Zerodium is a cybersecurity company specialized in the purchase of exploits that a few years ago caught the attention of the community due to a million dollar offer for a jailbreak for the browser-based iOS system. According to specialists in a hacking course, the company has just announced that it will stop paying for some security bugs on iOS, due to the oversupply.
“We will stop acquiring new Apple iOS exploits (local privilege escalations, remote code execution in Safari, and sandbox evasion) over the next two to three months due to the large number of reports we receive related to these attack vectors,” the company’s announcement says. Zerodium also mentions that the value of one-click attack chains on iOS could also collapse in the near future.
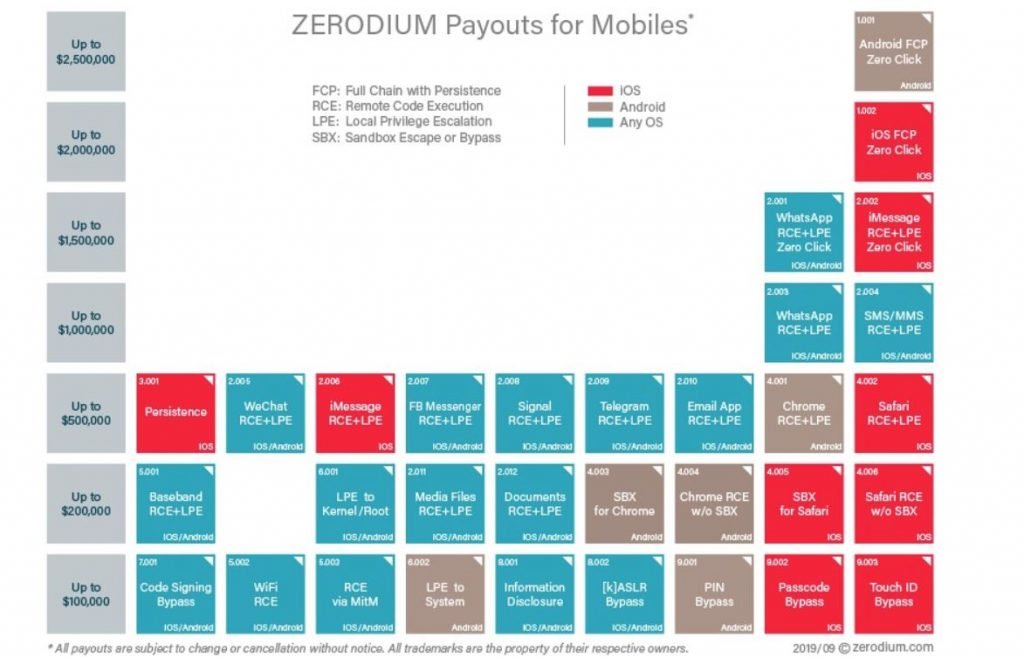
Zerodium also published its updated price list: From now on, the company will reward remote code execution errors and local privilege escalations with payments of up to $500k USD. More complex iOS exploit reports, such as persistent zero-click failures, could be rewarded with up to $2 million USD, as mentioned by experts from the hacking course.
Regarding the reasons that led Zerodium to make this decision, Chaouki Bekrar, founder of the firm, mentioned: “Security on iOS is a disaster; we have encountered multiple zero-day vulnerabilities that are exploitable on all iPhone or iPad models. I just hope that iOS 14 will be more secure.”
For experts from the hacking course, iOS 13 is an operating system highly prone to show security flaws, so the company has invested great resources to make its next operating system more secure. Version 13 of iOS has had 12 security updates since its release in September 2019. Demand for iOS vulnerabilities has dropped dramatically since that month, when Zerodium announced that it would pay higher rewards for security flaws in the Android operating system; until then, the company offered better payments for bugs on iOS.
Another factor that contributed to Zerodium’s lack of interest in iOS flaws is that Apple decided to publicly open its vulnerability bounty program. Until then, researchers could only participate in Apple’s invitation rewards program.
Both companies were consulted, although they have not responded so far. For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











