According to cloud security course specialists, the Electronic Frontier Foundation (EFF) presented a database detailing the methods used by law enforcement organizations for city surveillance, although some prefer to call it espionage. The EFF describes this “Atlas of Surveillance” as the largest collection of information on surveillance technology.
Representatives of this civil association say that the database was created to help technology users understand how authorities across the United States use surveillance tools systematically.
This interactive map features thousands of data points extracted from more than 3,000 police departments across the country. Users can approach different locations and find brief reviews of the technology used by each department, as well as track geographical areas with the greatest presence of surveillance systems.
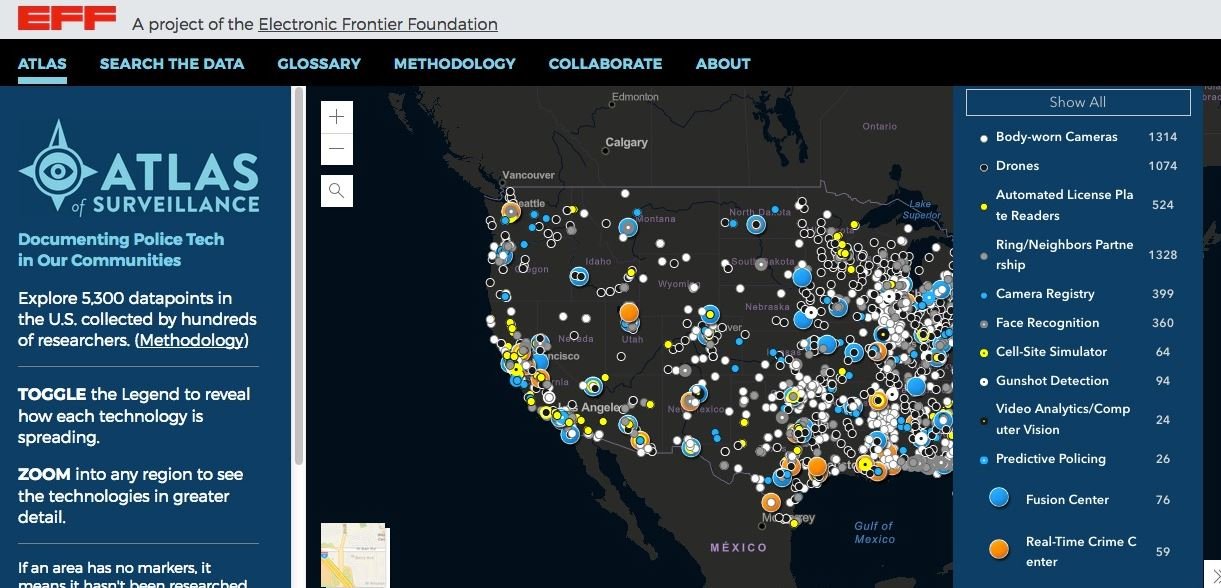
Cloud security course experts point out that this map also has indicators on specific and emerging technologies, including the use of drones, license plate readers, facial recognition cameras, Ring implementations, and use of a new technology known as “predictive surveillance,” which uses statistics and machine learning to try to detect potential criminal incidents.
It is also possible to search for information from thousands of local police departments, including data collected by federal agencies on the performance of programs implemented by each department.
In a statement, EFF states: “The Atlas of Surveillance documents the disturbing increase in the use of sophisticated tools for collecting people’s data in all kinds of environments, which the authorities leverage to create personal records with the excuse of preventing criminal activity.”
This map was created from a crowdfunding initiative, mentioned by cloud security course experts, so developers hoped to ensure the independence of this project from any government entity.
“The prevalence of surveillance technologies in our society offers many challenges related to privacy and freedom of expression, but it is one thing to know in theory, and another to see the data on a map”, concludes the message of the civil association.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











