Have you ever tried to check someone’s phone and failed? Well, worry not as there are a million others doing the same. Smart devices are developed by a team of experts thus making sure that there are not any loopholes. Despite all of it, developers coped up to intervene in the system without pulling any alarm.
Not all apps work as they need to be thus wasting time and money of users. Brands claim to be the best in the market but users end up in dismay. To help you get out of those failed trials, let me present you with the most authentic tool to keep an eye on someone’s phone. Let’s get in without any further delays.
Spyier: The Hidden Spying Assistant
Spyier is the pick of millions of users whenever they browse for how to spy on someone’s phone without them knowing for free. Spyier has made the process of spying on smart devices trouble-free. There is no need to learn programming skills as the easy user interface of Spyier makes using it easier.
Spyier is available online so that users can easily get the perks of using without any hassle. Just grab any internet-capable devices and start using Spyier on the go. The official webpage of Spyier has the option for Signup thus users can register and subscribe to the package as per the number of devices to spy.
Forbes, Android Authority, New York Times, Digital Trends, Life wire, and Top 10 Reviews are some of the top-notch media outlets which recognized the services of Spyier. The usage of Spyier over 190 countries is proof that users are restricted to a specific geographical area to use Spyier.

How Spyier works for multiple Operating Systems
Spyier provides the facility to track Android smartphones with Spyier without any extra efforts. It never required adding long user manuals but a live demo is available to help people get to know the way to use Spyier with its full efficiency. Spyier for android requires installation by touching the device.
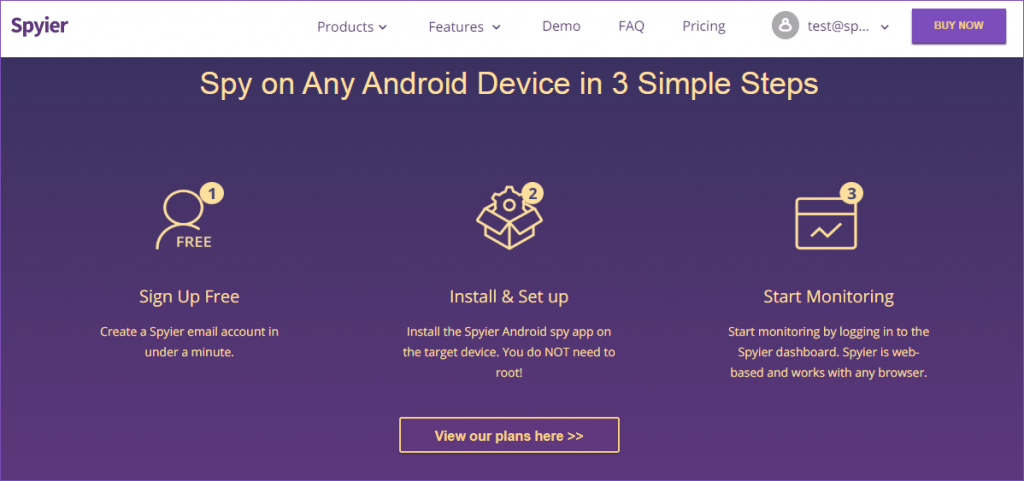
You would be eager to know how to spy on iOS devices. Spying is a cup of tea for iPhone and iPads as users make no extra effort. You would not be required to physically touch the device at all. The iCloud credentials are the entrance door to install Spyier to begin monitoring it round the clock.
Spyier can spy on any operating system without interrupting the processing of other applications. Installing Spyier does not risk virus exposure as it is developed to retain system security. Spyier executes in the background without generating any alerts thus users remain unaware of its presence.
How do Spyic Features are helpful to Secretly Spy on Cell Phones?
To pace up with your spying worries for your loved ones, this tool is the best option to consider. It does not take huge storage space as the 2MB setup goes unnoticed by the user. There are multiple other services that spy offers to monitor every bit of data stored on the target device while keeping your identity secret.
Spyier dashboard is the control panel of the device to be monitored without notifying the user at all. You will get all the details under the same roof thus no need to move your fingers to other applications. Here is a quick preview of how does Spyier helps its user to track smart devices:
- Track Cell Phone Location
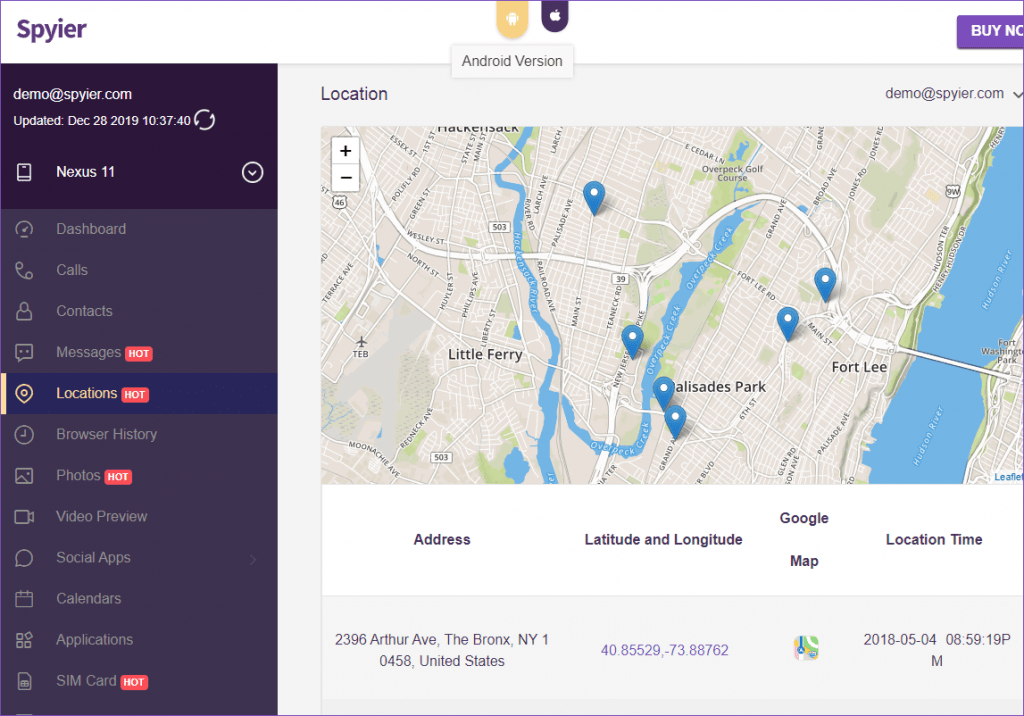
Spyier tracks the real-time location of the device it is installed on. You don’t need to follow someone, rather install this utility and you will get updates about their location. Spyier helps you to get proof of whether someone was hanging out with friends or attending meetings.
- Enable Geo-Fence Alerts
As the name suggests, these features create a borderline around the objective device. Whenever someone enters or leaves the specified zone you will get alerts. The virtual boundary points could be marked on Google maps to keep them safe from going to risky places
- Android Keylogger
People always prefer using a keylogger as it gets them everything types on the objective device. By keeping the user requirements in mind, the developers of Spyier have incorporated this feature as well. Now you can get serialized keylogger details for Spyier dashboard to get their login credentials.

- Check Browsing History
The Internet is the new hub of crimes as online predators are always in search of innocent faces to muck them. You can keep a track of how often a specific website was searched on the target device and even restrict the usage from the Spyier dashboard. Spyier gets the web-browsing history in a click for you
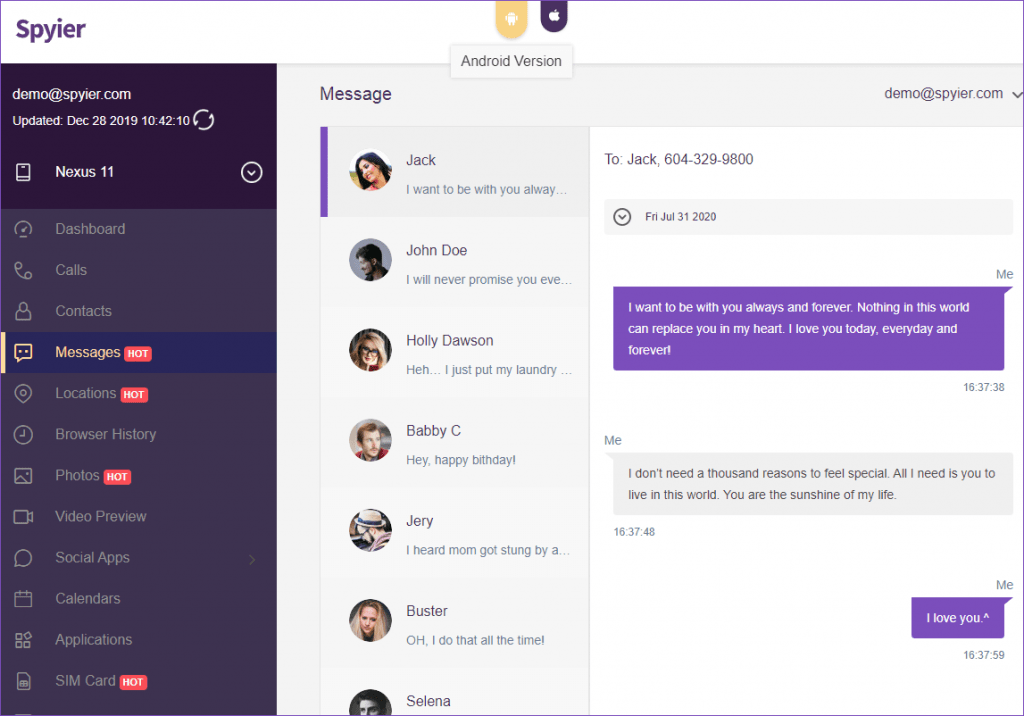
- Read Messages
If anyone is busy with messages round the clock then it must ring the alarm of being cheated on. However, there is no proof thus leading to a thought that you might be discerning wrong. Spyier provides the facility to read anyone’s conversations by clicking on the Messages tab on the Spyier online dashboard.
- Check Installed Application
We are well aware that people do not use a single account but they try creating multiple fake accounts, add random friends, and chat with them for hours. You do not need to be worried over this as Spyier would help you to check applications installed on the smart device as well as the accounts logged in there.
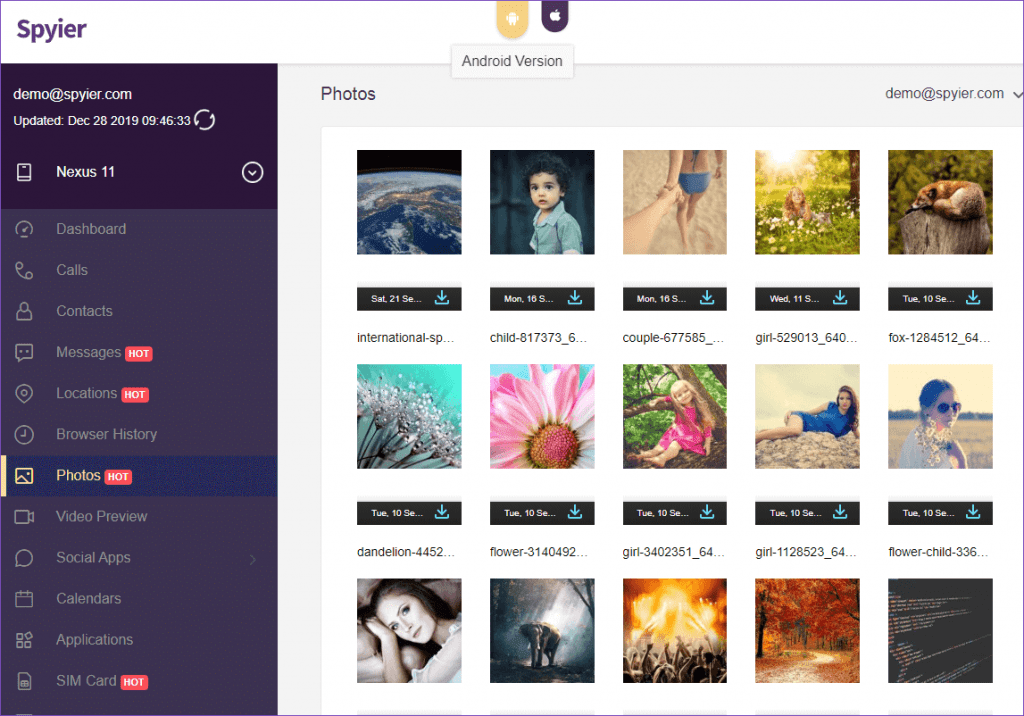
- Preview Gallery
Images and videos access is another useful yet easily accessible feature provided by Spyier. All you have to do is log in to your Spyier account, open dashboard, and click the tab and you are done. You can even preview the deleted images as Spyier keeps a record of each and everything saved in the objective device.
- Check Call Log
Checking the call history has become a left-hand job with Spyier. Not only this, but users can check the contact details, call duration, and the favorites list. There is no need to touch the target device as all rather you can access call details from Spyier web-based dashboard.
To Conclude
There is nothing that goes unnoticed by Spyier while stealthily tracking someone’s cell phone. No matter how much security measures are used by the target system, Spyier always makes a way to fetch the information. You can keep your identity secret by using Spyier as it utilizes stealth mechanisms while spying over smart devices.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











