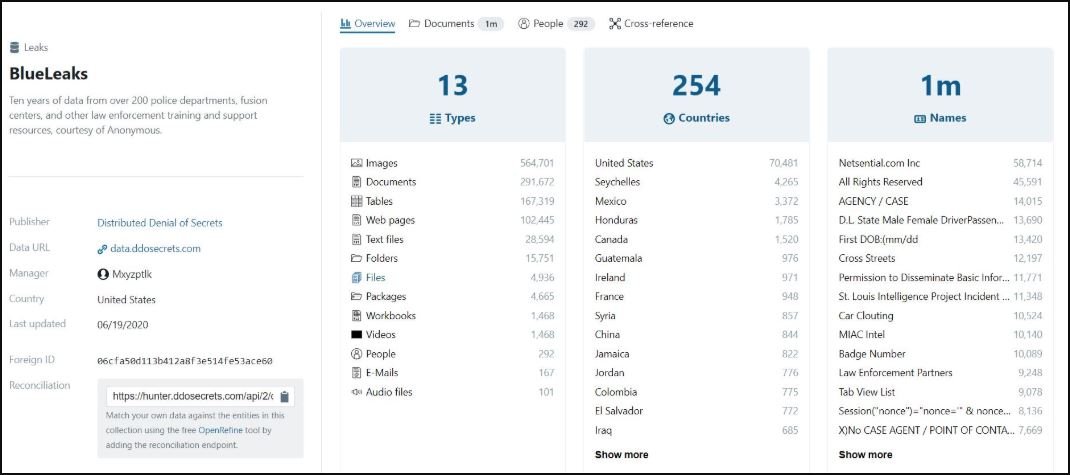
German authorities have taken control of a server hosting the BlueLeaks leak, a nickname that knows a database of more than 260 GB extracted from multiple U.S. police corporations.
BlueLeaks is also the name by which a website similar to WikiLeaks is known, hosting thousands of stolen documents. The server that the authorities seized belongs to an activist group known as Distributed Denial of Secrets (DDoSecrets), which has been linked to the publication of data related to justice agencies.
This week, Emma Best, a researcher and co-founder of DDoSecrets, mentioned that German prosecutors confiscated the hacktivist’s main public download server: “We have received official confirmation that #DDoSecrets’s main public download server was confiscated by German authorities,” Best said via his Twitter account.
The activist claims that the sole purpose of this server was to distribute public data, so it was not connected to the sources responsible for the leaks.
Regarding the source of the leak, Best assures that the data was obtained by the hacking group Anonymous, including emails, scanned documents, arrest notifications, police training materials, among others.
DDoSecrets made it accessible on a website on June 19. Four days later, Twitter permanently blocked the official DDoSecrets account, as it openly shared information from BlueLeaks. Twitter management claims that the organization violated the platform policy regarding sharing private data links or material related to hacking incidents. Stolen data may be used for malicious purposes, which also goes against Twitter’s usage policies.
The authorities claim that BlueLeaks’ data belongs to Netsential, a U.S.-based company that provided hosting services to multiple law enforcement agencies. A few weeks ago, the company revealed that its servers were compromised, so its website would be taken offline for an intensive maintenance period.
Despite setbacks, DDoSecrets members say they won’t stop working, and are even planning how to share this information without relying on traditional Internet platforms.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











