyber-attack campaign against local government, as this is a trend that has shown considerable growth over the past few months.
Given the timing of the world and the kind of information exposed in this incident, experts believe this leak could cause greater problems than expected, even from lethal consequences.
Since the beginning of the pandemic, multiple groups of threat actors have managed to deploy ambitious fraud campaigns using this issue, offering fake vaccines or treatments to unsuspecting users, not forgetting that the fear patients might experience when receiving an unfavorable diagnosis makes them more vulnerable to falling into these traps.
Finally, threat actors could modify the diagnoses of millions of patients, which could spread an infection to levels where no government in the world could control it.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











