Specialists in the hacking course of cybersecurity firm Wordfence recently reported a critical zero-day vulnerability in Elementor Pro, a popular WordPress plugin installed on around 1 million websites. According to the report, this flaw was being actively exploited in conjunction with other vulnerability present in Ultimate Addons for Elementor, plugin used on more than 100,000 websites.
The plugin developers released an update after the report. Vulnerable website administrators are asked to update to the latest versions of the plugins; for Elementor Pro, that’s version 2.9.4 and in Ultimate Addons for Elementor, it is version 1.24.2.
Below is an overview of the two vulnerabilities found, in addition to their respective scores and identification keys in the Common Vulnerability Scoring System (CVSS).
CVE-2020-13125: This vulnerability is present in Ultimate Addons for Elementor, a plugin that works as an Elementor extension, adding multiple additional widgets. One of these widgets adds a registration form on any WordPress site; the flaw allows users to register even if this feature is disabled or if the form widget is not actively used.
Developers registered nopriv and regular AJAX actions linked to the get_form_data function to provide functionality for the User Registration Form widget.
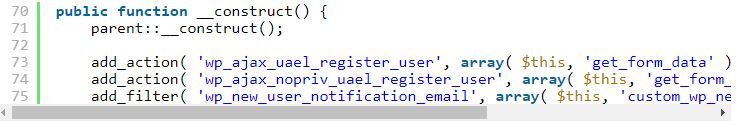
While analyzing the get_form_data function, hacking course experts noted that it was designed to retrieve the information presented on the registration form. This data was used to create a new user on the site using the wp_insert_user link. Nowhere in the feature does user registration verify that user registration form is not enabled on the site, nor are alternative checks performed to verify that the registration form widget was active.
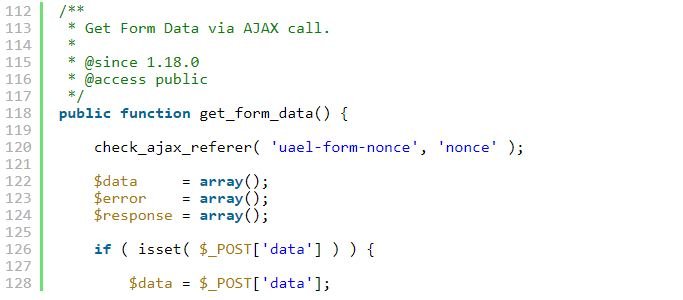
The lack of these checks makes it possible for threat actors to dodge user registry settings on the vulnerable site.
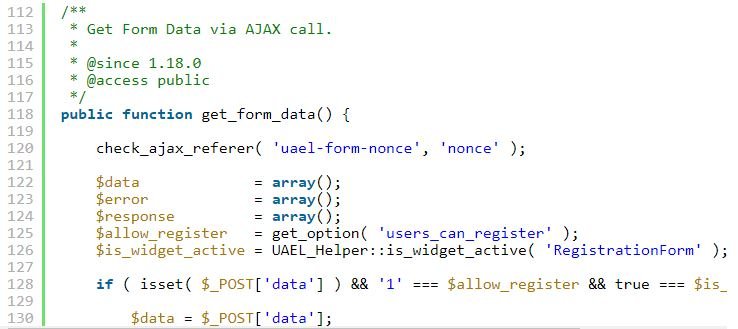
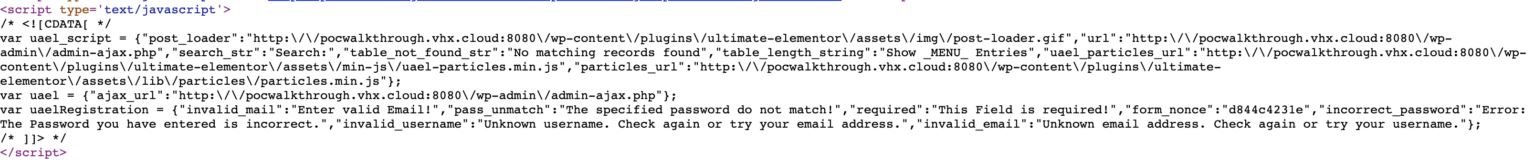
The Nonce record is always displayed
Although these logs are used to mitigate cross-site request forgery (CSRF) attacks, they can also act as a security feature in cases where a function contains a small flaw, that is, if an attacker cannot discover the error. The get_form_data feature uses nonce verification that might have stopped the registry of unauthorized users. The hacking course experts found that form_nonce was always visible in the source code of a page where a UA was enabled for the Elementor widget, even when there was no form present on the page.
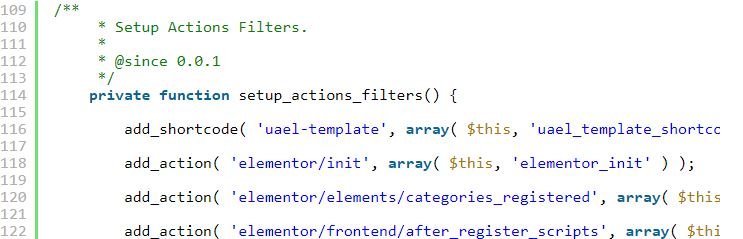
This means that a hacker only needs to scrape the source code of the pages on a site that runs the vulnerable plugin for var uaelRegistration. If that site had at least one widget in use on any page, they would be granted a usable nonce to register on the site.
The combined exploitation of the two flaws allows any hacker to register as a subscriber on a vulnerable site, which could be exploited to perform subsequent attacks that require subscriber-level access. The vulnerability received a score of 7.2/10 on the CVSS scale, so it is considered a high-gravity error.
CVE-2020-13126: On the other hand, this vulnerability resides in Elementor, one of WordPress’ most popular plugins. Elementor Pro, its Premium version, is used by about one million websites and has almost 50 additional widgets.
When a plugin has the ability to upload files, appropriate security measures should always be included to prevent unauthorized users from uploading files or bypassing any file or privilege filters on the site. Unfortunately, “Custom Icon” loading functionality in Elementor Pro does not have the appropriate security measures. A threat actor could take advantage of this condition to load malicious files, such as shells or backdoors.
According to the experts of the hacking course, Elementor Pro registers an AJAX endpoint used to activate the icon loading function. Neither the AJAX action nor the upload function is permission-checked, allowing any authenticated user the ability to activate the feature and upload a .zip file.
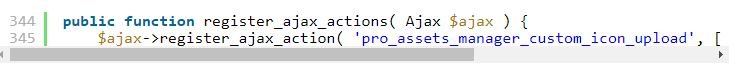
Upload files without verification
The custom icon upload feature was intended to allow only .zip files that were created from fontello, IcoMoon, or Fontastic icon creation sites. However, the plugin never checks to see if additional files have been included in those .zip files.
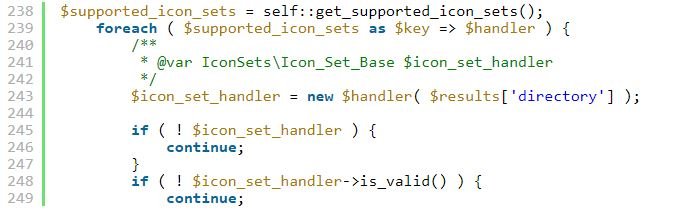
This allows hackers to include malicious files in a .zip file loaded as an icon, avoiding the restrictions present in the plugin.
A nonce check in the function was present, but as in Ultimate Addons, the nonce was easily detectable, as it was included in var elementorCommonConfig as “ajax”.
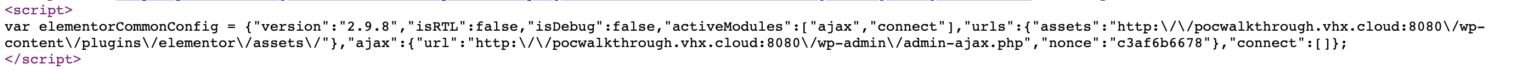
A threat actor might find a usable nonce by scraping the source of the /wp-admin dashboard page while authenticated. This could be used as a legitimate Elementor AJAX element to execute the vulnerable action and load specially designed .zip files. The vulnerability received a 9.9/10 score on the CVSS scale, so it is considered a critical flaw.
For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











