One of the most notable behaviors during the weeks of social estrangement and work from home has been the use of remote communication tools, such as the Zoom video conferencing platform. However, GDPR training experts have also uncovered multiple security flaws that could expose users of these services.
The most recent Zoom-related finding relates to a phishing attack in which threat actors pose as invitation notifications to a video conferencing session, asking the target user to join a call for work reasons. For this, potential victims will need to register and log in to a Zoom phishing page, so that cybercriminals will be able to extract their login credentials.
A report by Abnormal Security GDPR training experts mention that threat actors try to take advantage of the uncertainty that thousands of workers go through, as most of these phishing notifications relate to alleged HR departments that notify the target user of their dismissal.
As in any other phishing campaign, hackers create a legitimate-looking page and email address with compelling messages for potential victims. Because many users do not have cybersecurity knowledge, they are highly likely to fall into the trap.
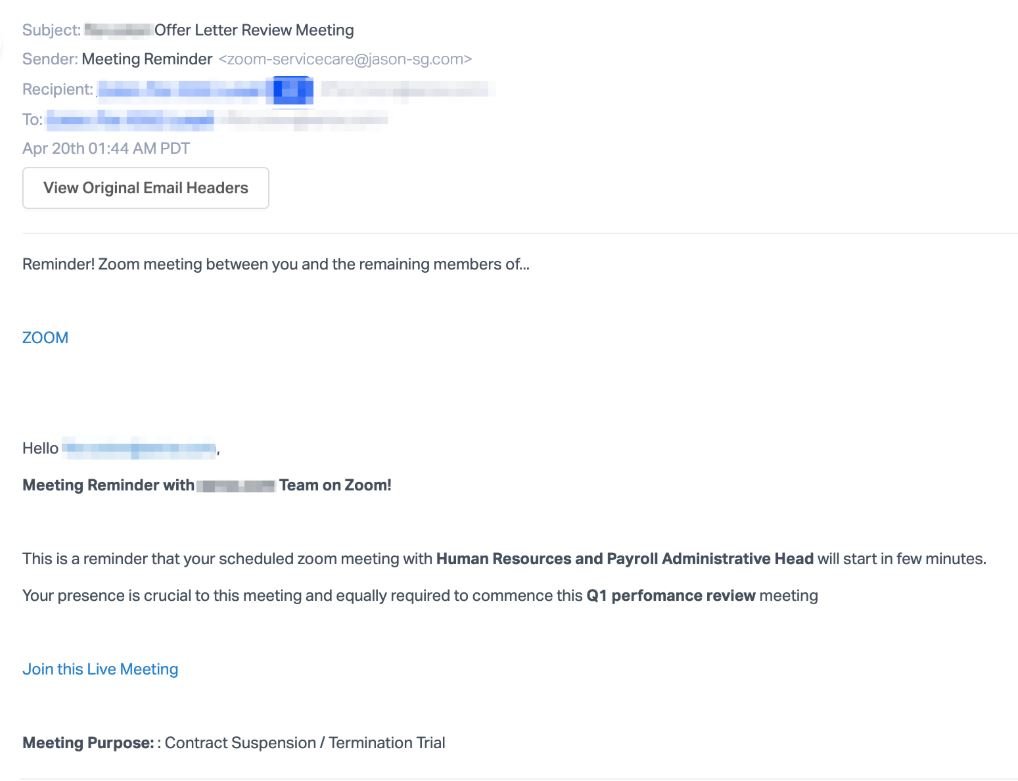
The message received by the target user contains a link to the fake Zoom page (with address zoom-emergency.myftp.org), where you are prompted to log in. Links to the phishing page are hidden in the text used in automatic meeting notifications such as “Join this live meeting”.
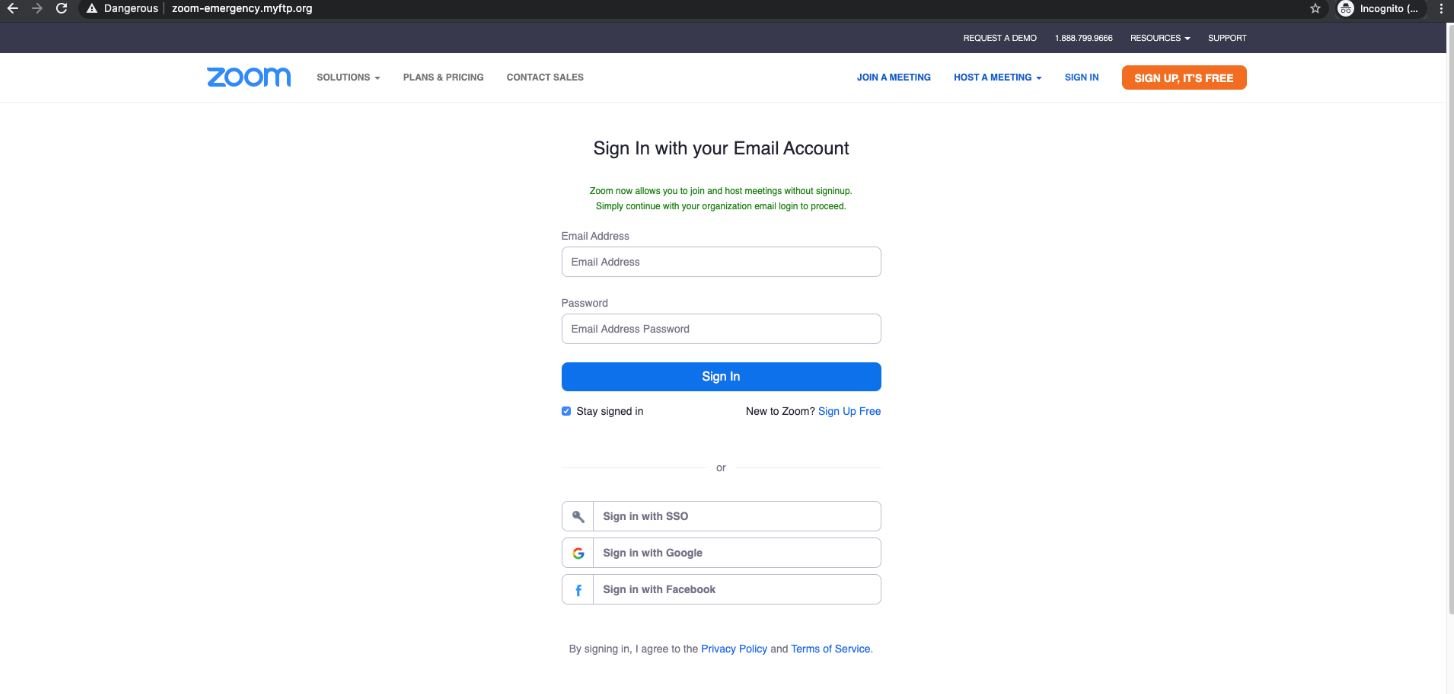
If the attack is successfully completed, the threat actors will be able to extract the login credentials of the victims, thus compromising any information stored in the Zoom account of the affected users, as mentioned by GDPR training experts.
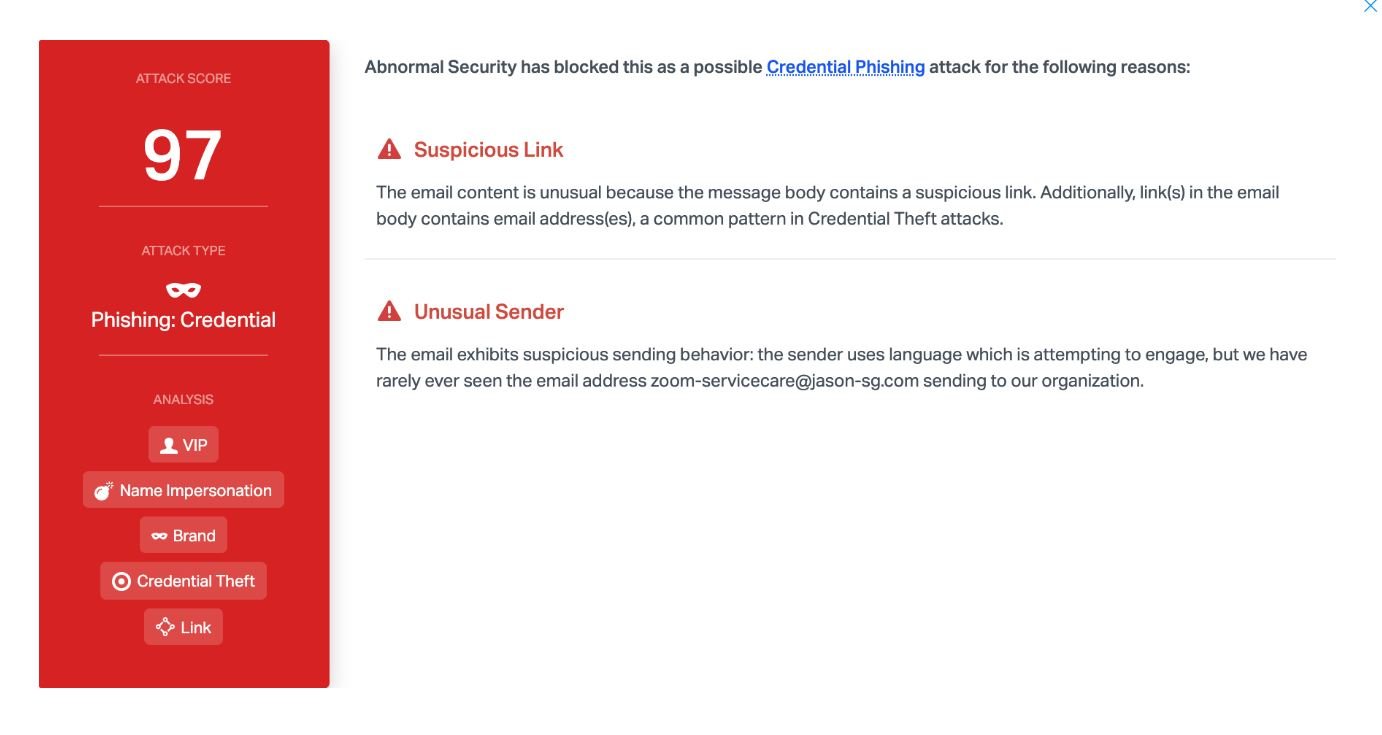
According to the International Institute of Cyber Security (IICS), this phishing campaign is highly effective because of the context in which it is being carried out. Thousands of companies are experiencing serious economic hardship, so workers know that the risk of losing their jobs is real. In addition, both the appearance of the fake site and the wording of the message have detailed elaboration, so it is not complicated for the hasty employees to expose their credentials of access to the hackers.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











