As the use of Internet of Things (IoT) devices in home environments grows, so do reports of security and privacy risks. Blake Janes, a computer science student at Florida Tech, revealed the finding of what he called “systematic design flaws” in the smart cameras and doorbells of Nest, Ring, SimpliSafe and eight other companies; these flaws would allow a supposedly deleted shared account to remain active and with full access to video streams.
This finding was published by Janes and two of her colleagues in the document “Never ending story: Authentication and Access Control Design Flaws in Shared IoT Devices”.

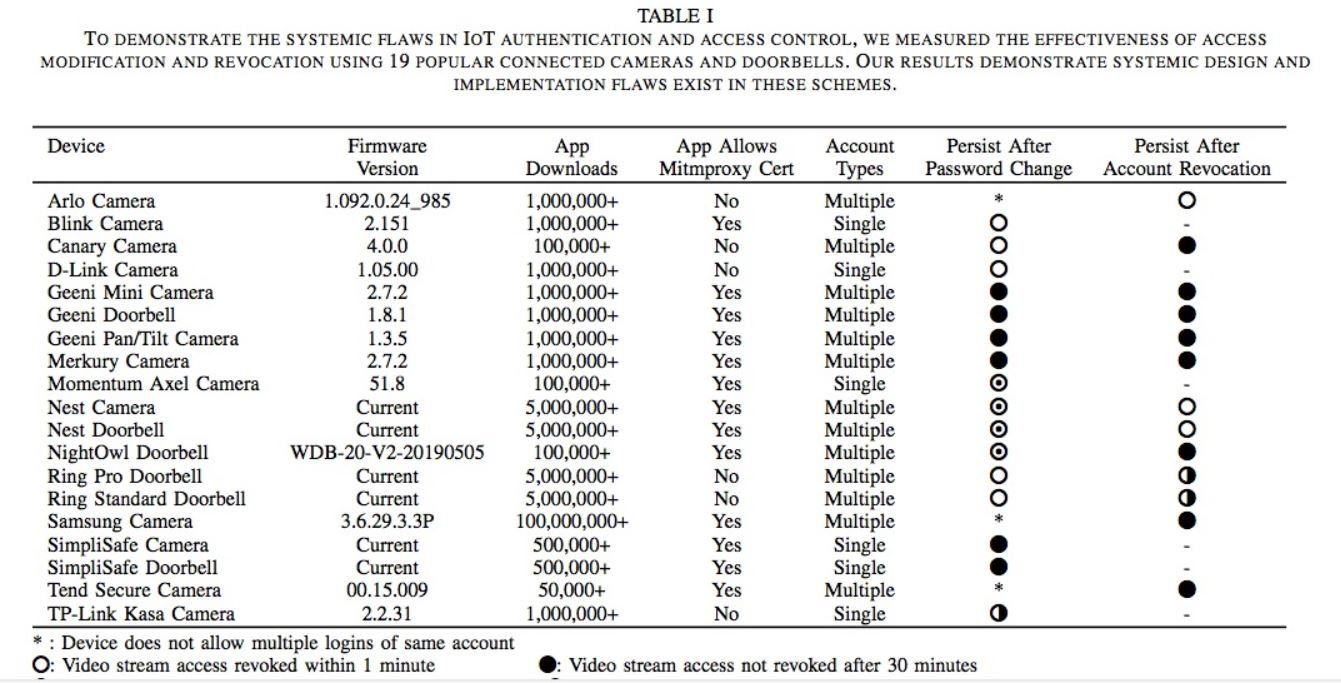
The young researcher found that the mechanism for removing user accounts does not work as it should on many of these devices, as active user accounts are not deleted. This condition would allow threat actors to exploit the flaw and gain access to the system with the ability to record audio and video without the administrators of the affected devices being able to detect this activity.
“Think of this: a couple who shared the same home is divorced; both have access to their surveillance system and Subject A removes the access for subject B, although this action is not replicated to Subject B’s smartphone. This means that even though Subject A revokes other accesses and resets the password to access the device, Subject B will still have access to the camera data, including audio and video streaming,” Janes says.
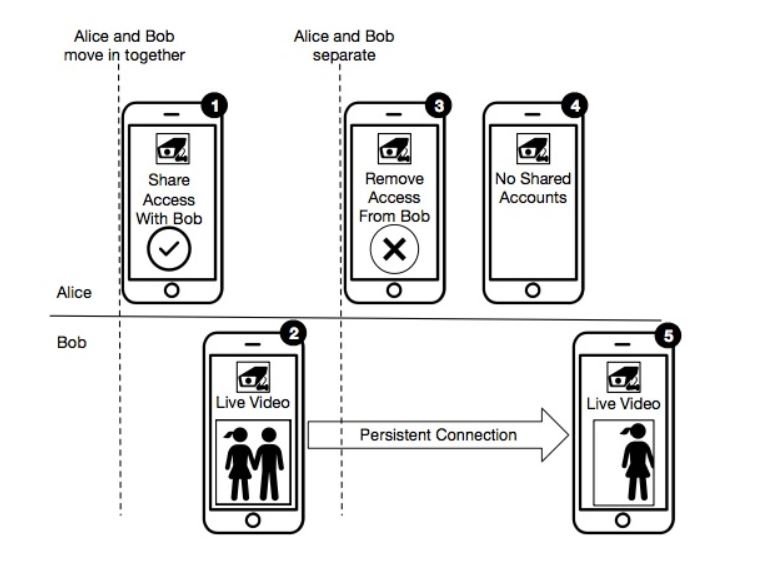
Researchers attribute this behavior to the fact that the granting of access is done in the cloud and not on-premises (using mobile apps from surveillance systems or web management interfaces). According to the International Institute of Cyber Security (IICS), the companies decided to take this approach because it allows cameras to transmit data without the need to forcibly use a smartphone. In addition, these devices were designed so that users did not have to respond to frequently access requests, as this increases the time required to access the data transmitted by the camera, something counterproductive as it is a system of this nature.
One of the most disturbing factors about this finding is the fact that threat actors would not require using sophisticated hacking tools to access the transmissions of these cameras, as only any application or user interface is needed.
Companies whose products contain this error include Blink, Canary, D-Link, Merkury, Momentum Axel, Nest, NightOwl, Samsung, SimpliSafe, TP-Link. Users of compromised devices must remain alert to install firmware updates released by manufacturers. Verifying your device settings is also a good preliminary measure.
Manufacturers whose products are affected by these flaws have already been reported and are working on implementing appropriate strategies to correct them. In addition, Google gave a reward of more than $3,000 USD to investigators for identifying an additional flaw at Nest; for their part, firms such as Samsung and Ring will correct the flaw in collaboration with researchers.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











