Last week, the web application penetration testing team at cybersecurity solutions firm Sophos received a report on an XG Firewall implementation that presented a visible suspicious value in the management interface. After conducting an investigation, the company determined that this was an attack on its physical and virtual firewall drives.
Apparently, the attack affected systems configured with the management interface and user portal exposed in the WAN zone. In addition, manually set firewall deployments are also affected.
Regarding the attack variant used by threat actors, web application penetration testing experts mention that a pre-authentication SQL injection vulnerability was exploited to gain access to exposed firewalls. Data stolen from any affected firewall includes the local usernames and hash passwords of any local user account. This includes local device administrators, user portal accounts, and accounts used for remote access.
In response to the incident, Sophos began an immediate investigation trying to retrieve and analyze any data related to the attack and implementing temporary mitigation on all affected firewall versions. This measure eliminated the SQL vulnerability, limiting the scope of the attack. In addition, Sophos web application penetration testing experts issued a message for system administrators to identify whether their deployment has been compromised.
Scenario 1: Compromise-free implementation
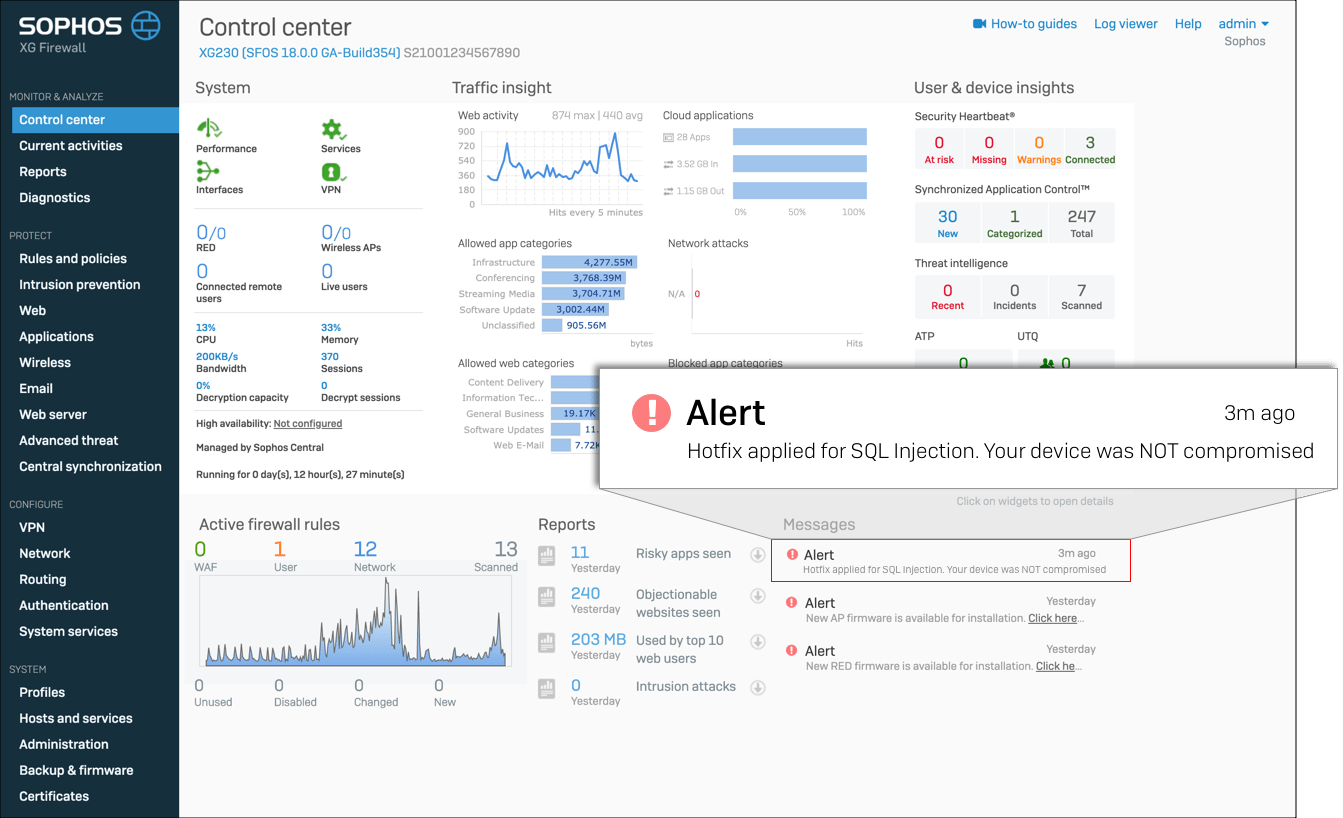
Scenario 2: Compromised implementation
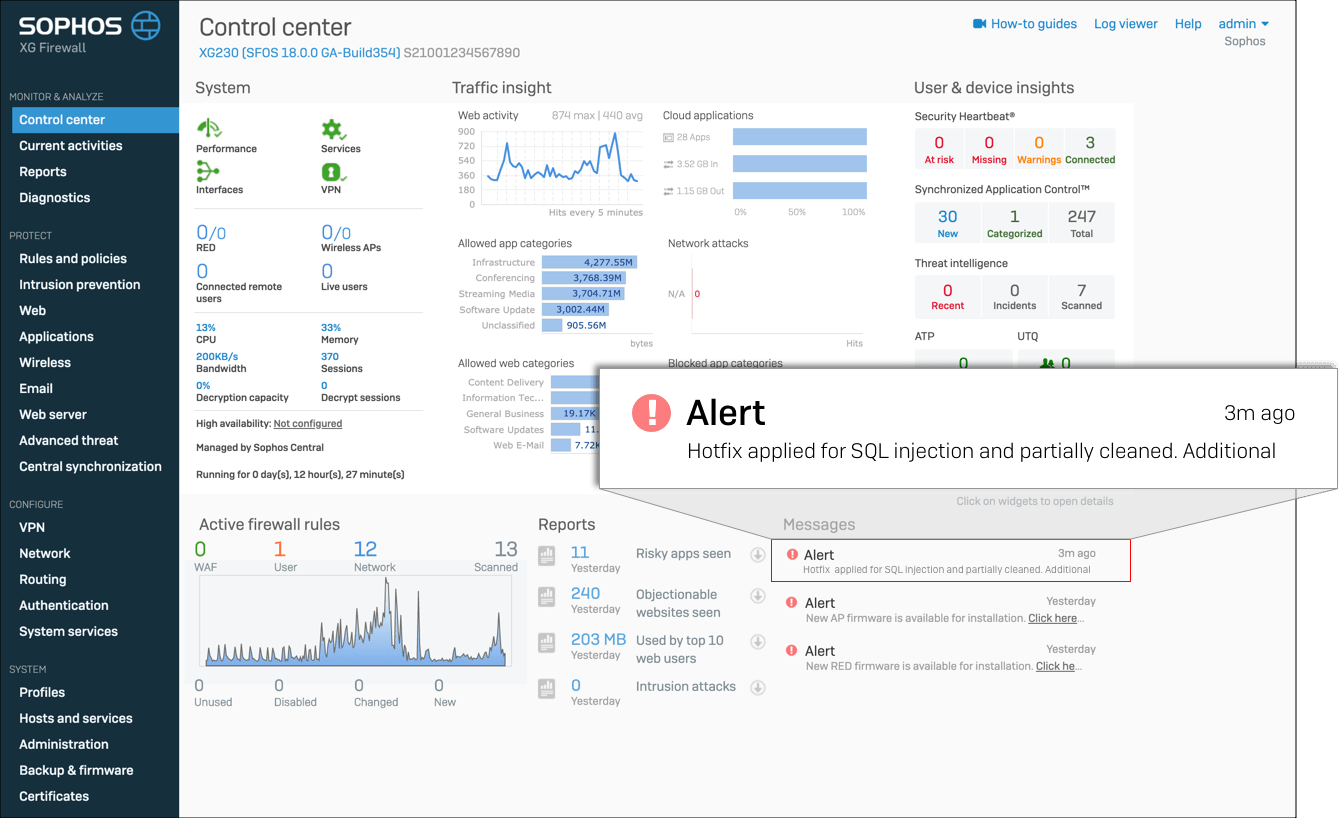
XG Firewall deployment administrators are not required to perform additional actions. On the other hand, administrators of attacked devices that have received emergency updates must perform the following steps to complete the remediation of this issue:
- Reset all device administrator accounts
- Restart affected devices
- Reset passwords for all local user accounts
- Although passwords are encrypted, it is recommended to reset them for any account where XG Firewall credentials may have been reused
The existence of any additional attacks is not yet unknown, however, it is recommended to implement the mitigation steps as soon as possible.
For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











