Introduction
People always search internet to hide data and transfer it across to your friends. Imagine you get a MP3 file with your password in it. Now you can transfer any confidential file or data via audio file (MP3, WMA, WAV, APE). Later on same can be retrieved easily. Researcher of International Institute of Cyber Security comments “we have seen forensics cases where information is shared using these steganography channels“.
Using this we can also convert the MP3 extension to (.ape, .wav, and .flac). This application is very simple to use and easy to understand. Now we will move on to step by step tutorial on how to use DeepSound.
Environment
- OS: Microsoft Windows [Version 10.0.18363.1016], 64 bit
Installation steps
- Click Here to download the tool.
- It downloads zip file, extract the file.
- Next, run the DeepSound.exe file to use.
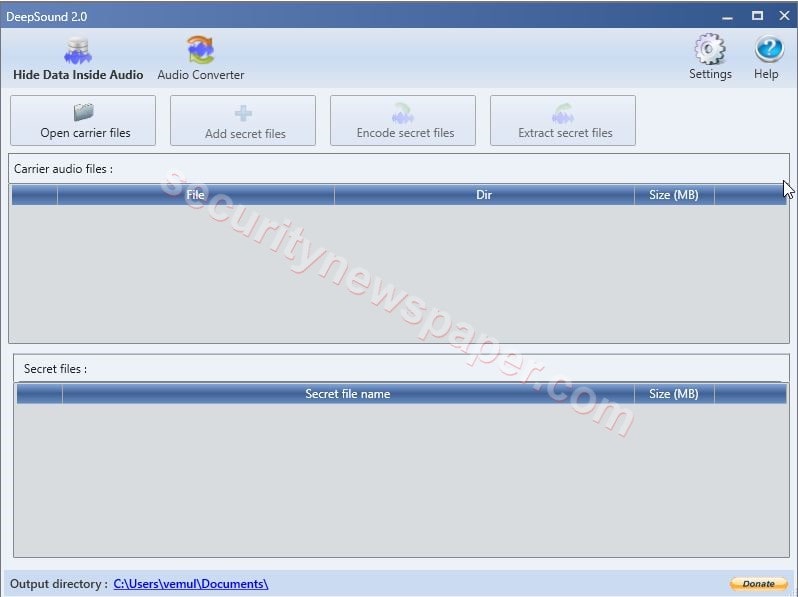
- Now, click on the “open carrier file”, to add any audio file of these extensions (.MP3, .ape, .wav, and .flac).
- Next, click on “Add secret file”, to add any confidential data files.
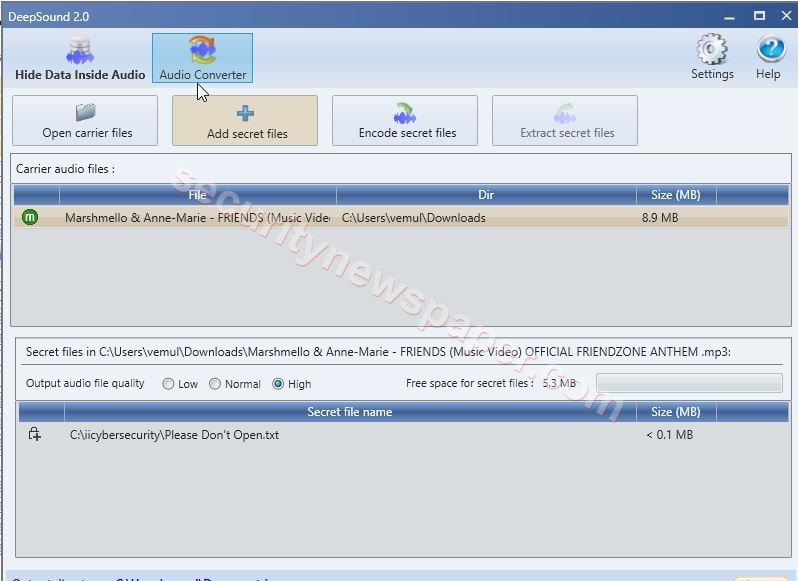
- Successfully added the audio and confidential file.
- You can also also select the audio quality.
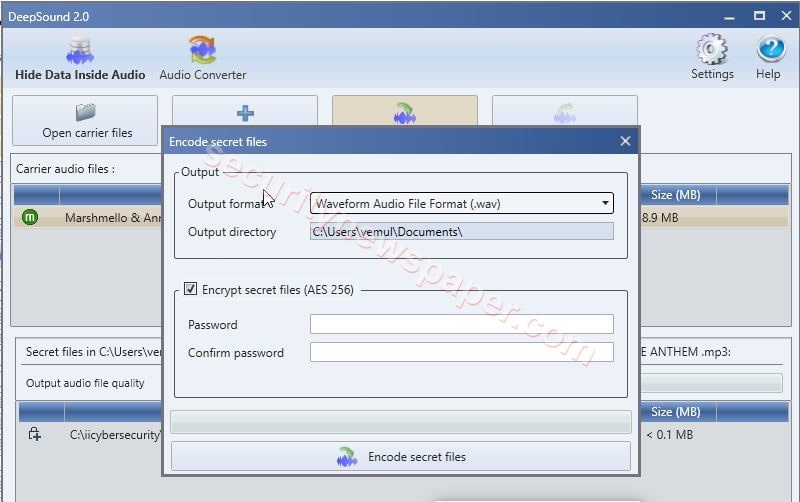
- Click on encode secure file, check the box Encrypt secret files and enter the password then click on encode secret files to secure the file.
- This will save the audio file on a specific path. The encrypted file will be as same as the original file.
Decrypt Audio File.
- Add encrypted audio file by clicking on an open carrier file, it will ask security passwords.

- Enter the security key and click on Ok.
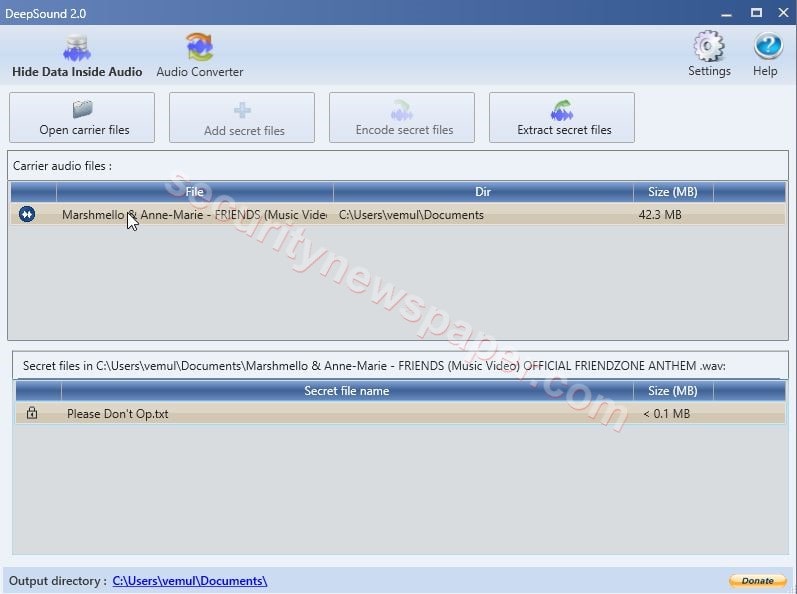
- Now, select a secret file and click on Extract secret files. This will download the secret file in our machine.
Change Audio File Extension
- Click On Audio Converter, add the audio file and select the extension then click convert
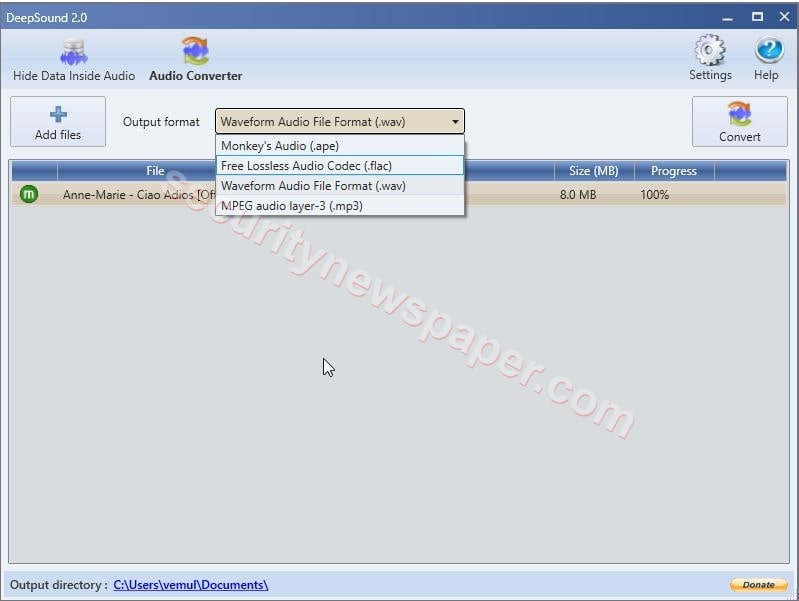
- The converted audio file will be saved at output directory path.
Conclusion
We saw on how to transfer or store any confidential data in any audio file. If we use this technique, no one can identify or steal your data and it’s best to transfer data file to any end-user. To find hidden data in audio file, some binary analysis is required.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











