The 2019 cybersecurity community was surprised by the emergence of Astaroth, a Trojan developed for information theft that quickly became one of the most popular malware variants. Now, cloud security course experts point out that this malware has evolved to add anti-malware and anti-security analysis controls, making it an extremely stealth variant.
Apparently, Astaroth’s highest concentration of activity is in Brazil. Although researchers have so far not mentioned the likely causes of this behavior, this is an advantage, as experts can continue to investigate this malware before it spreads to more countries.
Cofense’s cloud security course experts were the first to detect malware nearly two years ago, although reports from IMB and Microsoft researchers have also emerged. With each new report, experts noticed new features in malware, infection chain improvements, and increasingly complex evasion capabilities.
In one of the most recent reports regarding Astaroth, Cisco Talos experts claim that malware follows a process of constant evolution. As at startup, the Trojan is still distributed by sending spam emails, although experts point to the emergence of two new features.
One of Astaroth’s new features is a collection of anti-sandbox and anti-security scanning controls; the Trojan runs these checks before running itself, making sure it is running on a real computer and not in an isolated environment. Thanks to this feature, Astaroth operators prevent payloads from being identified as malware, so infection levels will remain very high and victims and security companies will have fewer resources to identify these infections. “This is a very difficult malware to analyze,” concludes the report of cloud security course experts.
The second of Astaroth’s new features detected by researchers is the difficulty in stopping their communications with their command and control (C&C) servers. Malware developers added descriptions of random YouTube channels to hide the URL from their servers.
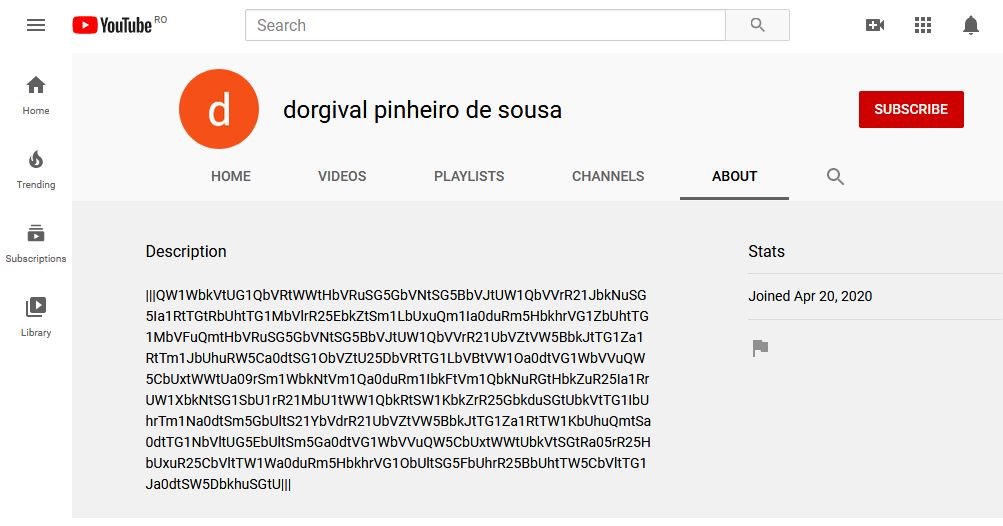
The report mentions that, after Astaroth infects the target system, the Trojan connects to a YouTube channel and extracts its description. After encoding this text, the malware receives new instructions and sends the extracted information from the target system for storage in a location controlled by the hackers. Other malware variants, such as Janicab, have employed similar techniques to hide previously. However, experts point to its presence in Astaroth’s code as a sign of the level of sophistication of the Trojan’s creators.
For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











