Introduction
Companies are spending thousand of dollars to detect malicious traffic in the Network and discover threats. Today we will talk about open source Maltrail, which is a malicious traffic detection system. This tool helps the Network Administrator to monitor traffic and discover the threats in the Network or on the Server.
Maltrail can be deployed in inline or transparent mode. For deploying it in transparent mode, port mirroring is required to be done in the network to detect the malicious traffic as Intrusion Detection System. Using this tool we can protect our network from cyber attacks.
Environment
- OS: Ubuntu 2020 64 bit
- Kernel version: 5.6.0
Installation Steps
- Use this command to clone the project.
- git clone https://github.com/stamparm/maltrail
root@iicybersecurity-VirtualBox:/home/iicybersecurity# git clone https://github.com/stamparm/maltrail Cloning into 'maltrail'... remote: Enumerating objects: 226490, done. remote: Total 226490 (delta 0), reused 0 (delta 0), pack-reused 226490 Receiving objects: 100% (226490/226490), 90.04 MiB | 3.86 MiB/s, done. Resolving deltas: 100% (184672/184672), done.
- Use the cd command to enter into maltrail directory.
root@iicybersecurity-VirtualBox:/home/iicybersecurity# cd maltrail/ root@iicybersecurity-VirtualBox:/home/iicybersecurity/maltrail#
- Next, use this command to install the requirements.
- sudo apt-get install git python3-pcapy.
root@iicybersecurity-VirtualBox:/home/iicybersecurity/maltrail# sudo apt-get install git python3-pcapy Reading package lists... Done Building dependency tree Reading state information... Done git is already the newest version (1:2.25.1-1ubuntu3). The following additional packages will be installed: python3-click python3-colorama python3-flask python3-impacket python3-itsdangerous python3-jinja2 python3-ldap3 python3-openssl python3-pyasn1 python3-pycryptodome python3-pyinotify python3-werkzeug Suggested packages: python-flask-doc python-jinja2-doc python-openssl-doc python3-openssl-dbg python-pyinotify-doc ipython3 python-werkzeug-doc python3-lxml python3-termcolor python3-watchdog The following NEW packages will be installed: ====================================================================================================SNIP============================================================================================================================== /usr/lib/python3/dist-packages/impacket/tds.py:778: SyntaxWarning: "is" with a literal. Did you mean "=="? if lmhash is '' and nthash is '' and (aesKey is '' or aesKey is None) and TGT is None and TGS is None: /usr/lib/python3/dist-packages/impacket/tds.py:813: SyntaxWarning: "is" with a literal. Did you mean "=="? if lmhash is '' and nthash is '' and (aesKey is '' or aesKey is None) and TGT is None and TGS is None: /usr/lib/python3/dist-packages/impacket/tds.py:813: SyntaxWarning: "is" with a literal. Did you mean "=="? if lmhash is '' and nthash is '' and (aesKey is '' or aesKey is None) and TGT is None and TGS is None: /usr/lib/python3/dist-packages/impacket/tds.py:813: SyntaxWarning: "is" with a literal. Did you mean "=="? if lmhash is '' and nthash is '' and (aesKey is '' or aesKey is None) and TGT is None and TGS is None:
- Next, use this command to start sensor python3 sensor.py
root@iicybersecurity-VirtualBox:/home/iicybersecurity/maltrail# python3 sensor.py Maltrail (sensor) #v0.24.22 [i] using configuration file '/home/iicybersecurity/maltrail/maltrail.conf' [i] using '/var/log/maltrail' for log storage [?] at least 384MB of free memory required [i] using '/root/.maltrail/trails.csv' for trail storage [i] updating trails (this might take a while)... [o] 'https://data.netlab.360.com/feeds/dga/bigviktor.txt' [o] 'https://data.netlab.360.com/feeds/dga/chinad.txt' [o] 'https://data.netlab.360.com/feeds/dga/conficker.txt' [o] 'https://data.netlab.360.com/feeds/dga/cryptolocker.txt' [o] 'https://data.netlab.360.com/feeds/dga/gameover.txt' [o] 'https://data.netlab.360.com/feeds/dga/locky.txt' ==================================================================================================SNIP================================================================================================================================ [i] opening interface 'any' [i] setting capture filter 'udp or icmp or (tcp and (tcp[tcpflags] == tcp-syn or port 80 or port 1080 or port 3128 or port 8000 or port 8080 or port 8118))' [o] running... sensor.py:1093: DeprecationWarning: PY_SSIZE_T_CLEAN will be required for '#' formats _cap.loop(-1, _loop_handler)
- Now, use this command to start maltrail server python3 server.py.
root@iicybersecurity-VirtualBox:/home/iicybersecurity/maltrail# python3 server.py Maltrail (server) #v0.24.22 [i] using configuration file '/home/iicybersecurity/maltrail/maltrail.conf' [i] starting HTTP server at http://0.0.0.0:8338/ [o] running...
- Open this link in the browser http://192.168.0.24:8338
- Successfully we got the login page.
- For logging into this web interface, default credentials are:
- Username: admin
- Password: changeme!
- After logging in, we started attacking the server by using the Nmap tool on another machine by using this command nmap -n –script-vuln 192.168.0.24
- Nmap will start’s scanning the target IP. Maltrail tool sensor will detect the attack on the server and show it in the tool’s web interface page.
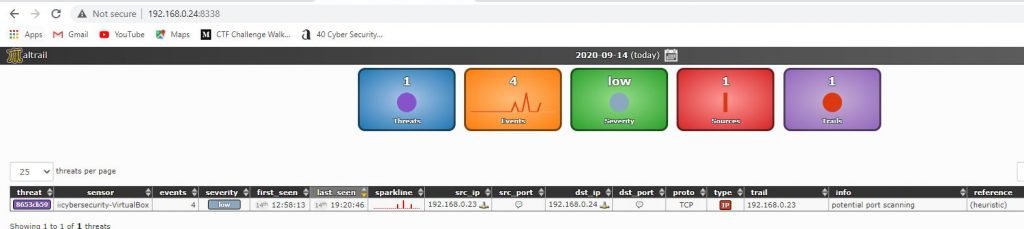
- Here, it shows the attack details number of threads, Events, security, sources, and trails details in the interface page.
- This also generates the log files in /var/log/maltrail at this location.
root@iicybersecurity-VirtualBox:/var/log/maltrail# ls 2020-09-14.log error.log
Conclusion
We saw on how easily Maltrail tool detected the malicious traffic on server, using this tool we can secure our network from the attackers.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











